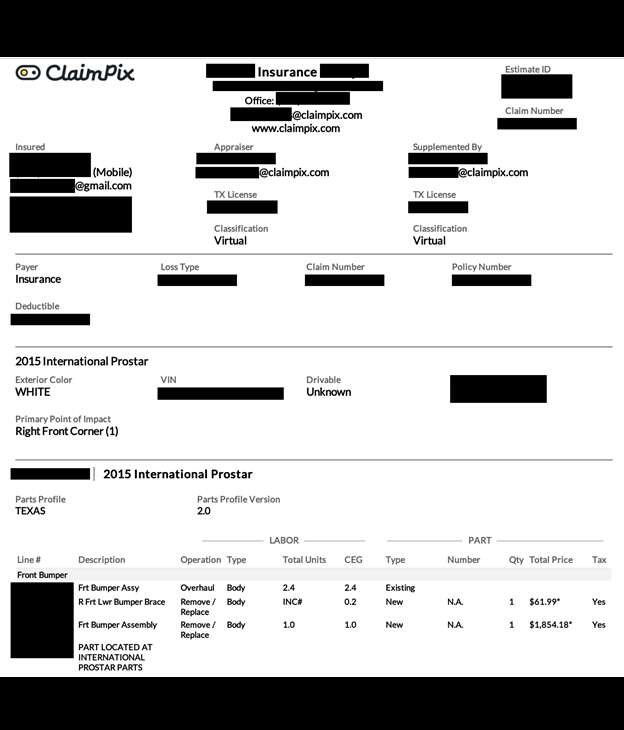
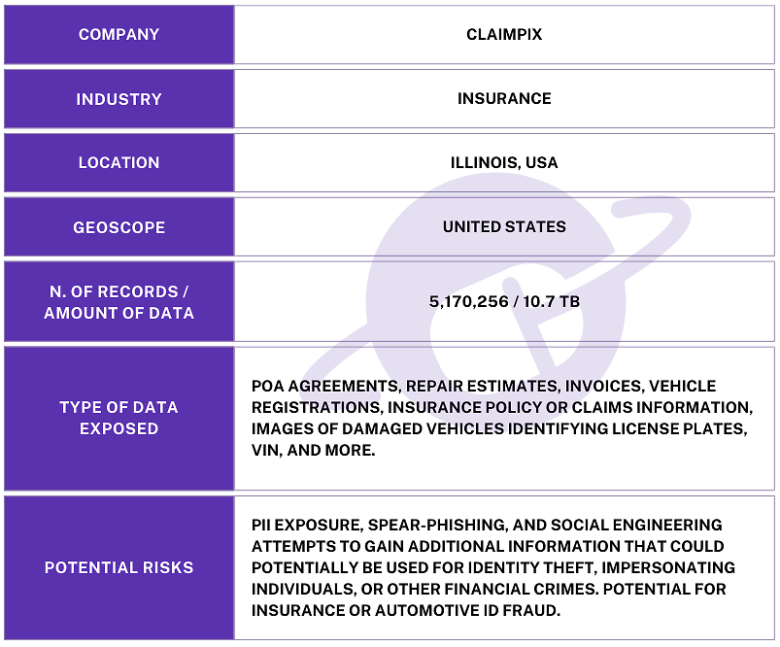
 The publicly exposed database was not password-protected or encrypted. It contained 5,170,256 files and images. In a limited sampling of the exposed files, I saw insurance documents that contained names, physical addresses, phone numbers, and emails. I also saw registration documents that contained PII and additional details about the vehicle (including VIN number, year, make, model, and more).
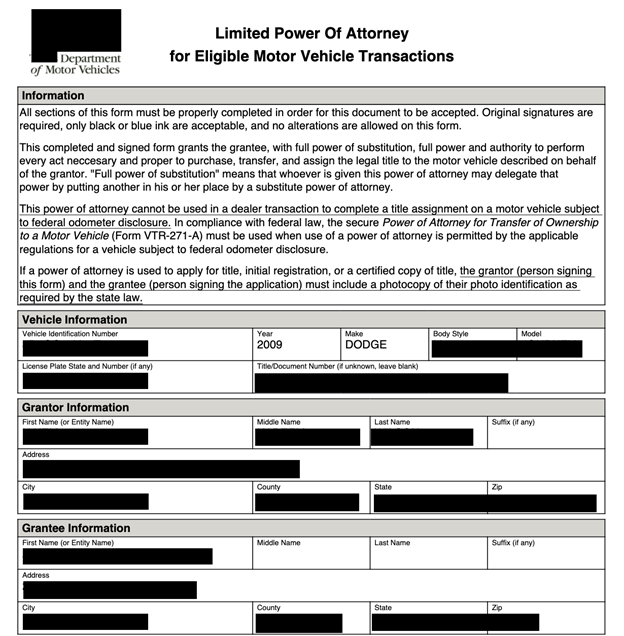
The database also contained just under 16,000 powers of attorney documents, which bestow the named grantee the legal authority to purchase, transfer, and assign title for the specific motor vehicle on behalf of the owner. Alternatively, they could delegate that authority to someone else to apply for a title, registration, or certified copy of the title. These documents were signed electronically and included the IP addresses of the individuals who signed them. Additionally, the database contained internal documents, such as software license agreements, indicating the terms, fees, and other information that should not be publicly exposed.
