Inside this Article
 What has Anonymous accomplished in a Cyberwar with Russia?
The methods Anonymous has used against Russia have not only been highly disruptive and effective, they have also rewritten the rules of how a crowdsourced modern cyberwar is conducted. In addition to hacking and releasing Russian data, the group has also offered cyber security assistance to Ukraine such as penetration testing and finding vulnerabilities before Russia could exploit them. Anonymous also offered free training to new recruits on denial of service attacks and other hacktivist methods. This effectively allows anyone with a computer and an internet connection regardless of their technical skills to join in the cyber war. The initial call to action posted on Twitter transformed into a larger operation that spread far beyond the Russian government, companies, or organizations, and included an information campaign aimed at Russian citizens.
New Methods and Techniques that are hard to defend against include:
What has Anonymous accomplished in a Cyberwar with Russia?
The methods Anonymous has used against Russia have not only been highly disruptive and effective, they have also rewritten the rules of how a crowdsourced modern cyberwar is conducted. In addition to hacking and releasing Russian data, the group has also offered cyber security assistance to Ukraine such as penetration testing and finding vulnerabilities before Russia could exploit them. Anonymous also offered free training to new recruits on denial of service attacks and other hacktivist methods. This effectively allows anyone with a computer and an internet connection regardless of their technical skills to join in the cyber war. The initial call to action posted on Twitter transformed into a larger operation that spread far beyond the Russian government, companies, or organizations, and included an information campaign aimed at Russian citizens.
New Methods and Techniques that are hard to defend against include:- Hacking Printers – Russian censorship has blocked many inside the country from knowing the true scale of the war and Russian losses. Anonymous hacked printers across Russia and printed uncensored facts or anti-propaganda and pro-ukrainian messages. The group claims to have printed over 100,000 documents. This also includes barcode printers at grocery stores where prices were changed and product names were changed to anti-war or pro-Ukrainian slogans.
- Using Conti Ransomware Code – The Conti ransomware leaders pledged allegiance to Russia after the war and shortly after their data was leaked including their source code. Anonymous affiliate group Network Battalion 65 or NB65 hackers edited the source code and turned Conti’s Ransomware against Russia by encrypting data that users could no longer access. Analysis showed 66% of the code used to attack Russian assets matched Conti. Like traditional ransomware, victims could make a payment to have the data decrypted and regain access after paying a ransom that would reportedly go to Ukraine. In early May, NB65 dumped 7 million credit card numbers from QIWI, a leading provider of payment and financial services in Russia.
- Hijacking Russian Servers – They hacked Russian hosting servers and then used them to attack other Russian websites and services. Using Russian IP addresses would cause disruption and denial of service to sites that use the simple protection method of geo blocking IP addresses outside of Russia. This is effective and the owners of the hacked servers often have no idea their resources are being used to launch attacks on other servers.
- Hacking The News – The Russian government was so concerned with censorship about the war that they passed a “Fake News” law that punished individuals up to 15 years in prison for speaking out against the war if it was deemed to be against Russian interests. Multiple Anonymous affiliated groups launched an attack on Smart TVs, Internet streams, News sites, and television channels that showed images of the war or other news that bypassed Russian censors. Anonymous claimed on Twitter to have hacked Russian streaming services Wink and Ivi, and live broadcasts at the TV channels Russia 24, Channel One, and Moscow 24. Once hacked they showed banned images or information about the war.
- Attacking Exposed Data – Our research discovered that hackers were targeting exposed Russian databases and changing the names of records or inserting folders with names such as Glory to Ukraine, Putin Stop This War, Hacked by Ukraine, and many others. Records were also deleted both manually and in what appeared to be an attack similar to the MeowBot malicious script that served no other purpose but to wipe out data. Out of 100 databases we identified that 92 were compromised or had evidence that hackers had accessed and vandalized the records.
- Targeting companies who still do business in Russia – Sanctions and calls from western countries and customers were not enough to fully stop some companies from trying to stay in the Russian market. Profits are the backbone of any business and many companies have a long history of placing revenue over morals. Anonymous threatened to leak insider or sensitive business data and days later dumped 10GB of data belonging to Nestlé. This included emails, passwords, Nestlé business customers, etc.. The group successfully launched denial of service DDoS attacks on Auchan, Leroy Merlin, and Decathlon websites. The threat of cyberattacks combined with the uncertainty of the Russian market have added additional risks for western companies.
- RoboDial, SMS, and Email Spam – Almost everyone on earth has received some form of spam in the form of a phone call, text, or email message. These usually try to sell a service or scam victims out of money. Now this same technology has been used to bypass Russian censorship and inform citizens of news and messages they are forbidden to learn on state sponsored propaganda channels. Anonymous affiliated Squad303 claimed to have sent over 100 million messages to Russian devices.
