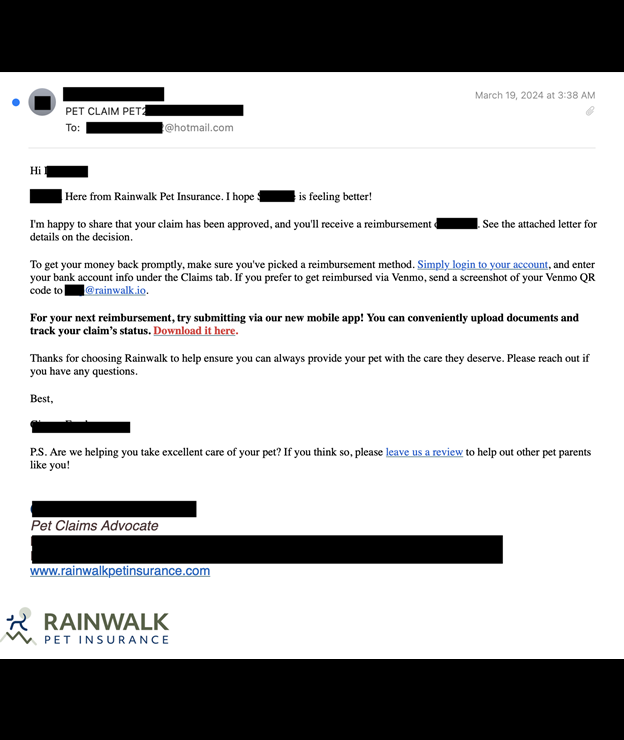
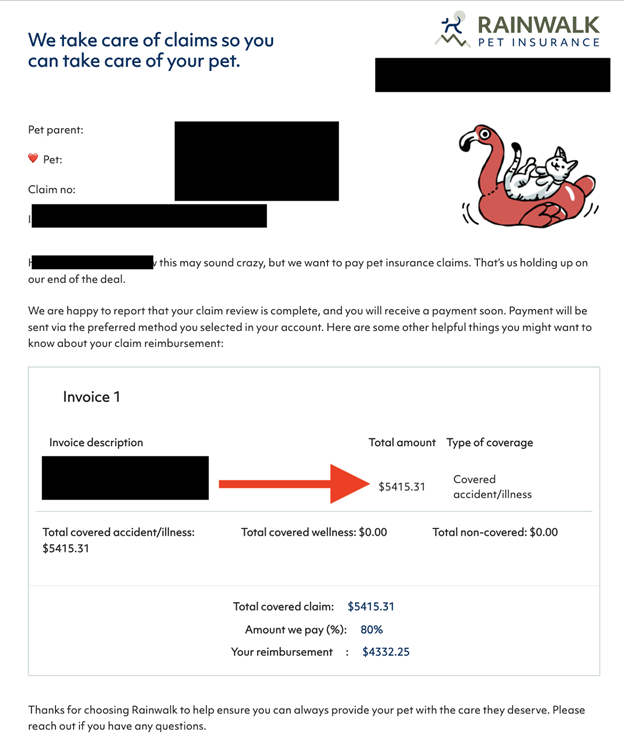
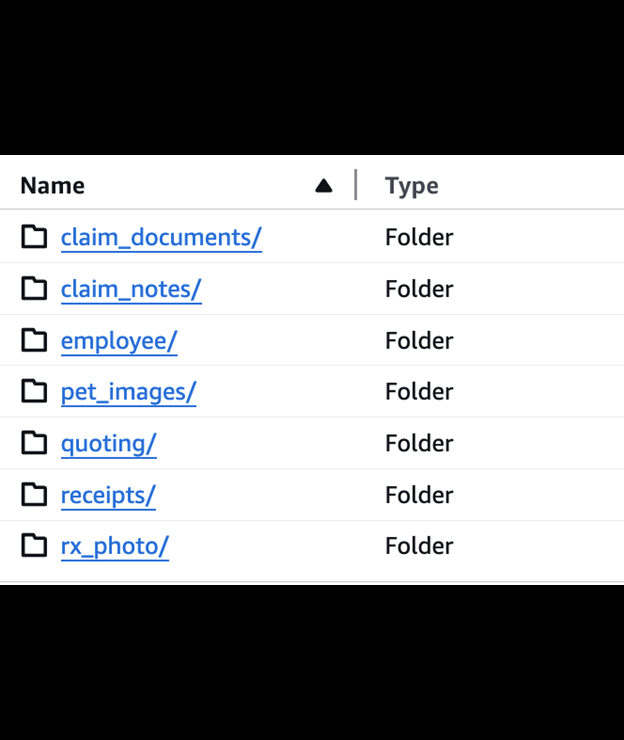
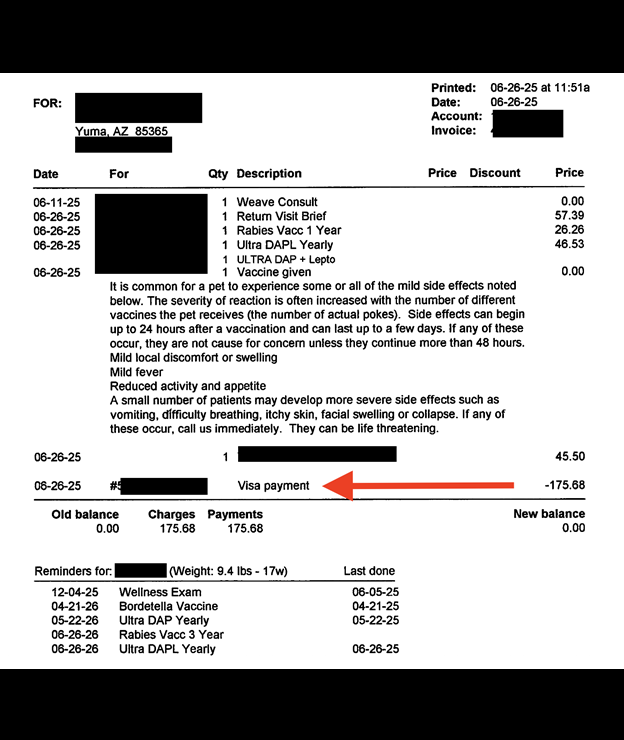
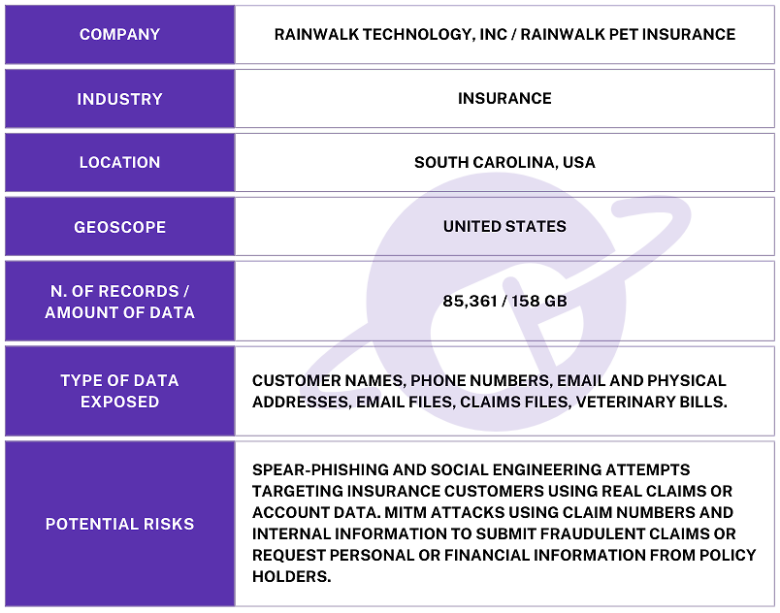
 The publicly exposed database was not password-protected or encrypted. It contained 85,361 files totaling 158 GB. In a limited sampling of the exposed files, I saw documents — including invoices, claims, and email communications — containing pet owner or policy holder names, physical addresses, email addresses, phone numbers, and other identifiable information. Many documents also included pet names, age, medical histories, breed, microchip numbers, and other information. Some veterinary invoice documents contained partial credit card numbers.