Information inside the database (and the name of the database itself) indicated the records belonged to Illinois-based ClaimPix, a platform for managing and filing auto insurance claims. I immediately sent a responsible disclosure notice to ClaimPix, and the database was restricted from public access shortly after and was no longer accessible. Although the records appeared to belong to ClaimPix, it is not known if the database was owned and managed directly by them or by a third-party contractor. It is also not known how long the database was exposed before I discovered it or if anyone else may have gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity.
I received the following reply to my responsible disclosure notice: “Thank you for alerting us to the security issues that you mentioned. We have investigated and confirmed your findings. We wanted to respond to you with a plan after we had time to identify the issue and also begin steps to remediate it. We have updated policies and our code to address this issue and will be making those changes live later this evening.”
According to their website, ClaimPix is used in the insurance claims process, vehicle transportation for damage inspections, and bill of lading receipts by companies across the entire United States. Users send customers a white‑labeled link via the ClaimPix portal where customers then take and upload required photos (such as vehicle damage, license plate, VIN, proof of coverage documents, etc.) using their mobile devices.
The process of filing insurance claims requires a range of documents that contain identifiable information that is not intended to be public. The exposure of personal data, insurance information, and even identification documents pose numerous potential risks both online and offline. In 2024, it was reported that the FTC received over 1.1 million identity theft reports and an estimated 2.6 million cases of related fraud. Exposed powers of attorney could potentially allow criminals to impersonate agents or representatives and attempt to initiate fraudulent sales, transfer property ownership or registration — all without the legitimate owner’s knowledge and consent.
Criminals could use information such as VIN numbers, license plates, and personal information to impersonate the owner, clone vehicles, or forge title and ownership documents. Cloning a vehicle (or VIN cloning) is a growing threat. It is basically identity theft for automobiles, where information is taken from a real, legally registered vehicle and then used to illegally register a stolen or salvaged car of a similar year, make, and model.
Although I was unable to find recent data on VIN cloning in the US, a 2025 report by Carfax Canada estimates that there could be over 372,000 potentially cloned VINs in Canada. The fact that, in 2022, Canada had 26.3 million registered vehicles while the US had approximately 285 million suggests that the overall scale of registered vehicles may make the risks of VIN cloning substantially higher in the United States. I am not saying that ClaimPix users or customers are or have been at risk of any form of fraud or scams, I am only providing a real-world scenario on how malicious actors could potentially misuse this type of information for educational purposes.
Another concern is the potential risk of insurance fraud by exploiting stolen or compromised data such as policy numbers, claim numbers, and PII. This type of fraud could happen to both insurers and policy holders. As a hypothetical example, if criminals gained access to an active claim that is being processed, and they knew that there was a deductible that must be paid to repair the claimant’s vehicle, they could attempt to fraudulently collect that payment directly from the policy holder.
On the other hand, for insurance companies, one common threat is criminals impersonating policyholders to file fraudulent claims using real information of their insurance policy, personal, and vehicle data. They could also use man-in-the-middle tactics to alter legitimate claims, increasing payouts and redirecting settlement or repair funds to their own accounts.
Another more creative approach criminals could potentially take would be to create a new, fake identity by combining real information from multiple people. They could then use this fake ID to apply for insurance policies and make fraudulent claims at a later date. I am not saying that ClaimPix’s users are at risk of these types of fraud, identity theft or impersonation. I am only identifying hypothetical risks based on documented methods that criminals have used in the past for the purposes of data protection and security awareness.