- Holidays and important date Hacks – The psychological effects launching cyber attacks and hacks on key Russian holidays. On May 9th “Victory Day” Anonymous-related hacker group PuckArks claims they were responsible for hacking the Russian YouTube clone called Rutube with access codes breached or leaked. Anonymous hacked Russian Smart TV menus to show all channels and descriptions as anti-war messages during Russia’s parade. On June 8th, the radio station Kommersant FM was hacked to broadcast the Ukrainian national thehem and a sequence of Russian-language anti-war songs. On June 17th, hackers targeted the St Petersburg International Economic Forum’s computer network with a DDoS attack forcing Vladimir Putin to delay his keynote speech by nearly 2 hours. On June 28 (Constitution Day in Ukraine) the websites of Rosreestr and the Presidential Council for the Development of Civil Society and Human Rights (HRC) were hacked.
Rosreestr is Russia’s official Federal Service for State Registration of real estate and property. Their website displayed text that read “Russian citizens are in solidarity with the Ukrainian people in their struggle for independence and their own, Ukrainian-oriented legislative foundation”.
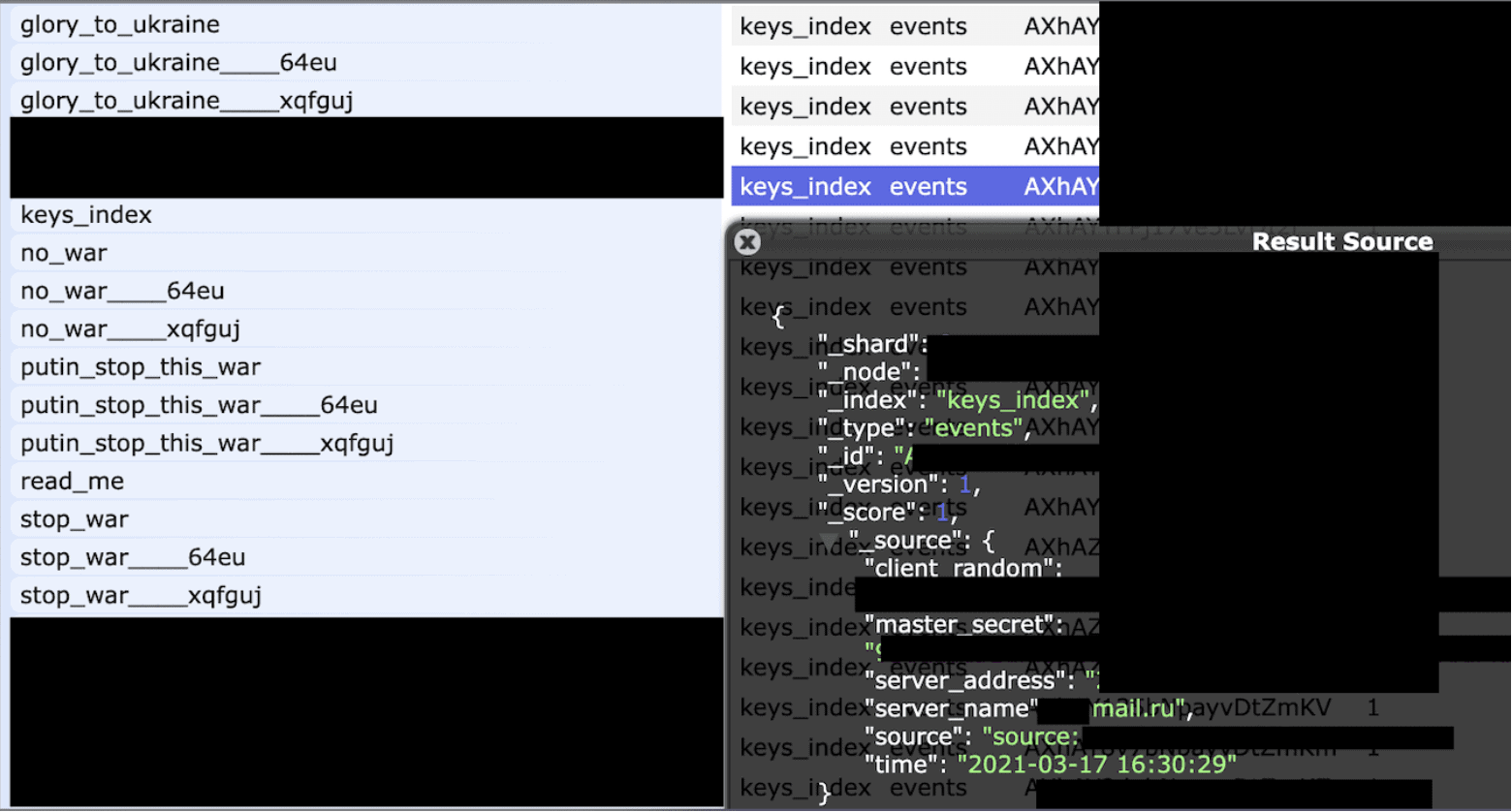 Example of a hacked database showing folders were renamed to antiwar names. The records also contained secret keys and other sensitive information that was accessible to hackers.
Example of a hacked database showing folders were renamed to antiwar names. The records also contained secret keys and other sensitive information that was accessible to hackers.