The name of the database along with information from its internal files suggests the records belong to South Carolina-based Rainwalk Technology, which provides pet insurance. I immediately sent a responsible disclosure notice to Rainwalk, and the database remained open for nearly a month before it was restricted from public access and no longer accessible.
I did not receive any reply to my responsible disclosure notice. Although the records appeared to belong to Rainwalk, it is not known if the database was owned and managed directly by them or by a third-party contractor. It is also not known how long the database was exposed before I discovered it or if anyone else may have gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity.
According to a report by The North American Pet Health Insurance Association (NAPHIA), it is estimated that 7.03 million pets were insured in North America at the end of 2024. This represents a 12.2% increase from the 6.25 million total pets insured in 2023, amounting to nearly $5.2 billion in gross written premiums.
In the U.S., there are no direct privacy protections for pet data, since laws like HIPAA only apply to human health records. However, when pet information is combined with owner details (such as names, addresses, emails, and other PII), it could pose significant potential privacy risks. Although pet related data may seem harmless on its own, when it is linked with human PII, it could hypothetically provide malicious actors with highly valuable targets for both digital and real-world threat scenarios.
According to the most recent Verizon data breach investigations report, an estimated 97% of cybercrimes are committed for financial gain. Like human medical bills, veterinary care can add up to many thousands of dollars — which means the possibility of criminals gaining access to open claims and reimbursement data poses significant potential financial risks for insurance providers.
I saw numerous emails indicating that customers can receive Venmo payments by emailing their QR code to Rainwalk, which could create reimbursement-related security risks. These emails also included the claim number, name of the account holder, pet’s name, and monetary amounts. Hypothetically, this would be enough information to launch a man in the middle attack (MITM). By using real claim data, malicious actors in theory could submit fraudulent claims using real account data. They could also replace the QR code with their own payment information, collecting real clients’ reimbursements for themselves.
Additionally, customers could potentially be targeted with the exposed information. Criminals could send them fraudulent invoices (modeled after real ones) or use real policy data to trick them into revealing more sensitive information. For instance, criminals could contact customers, claim to be affiliated with an insurer or clinic, and request additional personal information or payment details. The customer would have little reason to suspect these requests are not legitimate because criminals could hypothetically reference dates, amounts, claims numbers, and other information that only the care providers, insurance company, and pet parent would know. I am not claiming that Rainwalk customers are at risk of these types of threats, I am only providing hypothetical risk scenarios for educational purposes.
The exposure of microchip numbers also poses potential risks. Pet microchips are small RFID devices implanted under a pet’s skin. They carry a unique identification number that links the owner’s contact information in a registry, which can help identify lost or stolen pets. While the microchips don’t store personal data directly or enable GPS tracking, the microchip number itself can still be exploited for scams if exposed.
According to a report published by HackRead, thousands of pet owners have reported receiving emails claiming their pet’s microchip registration is expiring. The email urges them to pay a fraudulent renewal fee through scam websites. These microchip renewal scams target pet owners by exploiting their concern for their animals’ safety, falsely claiming a pet’s microchip must be renewed immediately. In reality, microchips never actually expire, but most pet owners do not know this. I am not claiming that Rainwalk’s customers are at risk of microchip renewal scams; I am only describing how such scams operate for information and awareness purposes.
As a cybersecurity researcher, my advice to pet insurance companies and veterinary medicine providers that collect and store data containing PII is to adopt a security strategy that treats all pet and owner data as if it were sensitive information. Encrypting documents is a basic first step that makes documents non-human readable and much more difficult to decrypt if they are ever exposed. Implementing access controls with multifactor authentication and reviewing permissions configurations can help prevent unauthorized access or accidental data exposures. It is also a good idea to conduct regular penetration testing, audit for misconfigurations, and use monitoring tools to detect and block unauthorized public access to storage buckets or databases.