My advice to companies in the insurance industry is to encrypt all sensitive data so that, in the event of a data incident, the data is far more secure than in plain text documents. It is also important to enforce access controls with multi-factor authentication. Role-based permissions can also ensure that potentially sensitive data is only accessed by authorized individuals within the organization. This includes regular audits of cloud storage systems to ensure they restrict public access. Regular vulnerability testing, monitoring, and anomaly detection can increase the chances of identifying suspicious activity early.
For individuals who believe they may have had their personal or insurance information exposed in any data breach, it is important to act fast — especially if you notice any suspicious activity such as unexpected bills or unsolicited requests for more information. If there is unauthorized use of your identity, the major credit bureaus (Experian, Equifax, TransUnion) have systems that can place a fraud alert or credit freeze on your credit profile. This can stop criminals from creating new accounts and, if caught early, limit the damage and begin the road to recovery.
It is important to check credit reports and insurance statements periodically to identify suspicious activity or unknown accounts. There are a number of companies that offer identity theft monitoring for a monthly or yearly fee. Additionally, the FTC’s IdentityTheft.gov offers the ability to report cases of identity theft and provides helpful information for recovering from it. I am not claiming that there is any imminent threat from this data exposure. I am only providing this information for educational purposes, to exemplify what individuals can do to protect themselves in the event their data is compromised and exploited in any type of data breach.
I imply no wrongdoing by ClaimPix, or its employees, agents, contractors, affiliates, and/or related entities. I do not claim that any internal, employee, customer, or user data was ever at imminent risk. The hypothetical data-risk scenarios I have presented in this report are strictly and exclusively for educational purposes and do not reflect, suggest, or imply any actual compromise of data integrity. It should not be construed as a reflection of or commentary on any particular organization’s specific practices, systems, or security measures.
As an ethical security researcher, I do not download, retain, or share any data I discover. I only take a limited number of screenshots strictly when necessary and solely for verification and documentation purposes. I do not engage in any activities beyond identifying the security vulnerability and, where possible, notifying the relevant parties involved. I disclaim any and all liability from the use, interpretation, or reliance on this disclosure. I publish my findings to raise awareness of issues of data security and privacy. My aim is to encourage organizations to proactively implement measures to safeguard sensitive information against unauthorized access.
The publicly exposed database was not password-protected or encrypted. It contained 5,170,256 files and images. In a limited sampling of the exposed files, I saw insurance documents that contained names, physical addresses, phone numbers, and emails. I also saw registration documents that contained PII and additional details about the vehicle (including VIN number, year, make, model, and more).
The database also contained just under 16,000 powers of attorney documents, which bestow the named grantee the legal authority to purchase, transfer, and assign title for the specific motor vehicle on behalf of the owner. Alternatively, they could delegate that authority to someone else to apply for a title, registration, or certified copy of the title. These documents were signed electronically and included the IP addresses of the individuals who signed them. Additionally, the database contained internal documents, such as software license agreements, indicating the terms, fees, and other information that should not be publicly exposed.
Information inside the database (and the name of the database itself) indicated the records belonged to Illinois-based ClaimPix, a platform for managing and filing auto insurance claims. I immediately sent a responsible disclosure notice to ClaimPix, and the database was restricted from public access shortly after and was no longer accessible. Although the records appeared to belong to ClaimPix, it is not known if the database was owned and managed directly by them or by a third-party contractor. It is also not known how long the database was exposed before I discovered it or if anyone else may have gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity.
I received the following reply to my responsible disclosure notice: “Thank you for alerting us to the security issues that you mentioned. We have investigated and confirmed your findings. We wanted to respond to you with a plan after we had time to identify the issue and also begin steps to remediate it. We have updated policies and our code to address this issue and will be making those changes live later this evening.”
According to their website, ClaimPix is used in the insurance claims process, vehicle transportation for damage inspections, and bill of lading receipts by companies across the entire United States. Users send customers a white‑labeled link via the ClaimPix portal where customers then take and upload required photos (such as vehicle damage, license plate, VIN, proof of coverage documents, etc.) using their mobile devices.
The process of filing insurance claims requires a range of documents that contain identifiable information that is not intended to be public. The exposure of personal data, insurance information, and even identification documents pose numerous potential risks both online and offline. In 2024, it was reported that the FTC received over 1.1 million identity theft reports and an estimated 2.6 million cases of related fraud. Exposed powers of attorney could potentially allow criminals to impersonate agents or representatives and attempt to initiate fraudulent sales, transfer property ownership or registration — all without the legitimate owner’s knowledge and consent.
