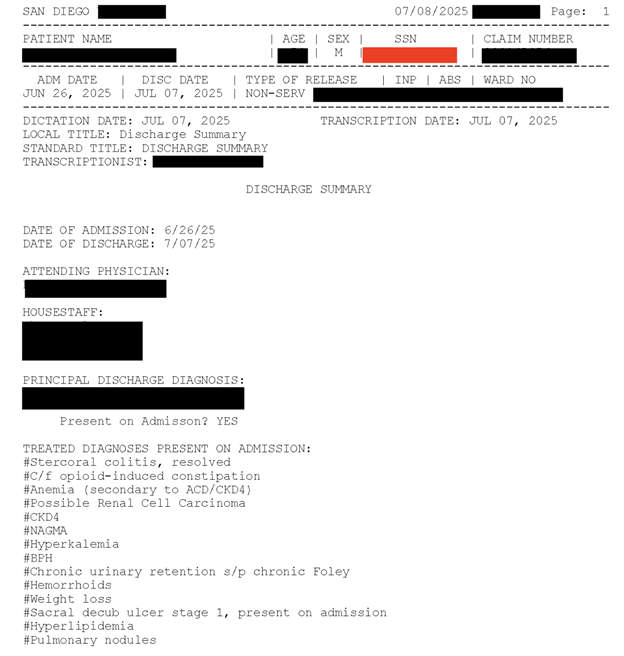
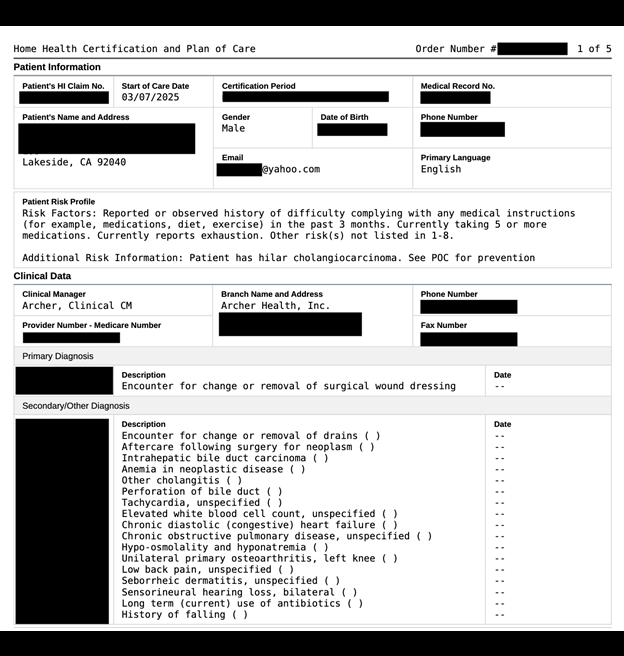
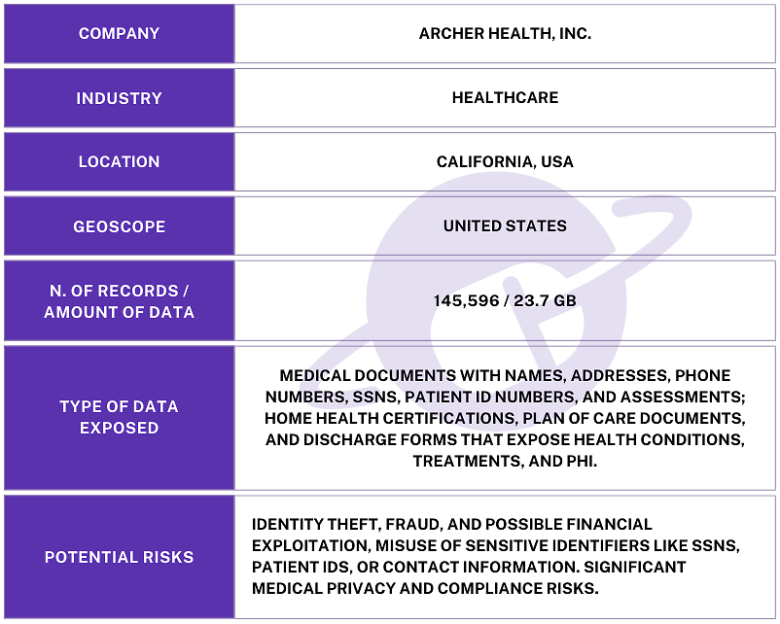
 The publicly exposed database was not password-protected or encrypted. It contained approximately 145,596 files in PDF, PNG, and other image formats. In a limited sampling of the exposed files, I saw medical documents that contained names, patient ID numbers, SSNs, physical addresses, phone numbers, and more. Additionally, there were documents marked as assessments, home health certifications, plan of care documents, and discharge forms that contained PII and PHI, as well as additional details such as diagnoses, treatments, and other potentially sensitive health-related data that should not be publicly exposed.