For pet owners who suspect their data may have been exposed, it is important to beware of the potential risks of unsolicited communications that reference pets. Any dubious requests, surprise invoices, or unfamiliar individuals asking for personal details related to pets should raise suspicion. Always verify that the person getting in touch with you is who they claim they are. Only communicate with insurance providers and veterinary hospitals using official channels.
Remember that malicious actors could exploit the emotional bond between owners and their animals and use real data to make fraudulent attempts appear legitimate. As a standard practice, I advise to never click on links, download attachments, or provide payment or personal details without verifying the request first. Users or customers should always report suspicious requests to the relevant company so they can identify potential issues and help protect customer information, issue warnings, or notify relevant authorities.
I imply no wrongdoing by Rainwalk Technology, Inc, or its employees, agents, contractors, affiliates, and/or related entities. I do not claim that any internal, employee, customer, or user data was ever at imminent risk. The hypothetical data-risk scenarios I have presented in this report are strictly and exclusively for educational purposes and do not reflect, suggest, or imply any actual compromise of data integrity. It should not be construed as a reflection of or commentary on any particular organization’s specific practices, systems, or security measures.
As an ethical security researcher, I do not download, retain, or share any data I discover. I only take a limited number of screenshots strictly when necessary and solely for verification and documentation purposes. I do not engage in any activities beyond identifying the security vulnerability and, where possible, notifying the relevant parties involved. I disclaim any and all liability from the use, interpretation, or reliance on this disclosure. I publish my findings to raise awareness of issues of data security and privacy. My aim is to encourage organizations to proactively implement measures to safeguard sensitive information against unauthorized access.
The publicly exposed database was not password-protected or encrypted. It contained 85,361 files totaling 158 GB. In a limited sampling of the exposed files, I saw documents — including invoices, claims, and email communications — containing pet owner or policy holder names, physical addresses, email addresses, phone numbers, and other identifiable information. Many documents also included pet names, age, medical histories, breed, microchip numbers, and other information. Some veterinary invoice documents contained partial credit card numbers.
The name of the database along with information from its internal files suggests the records belong to South Carolina-based Rainwalk Technology, which provides pet insurance. I immediately sent a responsible disclosure notice to Rainwalk, and the database remained open for nearly a month before it was restricted from public access and no longer accessible.
I did not receive any reply to my responsible disclosure notice. Although the records appeared to belong to Rainwalk, it is not known if the database was owned and managed directly by them or by a third-party contractor. It is also not known how long the database was exposed before I discovered it or if anyone else may have gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity.
According to a report by The North American Pet Health Insurance Association (NAPHIA), it is estimated that 7.03 million pets were insured in North America at the end of 2024. This represents a 12.2% increase from the 6.25 million total pets insured in 2023, amounting to nearly $5.2 billion in gross written premiums.
In the U.S., there are no direct privacy protections for pet data, since laws like HIPAA only apply to human health records. However, when pet information is combined with owner details (such as names, addresses, emails, and other PII), it could pose significant potential privacy risks. Although pet related data may seem harmless on its own, when it is linked with human PII, it could hypothetically provide malicious actors with highly valuable targets for both digital and real-world threat scenarios.
According to the most recent Verizon data breach investigations report, an estimated 97% of cybercrimes are committed for financial gain. Like human medical bills, veterinary care can add up to many thousands of dollars — which means the possibility of criminals gaining access to open claims and reimbursement data poses significant potential financial risks for insurance providers.
I saw numerous emails indicating that customers can receive Venmo payments by emailing their QR code to Rainwalk, which could create reimbursement-related security risks. These emails also included the claim number, name of the account holder, pet’s name, and monetary amounts. Hypothetically, this would be enough information to launch a man in the middle attack (MITM). By using real claim data, malicious actors in theory could submit fraudulent claims using real account data. They could also replace the QR code with their own payment information, collecting real clients’ reimbursements for themselves.