Criminals could use information such as VIN numbers, license plates, and personal information to impersonate the owner, clone vehicles, or forge title and ownership documents. Cloning a vehicle (or VIN cloning) is a growing threat. It is basically identity theft for automobiles, where information is taken from a real, legally registered vehicle and then used to illegally register a stolen or salvaged car of a similar year, make, and model.
Although I was unable to find recent data on VIN cloning in the US, a 2025 report by Carfax Canada estimates that there could be over 372,000 potentially cloned VINs in Canada. The fact that, in 2022, Canada had 26.3 million registered vehicles while the US had approximately 285 million suggests that the overall scale of registered vehicles may make the risks of VIN cloning substantially higher in the United States. I am not saying that ClaimPix users or customers are or have been at risk of any form of fraud or scams, I am only providing a real-world scenario on how malicious actors could potentially misuse this type of information for educational purposes.
Another concern is the potential risk of insurance fraud by exploiting stolen or compromised data such as policy numbers, claim numbers, and PII. This type of fraud could happen to both insurers and policy holders. As a hypothetical example, if criminals gained access to an active claim that is being processed, and they knew that there was a deductible that must be paid to repair the claimant’s vehicle, they could attempt to fraudulently collect that payment directly from the policy holder.
On the other hand, for insurance companies, one common threat is criminals impersonating policyholders to file fraudulent claims using real information of their insurance policy, personal, and vehicle data. They could also use man-in-the-middle tactics to alter legitimate claims, increasing payouts and redirecting settlement or repair funds to their own accounts.
Another more creative approach criminals could potentially take would be to create a new, fake identity by combining real information from multiple people. They could then use this fake ID to apply for insurance policies and make fraudulent claims at a later date. I am not saying that ClaimPix’s users are at risk of these types of fraud, identity theft or impersonation. I am only identifying hypothetical risks based on documented methods that criminals have used in the past for the purposes of data protection and security awareness.
My advice to companies in the insurance industry is to encrypt all sensitive data so that, in the event of a data incident, the data is far more secure than in plain text documents. It is also important to enforce access controls with multi-factor authentication. Role-based permissions can also ensure that potentially sensitive data is only accessed by authorized individuals within the organization. This includes regular audits of cloud storage systems to ensure they restrict public access. Regular vulnerability testing, monitoring, and anomaly detection can increase the chances of identifying suspicious activity early.
For individuals who believe they may have had their personal or insurance information exposed in any data breach, it is important to act fast — especially if you notice any suspicious activity such as unexpected bills or unsolicited requests for more information. If there is unauthorized use of your identity, the major credit bureaus (Experian, Equifax, TransUnion) have systems that can place a fraud alert or credit freeze on your credit profile. This can stop criminals from creating new accounts and, if caught early, limit the damage and begin the road to recovery.
It is important to check credit reports and insurance statements periodically to identify suspicious activity or unknown accounts. There are a number of companies that offer identity theft monitoring for a monthly or yearly fee. Additionally, the FTC’s IdentityTheft.gov offers the ability to report cases of identity theft and provides helpful information for recovering from it. I am not claiming that there is any imminent threat from this data exposure. I am only providing this information for educational purposes, to exemplify what individuals can do to protect themselves in the event their data is compromised and exploited in any type of data breach.
I imply no wrongdoing by ClaimPix, or its employees, agents, contractors, affiliates, and/or related entities. I do not claim that any internal, employee, customer, or user data was ever at imminent risk. The hypothetical data-risk scenarios I have presented in this report are strictly and exclusively for educational purposes and do not reflect, suggest, or imply any actual compromise of data integrity. It should not be construed as a reflection of or commentary on any particular organization’s specific practices, systems, or security measures.
As an ethical security researcher, I do not download, retain, or share any data I discover. I only take a limited number of screenshots strictly when necessary and solely for verification and documentation purposes. I do not engage in any activities beyond identifying the security vulnerability and, where possible, notifying the relevant parties involved. I disclaim any and all liability from the use, interpretation, or reliance on this disclosure. I publish my findings to raise awareness of issues of data security and privacy. My aim is to encourage organizations to proactively implement measures to safeguard sensitive information against unauthorized access.
Website Planet’s Recent Publications
At Website Planet we work with an experienced team of ethical security research experts who uncover and disclose serious data leaks. Recently, cybersecurity expert Jeremiah Fowler discovered and disclosed a non-password protected database totaling 378.7 GB that appears to belong to Virginia-based Navy Federal Credit Union.He also found another unsecured database that contained 1.6 million audio files apparently belonging to Hello Gym.