Information inside the database and the name of the database itself indicated the records belonged to California-based Archer Health, Inc. (also known as Archer Home Health), a company which provides a wide range of in-home healthcare and palliative care services. I immediately sent a responsible disclosure notice to Archer Health, Inc., and the database was restricted from public access within hours and is no longer accessible. I received a reply to my responsible disclosure notice the following day, which stated: “Thank you for bringing this to our attention. We take data security and patient privacy very seriously. Our team is actively investigating this matter and will address any security issues promptly.”
Although the records appeared to belong to Archer Health, Inc., it is not known if the database was owned and managed directly by them or by a third-party contractor. It is also not known how long the database was exposed before I discovered it or if anyone else may have gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity.
For healthcare providers, patient data is a critical asset — and the more complete the records are, the better it is for providing care and understanding the patients’ needs. However, the more complete the data is, the more potential risks arise if that information is ever exposed. Unfortunately, the healthcare sector is one of the most targeted by cybercriminals because of the highly valuable data they collect. According to statistics as of August 2025, the Department of Health and Human Services (HHS) Office for Civil Rights (OCR) reported a 239% increase in hacking-related data breaches between 2018 and 2023, and a 278% increase in ransomware attacks over the same period.
Health data is unique because it stays with individuals forever, whereas banking or credit information can be changed. Criminals also value this information because it could potentially enable a wide range of fraudulent activities, including extortion, identity theft, prescription fraud, false medical billing, and even the creation of synthetic identities that may go undetected for years. On the black market, health records are often sold at a higher price than financial data because they contain comprehensive personal and health profiles of individuals.
Health data is regulated by a federal law known as HIPAA, which sets national standards for protecting sensitive patient health information from disclosure without consent. Under the HIPAA Breach Notification Rule, organizations must promptly assess any unauthorized access or disclosure of PHI, notify affected individuals, and report significant breaches to the U.S. Department of Health and Human Services (HHS).
Aside from the potential risks the patients may face down the line due to the exposure of their personal data, cyberattacks represent a major potential risk for the healthcare industry because they can directly disrupt patient care and critical services. The exposure of internal records can also provide criminals with insights regarding how the organization operates, the software that is used, names of medical staff, and more.
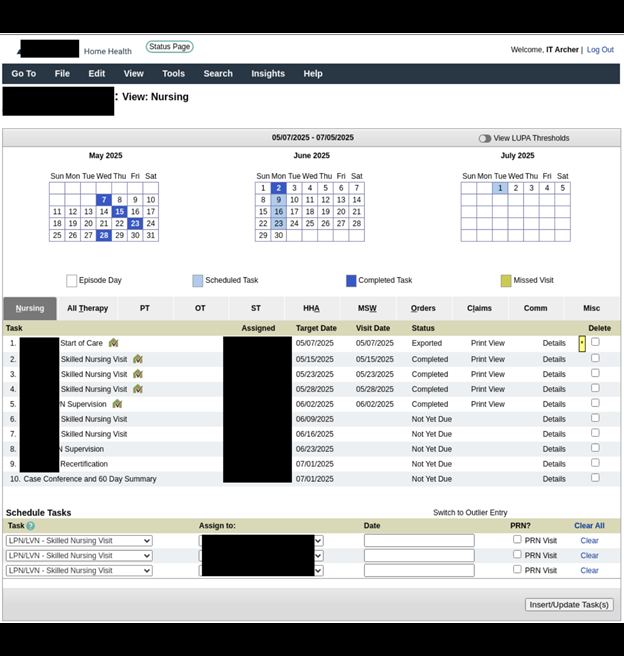
In this case, the database included numerous screenshots from a healthcare management software that showed active dashboards, logging, tracking, and scheduling details that included PII of patients and providers. The folders themselves indicated details of the data they contained. Some folders’ names contained the first and last names of patients; others used names such as “faxed orders”, “merged pdfs”, “received faxes”, “referrals”, “screenshots”, and more. As a general rule, file names in a database should not contain identifiable information (such as patient names or other PII) because they can potentially be exposed through error or monitoring logs, URLs, or misconfigured access controls.
Healthcare organizations should take additional steps to protect the data they collect and store, such as encrypting all stored and transmitted data, enforcing strict access controls with multi-factor authentication, and regularly auditing user permissions. This can help ensure that only authorized individuals have access to protected health information. If the records are encrypted, they are not human-readable and offer an additional layer of security in the event they are ever exposed.
Another good idea is to implement continuous monitoring and logging utilities to identify suspicious system activity. Software patching and vulnerability assessments can also help secure potential entry points or identify critical vulnerabilities before they can be exploited. It is also important that internal users with access to medical data receive training on the risks of phishing, social engineering, and data protection. After all, human error remains one of the leading causes of data exposures.
My advice to anyone who suspects their personal data may have been exposed in any data breach is to monitor their credit profile for suspicious activity. In the event of new unrecognized accounts or attempts to apply for loans or credit, it is a good idea to immediately report any unauthorized accounts charges or claims. Placing a fraud alert or credit freeze with major credit bureaus can help protect against identity theft if caught early. There are also many third-party companies that offer credit monitoring or identity protection services that could provide an additional layer of defense.