Additionally, customers could potentially be targeted with the exposed information. Criminals could send them fraudulent invoices (modeled after real ones) or use real policy data to trick them into revealing more sensitive information. For instance, criminals could contact customers, claim to be affiliated with an insurer or clinic, and request additional personal information or payment details. The customer would have little reason to suspect these requests are not legitimate because criminals could hypothetically reference dates, amounts, claims numbers, and other information that only the care providers, insurance company, and pet parent would know. I am not claiming that Rainwalk customers are at risk of these types of threats, I am only providing hypothetical risk scenarios for educational purposes.
The exposure of microchip numbers also poses potential risks. Pet microchips are small RFID devices implanted under a pet’s skin. They carry a unique identification number that links the owner’s contact information in a registry, which can help identify lost or stolen pets. While the microchips don’t store personal data directly or enable GPS tracking, the microchip number itself can still be exploited for scams if exposed.
According to a report published by HackRead, thousands of pet owners have reported receiving emails claiming their pet’s microchip registration is expiring. The email urges them to pay a fraudulent renewal fee through scam websites. These microchip renewal scams target pet owners by exploiting their concern for their animals’ safety, falsely claiming a pet’s microchip must be renewed immediately. In reality, microchips never actually expire, but most pet owners do not know this. I am not claiming that Rainwalk’s customers are at risk of microchip renewal scams; I am only describing how such scams operate for information and awareness purposes.
As a cybersecurity researcher, my advice to pet insurance companies and veterinary medicine providers that collect and store data containing PII is to adopt a security strategy that treats all pet and owner data as if it were sensitive information. Encrypting documents is a basic first step that makes documents non-human readable and much more difficult to decrypt if they are ever exposed. Implementing access controls with multifactor authentication and reviewing permissions configurations can help prevent unauthorized access or accidental data exposures. It is also a good idea to conduct regular penetration testing, audit for misconfigurations, and use monitoring tools to detect and block unauthorized public access to storage buckets or databases.
For pet owners who suspect their data may have been exposed, it is important to beware of the potential risks of unsolicited communications that reference pets. Any dubious requests, surprise invoices, or unfamiliar individuals asking for personal details related to pets should raise suspicion. Always verify that the person getting in touch with you is who they claim they are. Only communicate with insurance providers and veterinary hospitals using official channels.
Remember that malicious actors could exploit the emotional bond between owners and their animals and use real data to make fraudulent attempts appear legitimate. As a standard practice, I advise to never click on links, download attachments, or provide payment or personal details without verifying the request first. Users or customers should always report suspicious requests to the relevant company so they can identify potential issues and help protect customer information, issue warnings, or notify relevant authorities.
I imply no wrongdoing by Rainwalk Technology, Inc, or its employees, agents, contractors, affiliates, and/or related entities. I do not claim that any internal, employee, customer, or user data was ever at imminent risk. The hypothetical data-risk scenarios I have presented in this report are strictly and exclusively for educational purposes and do not reflect, suggest, or imply any actual compromise of data integrity. It should not be construed as a reflection of or commentary on any particular organization’s specific practices, systems, or security measures.
As an ethical security researcher, I do not download, retain, or share any data I discover. I only take a limited number of screenshots strictly when necessary and solely for verification and documentation purposes. I do not engage in any activities beyond identifying the security vulnerability and, where possible, notifying the relevant parties involved. I disclaim any and all liability from the use, interpretation, or reliance on this disclosure. I publish my findings to raise awareness of issues of data security and privacy. My aim is to encourage organizations to proactively implement measures to safeguard sensitive information against unauthorized access.
Website Planet’s Recent Publications
At Website Planet we work with an experienced team of ethical security research experts who uncover and disclose serious data leaks. Recently, cybersecurity expert Jeremiah Fowler discovered and disclosed a non-password protected database that contained 5.1 million files totaling 10 TB apparently belonging to ClaimPix.He also found another unsecured database containing 145,000 files contained within 23 GB of data apparently belonging to Archer Health, Inc.