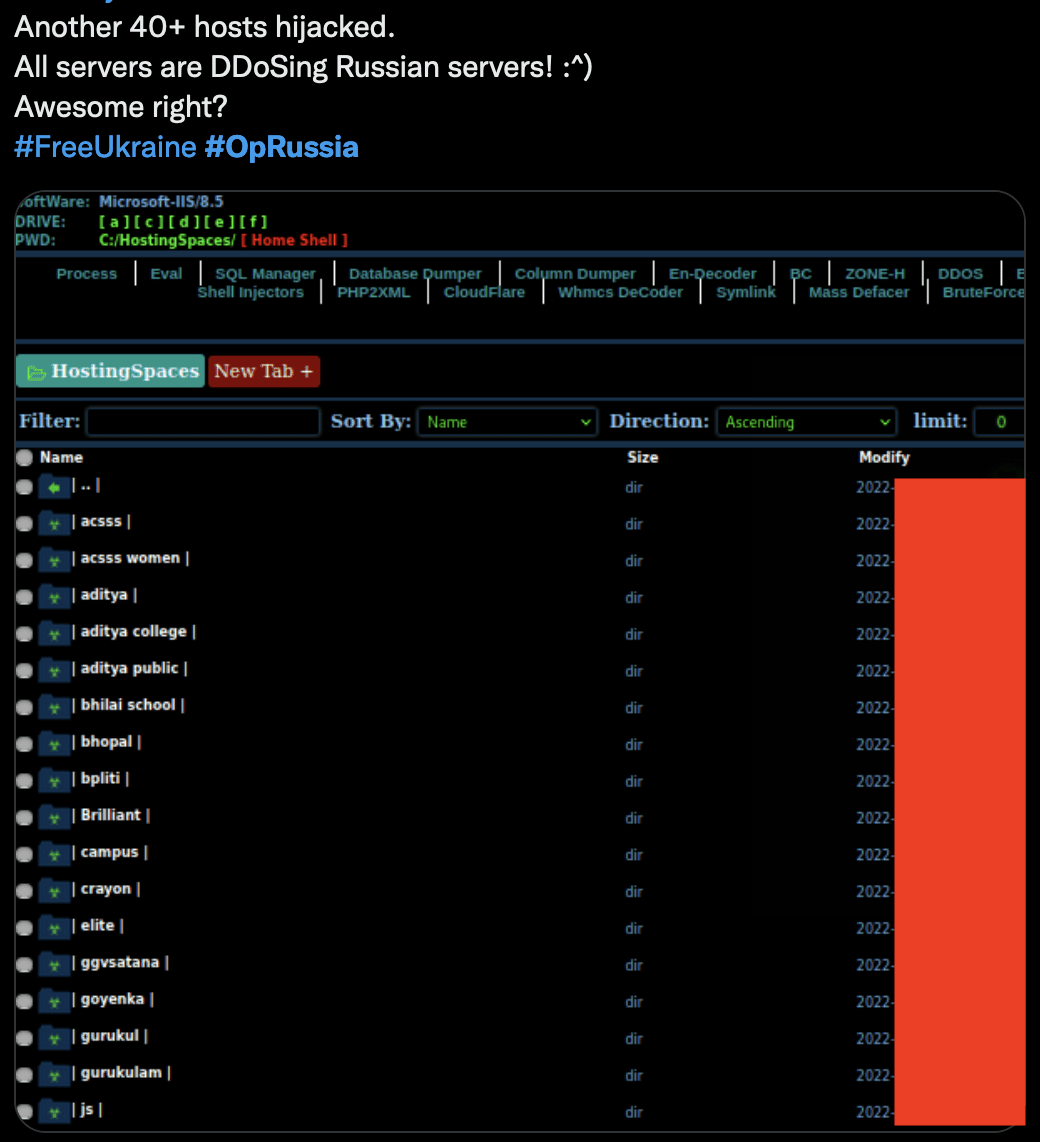 Example of compromised hosting servers that are launching DDoS attacks against Russian assets.
Example of compromised hosting servers that are launching DDoS attacks against Russian assets.
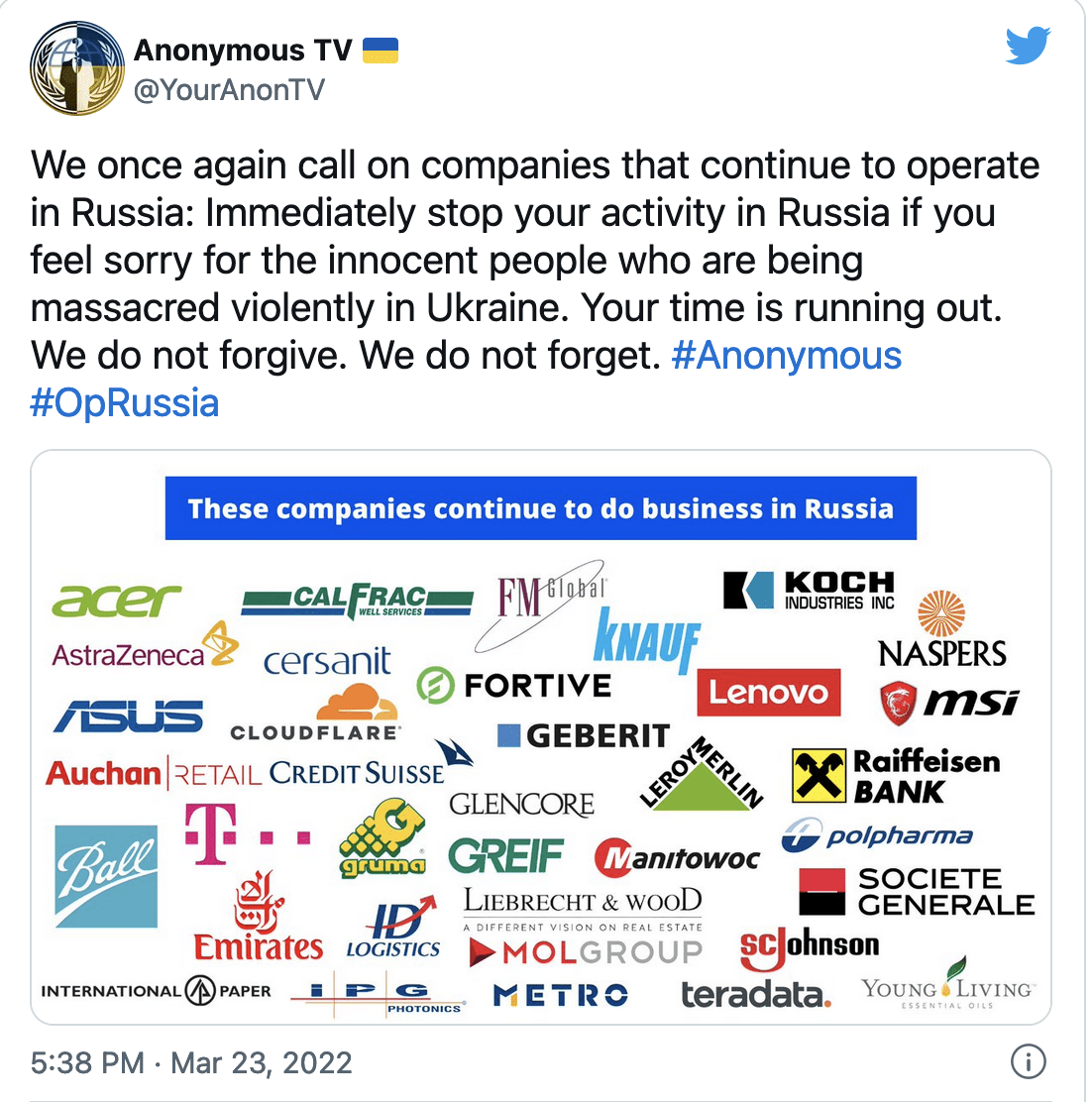 Example of the Twitter Threat sent as a warning to companies still doing business in Russia after the war in Ukraine.
Example of the Twitter Threat sent as a warning to companies still doing business in Russia after the war in Ukraine.
Hacktivism and Hacking is an Illegal Cybercrime
Digital information and technology has given us unrealistic expectations with instant gratification. We want results now and our smartphones have apps to shop, get a ride, date, or knowledge in a few clicks. The same logic applies to cyber activism except these individuals are breaking the law in many cases. People want instant vigilante justice and not to wait 20 years on an international court case that may never bring anyone to justice. One of the reasons people protest is because they lose faith in traditional institutions like tribunals or courts. Hacktivism allows average people to act in real time and be as destructive as they want and support a cause they believe in. This can be done from anywhere in the world and hackers can use technology to hide their location and identity from both the legal authorities and the victims they target. I am not condoning or promoting hacktivism. Cybercrime is considered an illegal activity where criminals use computers connected to the internet for a wide range of actions. These can range from espionage against a company or government, geopolitics, hacktivism, cyberwarfare and terrorism. The goals can range from a cyber protest to a large-scale criminal enterprise such as ransomware gangs who make millions of dollars every year, or state sponsored criminals who operate under the protection of their government. In the United States Federal cybercrime convictions could land someone a prison sentence of up to 20 years. In the European Union a hacker could be convicted for 2 years for illegally accessing information systems and at least 5 years for cyberattacks against critical infrastructure. Hacking is not only unethical, but is highly illegal and comes with substantial risk. With that being said, it is easy to see how and why Hacktivism is a successful tool to combine like minded people who share the same views across borders and countries to launch a multi-front attack against a cause they may disagree with? This could be a company that mistreats workers or a government that commits genocide or war. There are also those who would never be hackers or join Anonymous but are motivated by the emotional images seen on the news and social media. They are ready to temporarily suspend any moral or legal objections to attack the target for instant gratification. For the first time in modern history we see a war where average citizens from around the world use the internet and technology to attack, sabotage, or vandalize systems and data without crossing geographic borders. The interesting thing about Anonymous is that members can come and go or return based on the cause or issues they support. There is no central leadership structure, there is no President or CEO and groups launch actions under the umbrella of the Anonymous name. They are not connected with any specific country and this makes retaliation virtually impossible. The group has proven to be very capable in an all out assault against Russian assets. Without a doubt Anonymous has far exceeded expectations of what a loosely decentralized group of people from around the world could accomplish against a nation state. Russia has always projected the appearance and reputation that they possess a formidable cyber army and defense network. With the scale and success of the Anonymous cyber war, terabytes of data dumped to the public, thousands hacked websites, and more, we have to ask if Russia’s cyber defense capabilities were overestimated?Danger of Hacktivism
As a Security Researcher I often see login and admin information, secret keys, passwords, other account data, and much more exposed in open and unsecured databases. The difference between a Hacker and a Security Researcher is that despite knowing there is most likely a treasure trove of data just behind the locked door and the keys in our hands, we never circumvent passwords or credentials to access that data. Where hackers or cybercriminals do not follow the same rules or code of ethics. Hackers can use stolen data to launch additional attacks and commit more crimes in both the target and other networks. Using internal data they can break into associated accounts, transfer money, target individuals, and commit countless other forms of fraud. When a hacker has access to all of an organization’s data they can easily find information about other platforms, content management, customer information, etc. The hackers could also see out of date applications, middleware, versions, builds, other security flaws and unpatched vulnerabilities that could serve as a backdoor or deeper into the network infrastructure.This information would give the hackers multiple doors to open and attack vectors. Since my research I have watched closely the techniques and methods Anonymous has used. The hacks, disruption, data dumps, and scale have been unlike anything I have seen in the past. When a network of hackers is inside the target system they can pick and choose from many different attack vectors and ways to exploit the data based on their individual skill set. As a collective group or individually, they began a multi-tiered process to gain deeper access to systems and sensitive information. They can vandalize, encrypt data, or even delete millions of records including finding if there are connected backups and targeting those also. For example, if you have a group of people and some are good at brute force attacks, another who can launch malicious code injections, and others who can exploit software vulnerabilities. All of these skills combined will find a weakness and successfully “hack” that network and this is exactly what we have seen Anonymous do against Russia.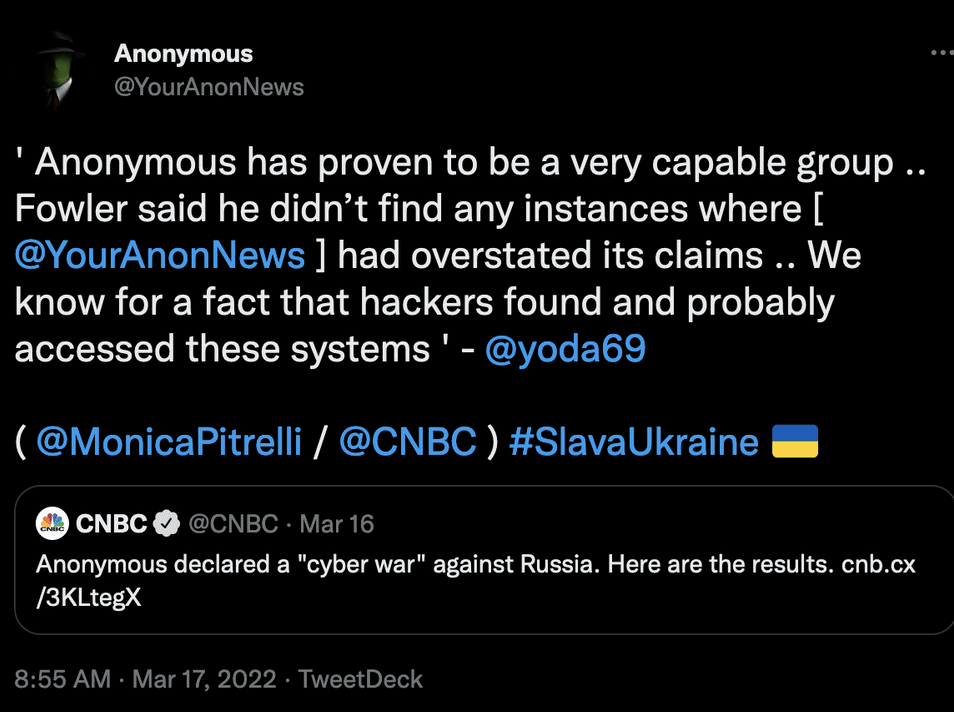 Tweet from Anonymous that quoted me and our research in the early days of the cyberwar.
Tweet from Anonymous that quoted me and our research in the early days of the cyberwar.
First Month Timeline and Key Data Dumps Since
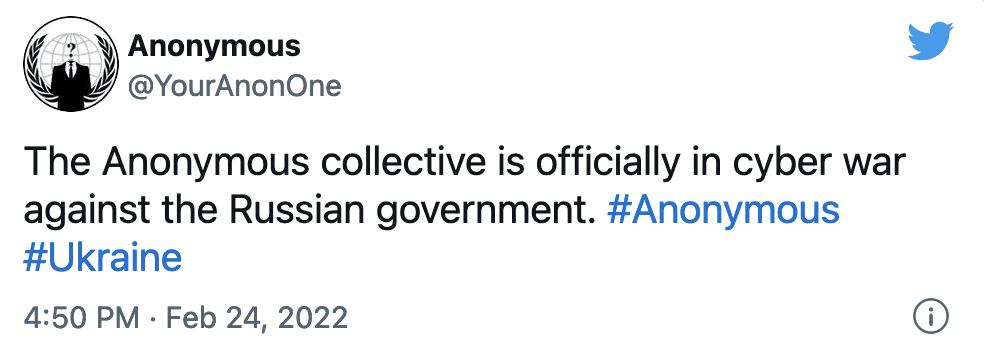
The Anonymous collective has claimed to have hacked over 2,500 Russian and Belarusian government, state media and other sites. There are likely many more attacks that are under the radar, not reported, or part of a longer term offensive. There are new data dumps being posted often that will provide researchers and foregin intelligence agencies with years of data to review. This data can identify secret deals, ownership of sanctioned companies, possible corruption and much more. Feb 24th – Anonymous declares a cyber war against Russia and calls for hackers to unite and target all things Russian including government websites, records, the media, stores, and more. Feb 28th – Anonymous hacked TV and news outlets then showing messages to Russian people that bypass censorship. March 4th – Anonymous hacked the Russian space research institute. Defaced the website and claimed to leak files from the Russian space agency Roscosmos. March 7th – Anonymous hacked Russian news and streaming sites and added Ukrainian war footage that is not shown on Russian state television. This was important because many Russians did not know the size and level of destruction of the conflict. They also did not know there were substantial Russian losses of personal and equipment. March 10th – Anonymous and affiliated groups accessed, vandalized, and deleted records of an estimated 90% of Russian exposed databases. Our detailed report of these findings was published and referenced. March 12th – Hackers accessed security cameras of Russian installations and what appears to be CCTV feeds from inside the Kremlin. Anonymous and affiliated groups sent over 7 million SMS text messages to Russian citizens about the war in Ukraine. March 15th – Anonymous launched a successful denial of service attacks against the Russian Federal Security Service and many other government agency websites. March 19th – Anonymous leaked the first major data dump containing 79GB of records belonging to Omega Company which is the in-house R&D unit of Transneft, the largest oil pipeline company in the world.Massive Amount of Data Dumped
Anonymous has hacked and publicly released millions of Records from Russian state agencies, state media outlets, private companies, and much more. Many of these records have been posted to DDoSSecrets and are available to anyone who wants to download and review the records. (Most documents are in the Russian language). Here are a few of the biggest data dumped since the start of the war over 3 months ago.- 1.1 million emails (1.1 TB) from ALET, a Russian customs broker for companies in the fuel and energy industries, handling exports and customs declarations for coal, crude oil, liquefied gas and petroleum products.
- Central Bank of Russia on March 26. Around 28gb of data was taken from the organization. This included data on transfers, clients, and supposed high-profile people who had been using the bank.
- Russian Army – Hackers released personal information of 120,000 Russian soldiers allegedly fighting in Ukraine. These records can be used to identify and investigate individuals suspected of crimes or killed in combat.
- 1.23 million emails (1.7 TB of data) from Elektrocentromontazh (ECM), the primary power organization of Russia. ECM designs, builds, installs and maintains electrical equipment in power generation and transmission facilities.
- Sawatzky (432 GB) – 575,000 emails from the Russian property management company.
- Gazregion (222 GB) – Emails and files from the Russian gas pipeline and facilities construction company
- Gazprom Linde Engineering (728 GB) – Anonymous released 768,000 emails from the joint venture between Gazprom and Linde.
- Technotec (440 GB) – Emails from an engineering and oil and gas production company
- Government Data: Ministry of Culture of the Russian Federation (446 GB); City administration of Blagoveshchensk (150 GB), and the Governor’s office of the Tver region (116 GB) lost hundreds of thousands of emails to hackers.
- VGTRK (786.2 GB) Twenty years worth of data from the Russian state broadcasting company.
- Russian Railway Staff Database. Including MD5 hashed emails and passwords, usernames, ID,account.
- Law Firm Rustam Kurmaev and Partners (RKP) 1TB of data. The firm has 455 clients including global corporations and banks. The records include internal files, emails, court files, client files, backups, and more.
- Russian IT company NPO VS (759 GB). The company manages IT infrastructure for the Russian Ministry of Defense and the Ministry of Internal Affairs. The records also included over 1 million emails.
- Denial of Service Attacks on The KGB of Belarus, Serbian Security Services and other “pro-Russian” assets outside of Russia.
- Anonymous collective leaked internal records of Putin’s political party called Rusnod. The records include IP, Names, Numbers, Addresses, Emails & passwords. The CSV document was shared on a Telegram channel.
- Hacked Russian Drones: Anonymous announced that operatives had hacked into a weapons company that handles the Russian Unmanned Aerial Vehicles (UAV) and the group had obtained classified tactics and plans. It is unclear who the group may have shared this information with. It is unlikely to be publicly dumped to prevent Russia from changing plans or tactics.
- The website of Russia’s Ministry of Construction, Housing and Utilities appeared to have been hacked, with an internet search for the site leading to a “Glory to Ukraine” sign in Ukrainian.
- Russian social media VK allegedly hacked. Users of VK have received messages from the social network’s official account informing them of the true casualties and actions of the Russian army’s attack against Ukraine.
- Nestlé business customer data leaked. Anonymous claims to have hacked a database belonging to the largest food company in the world. The records contained 10GB data of emails, passwords, and information of business customers.
- Russian Federal Air Transport Agency (Rosaviatsia). The attack erased all documents, files, aircraft registration data and mails from the servers. In total, about 65 terabytes of data was erased. The group claimed there were no connected backups. There are conflicting reports if this was conducted by the Anonymous hacktivist collective or another group. In an IBTimes article Anonymous claimed they would never endanger the lives of civilians.
- Russian Orthodox Church’s charitable wing was hacked and 15GB of data and roughly 57,500 emails were released.
- Marathon Group is an investment firm owned by Alexander Vinokurov who is currently under EU sanctions for “providing a substantial source of revenue to the Government of Russia.” Hackers released 62,000 emails. (Vinokurov is the son-in-law of Russian Foreign Minister Sergei Lavrov)
- Capital Legal Services Russian law firm. Anonymous hacked & released approximately 200,000 emails.
- Mosekspertiza, a state-owned company created by the Moscow Chamber of Commerce. The Anonymous-linked group ‘NB65’ hacked & released over 150,000 emails, 8,200 files.
How Big is Anonymous?
The short answer is no one really knows how many members Anonymous has. The Anonymous Twitter account @YourAnonNews has around 8 million followers, but it is unclear how many of these followers are active members and how many are just there to read the hacking collective’s news and updates. Back in 2015 there were an estimated 2,770 Anonymous Facebook pages that generated a collective 22.2 million “likes.” We can assume that the group is much bigger and globally connected now than ever before. The reason it is so hard to gauge this number and information is because they remain as the group’s name implies “Anonymous”. After the unprovoked war against Ukraine that has triggered the biggest refugee crisis since World War 2 it is estimated that over 5 million Ukrainians fled to Europe and millions more displaced internally. Russia’s heavy handed tactics against civilians and non-military infrastructure such as schools, hospitals, and apartment buildings appears to have motivated many to join Anonymous groups. Russia has effectively become the biggest recruiter for Anonymous and has inspired people who would never consider themselves a “hacker” or “hacktivist” to take action online.Ukraine’s Cyber Defense
In addition to the defense and offense Anonymous and hackers from around the globe have offered Ukraine, the country was actually highly skilled in technology and had experience in defending against Russian cyber attacks. Since 2014, Russia has used Ukraine as a testing ground for their cyber capabilities and even took their energy grid offline on two separate occasions. A Telegram channel called “IT Army of Ukraine” has over 310,000 digital volunteers. It is unknown the size and scale of Ukraine’s official cyber army but it is possible that many local programmers, coders and developers have joined the fight online. Ukraine’s digital transformation minister also called for volunteers to defend Ukraine in the cyber realm. Ukraine was one of the biggest outsourcing hubs for tech companies and had a robust startup culture and offered a very serious pool of talent from the technology sector. After the collapse of the Soviet Union in 1991 many traditional industries such as agriculture, pharmaceuticals, metal, etc were untouchable to average people. Young Ukrainians understood that technology and digital goods or services could flow freely across borders and slipped under the radar. Covid prepared the world to accept remote work and now many Ukrainians are balancing remote tech work and fighting a war.Hacker vs Hacker
The Russian hacker group Killnet is suspected to be state sponsored by the Russian government and not just aligned or pro-Russian. On May 16th Killnet threatened cyber attacks on western governments including the US, UK, Germany, Italy, Latvia, Romania, Lithuania, Estonia, Poland and Ukraine. Killnet also launched unsuccessful DDoS attacks against Italy during the Eurovision song contest where Ukraine won the competition and rights to host the program in 2023. The Killnet group also targeted the Italian Senate’s website, National Health Institute, several airport sites, and others. In return, Anonymous Italia led the call for a coordinated strike on Killnet that would involve the full force of Anonymous’ global members. The collective declared they would launch the biggest attack in the group’s history against Killnet on the night of May 21st. Within a matter of hours the Killnet.ru website was offline and “parked” and Anonymous posted screenshots of Killnet’s internal records, member photos, member names, emails, passwords and other personal information.Why has Russia Not Retaliated or Launched a Cyber War Against the West?
Russia has a long history of using cyber attacks for espionage, spreading disinformation, and the disruption of governments and key infrastructure. In previous conflicts Russia launched cyber attacks before and during any invasion. According to a report by Microsoft in 2021, Russian security services were already preparing for a military incursion and were likely trying to or had already accessed Ukrainian information and technology systems including energy and other critical service providers. Just before the war, Ukrainian government systems were hit with multiple variants of the malicious malware called “wiper” that deleted data and programs. Ukrainian banks were hit with denial of service attacks (DDoS) and websites were hacked with warnings in Ukrainian to expect the worst and that all of their data was taken. Example of hacked Ukrainian website message warning that data was taken.
Russia has used Ukraine and other former Soviet Republics as a Sandbox to test their cyberwarfare capabilities. The Russian government understands that attacking critical infrastructure, power and communications can have a big effect on their target nation but with unprecedented sanctions and countries pouring support to Ukraine, why has there been no major attacks on Western banks or infrastructure?
We can only speculate the reason why Russia has not responded or launched a cyber campaign against NATO members or western countries who have imposed sanctions that Russia has considered an “economic war”. As security researchers our goal is to highlight the cyber security implications of the conflict and not be involved in geopolitics. The real question is, have we overestimated Russia’s cyber capabilities or was this a strategic decision to not retaliate? It is possible that Russia understands that a cyber operation could trigger Article 5 of the NATO treaty, which states that an attack on one member nation is considered an attack on them all.
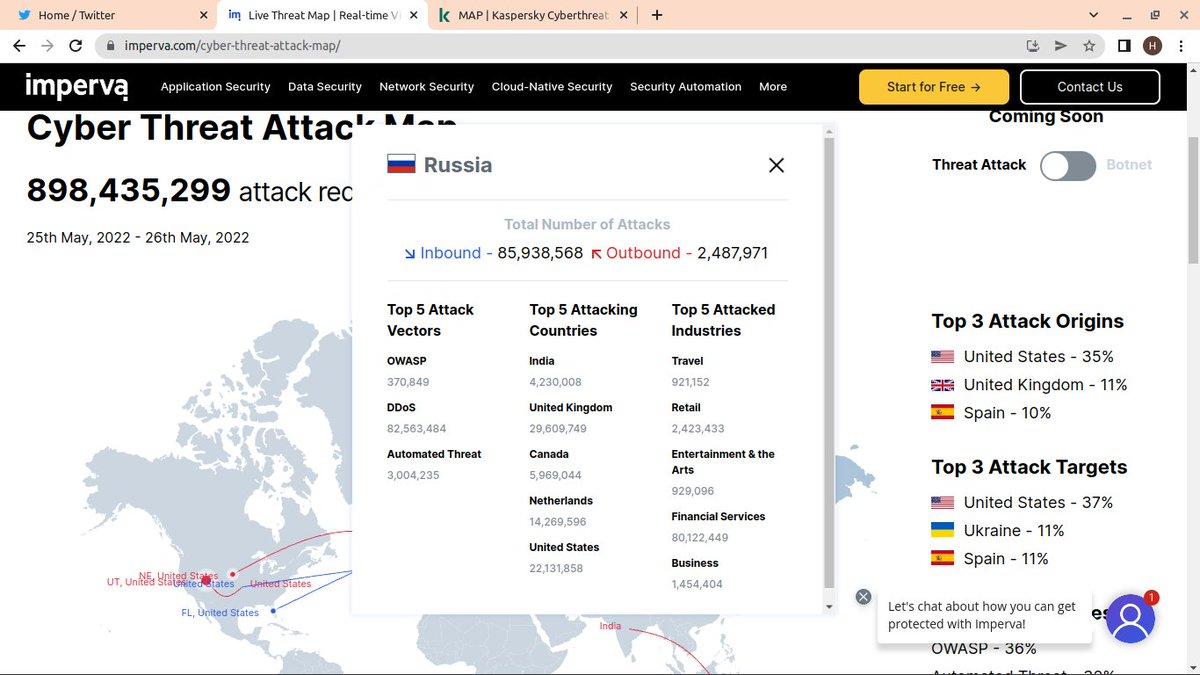
After Russia’s invasion of Ukraine many of us in the cyber security industry expected massive cyberattacks and damage or disruption to global computer networks. Although this has not happened yet, the conflict is unfortunately far from over. Cyber-attacks on Russia have increased by 55% compared to last Friday with nearly 86 million attacks, while attacks from Russia have increased by 8%.
Example of hacked Ukrainian website message warning that data was taken.
Russia has used Ukraine and other former Soviet Republics as a Sandbox to test their cyberwarfare capabilities. The Russian government understands that attacking critical infrastructure, power and communications can have a big effect on their target nation but with unprecedented sanctions and countries pouring support to Ukraine, why has there been no major attacks on Western banks or infrastructure?
We can only speculate the reason why Russia has not responded or launched a cyber campaign against NATO members or western countries who have imposed sanctions that Russia has considered an “economic war”. As security researchers our goal is to highlight the cyber security implications of the conflict and not be involved in geopolitics. The real question is, have we overestimated Russia’s cyber capabilities or was this a strategic decision to not retaliate? It is possible that Russia understands that a cyber operation could trigger Article 5 of the NATO treaty, which states that an attack on one member nation is considered an attack on them all.
After Russia’s invasion of Ukraine many of us in the cyber security industry expected massive cyberattacks and damage or disruption to global computer networks. Although this has not happened yet, the conflict is unfortunately far from over. Cyber-attacks on Russia have increased by 55% compared to last Friday with nearly 86 million attacks, while attacks from Russia have increased by 8%.