If the organization affected by the data breach has a portal, app, or member login area that requires a password, it is important to change those passwords and enable multi-factor authentication (2FA) if it is supported. Finally, make sure to review any medical billing statements or unexpected insurance claims for signs of potential medical fraud.
I imply no wrongdoing by Archer Health, Inc. or its employees, agents, contractors, affiliates, and/or related entities. I do not claim that any internal, employee, patient, or user data was ever at imminent risk. I only wish to raise public awareness of my findings to help organizations strengthen their data protection and cybersecurity practices. The hypothetical data-risk scenarios I have presented in this report are strictly and exclusively for educational purposes and do not reflect, suggest, or imply any actual compromise of data integrity. It should not be construed as a reflection of or commentary on any organization’s specific practices, systems, or security measures.
As an ethical security researcher, I do not download, retain, or share any data I discover. I only take a limited number of screenshots strictly when necessary and solely for verification and documentation purposes. I do not engage in any activities beyond identifying the security vulnerability and, where possible, notifying the relevant parties involved. I disclaim any and all liability arising from the use, interpretation, or reliance on this disclosure. I publish my findings to raise awareness of issues of data security and privacy. My aim is to encourage organizations to proactively implement measures to safeguard sensitive information against unauthorized access.
The publicly exposed database was not password-protected or encrypted. It contained approximately 145,596 files in PDF, PNG, and other image formats. In a limited sampling of the exposed files, I saw medical documents that contained names, patient ID numbers, SSNs, physical addresses, phone numbers, and more. Additionally, there were documents marked as assessments, home health certifications, plan of care documents, and discharge forms that contained PII and PHI, as well as additional details such as diagnoses, treatments, and other potentially sensitive health-related data that should not be publicly exposed.
Information inside the database and the name of the database itself indicated the records belonged to California-based Archer Health, Inc. (also known as Archer Home Health), a company which provides a wide range of in-home healthcare and palliative care services. I immediately sent a responsible disclosure notice to Archer Health, Inc., and the database was restricted from public access within hours and is no longer accessible. I received a reply to my responsible disclosure notice the following day, which stated: “Thank you for bringing this to our attention. We take data security and patient privacy very seriously. Our team is actively investigating this matter and will address any security issues promptly.”
Although the records appeared to belong to Archer Health, Inc., it is not known if the database was owned and managed directly by them or by a third-party contractor. It is also not known how long the database was exposed before I discovered it or if anyone else may have gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity.
For healthcare providers, patient data is a critical asset — and the more complete the records are, the better it is for providing care and understanding the patients’ needs. However, the more complete the data is, the more potential risks arise if that information is ever exposed. Unfortunately, the healthcare sector is one of the most targeted by cybercriminals because of the highly valuable data they collect. According to statistics as of August 2025, the Department of Health and Human Services (HHS) Office for Civil Rights (OCR) reported a 239% increase in hacking-related data breaches between 2018 and 2023, and a 278% increase in ransomware attacks over the same period.
Health data is unique because it stays with individuals forever, whereas banking or credit information can be changed. Criminals also value this information because it could potentially enable a wide range of fraudulent activities, including extortion, identity theft, prescription fraud, false medical billing, and even the creation of synthetic identities that may go undetected for years. On the black market, health records are often sold at a higher price than financial data because they contain comprehensive personal and health profiles of individuals.
Health data is regulated by a federal law known as HIPAA, which sets national standards for protecting sensitive patient health information from disclosure without consent. Under the HIPAA Breach Notification Rule, organizations must promptly assess any unauthorized access or disclosure of PHI, notify affected individuals, and report significant breaches to the U.S. Department of Health and Human Services (HHS).
Aside from the potential risks the patients may face down the line due to the exposure of their personal data, cyberattacks represent a major potential risk for the healthcare industry because they can directly disrupt patient care and critical services. The exposure of internal records can also provide criminals with insights regarding how the organization operates, the software that is used, names of medical staff, and more.
In this case, the database included numerous screenshots from a healthcare management software that showed active dashboards, logging, tracking, and scheduling details that included PII of patients and providers. The folders themselves indicated details of the data they contained. Some folders’ names contained the first and last names of patients; others used names such as “faxed orders”, “merged pdfs”, “received faxes”, “referrals”, “screenshots”, and more. As a general rule, file names in a database should not contain identifiable information (such as patient names or other PII) because they can potentially be exposed through error or monitoring logs, URLs, or misconfigured access controls.
Healthcare organizations should take additional steps to protect the data they collect and store, such as encrypting all stored and transmitted data, enforcing strict access controls with multi-factor authentication, and regularly auditing user permissions. This can help ensure that only authorized individuals have access to protected health information. If the records are encrypted, they are not human-readable and offer an additional layer of security in the event they are ever exposed.
Another good idea is to implement continuous monitoring and logging utilities to identify suspicious system activity. Software patching and vulnerability assessments can also help secure potential entry points or identify critical vulnerabilities before they can be exploited. It is also important that internal users with access to medical data receive training on the risks of phishing, social engineering, and data protection. After all, human error remains one of the leading causes of data exposures.
My advice to anyone who suspects their personal data may have been exposed in any data breach is to monitor their credit profile for suspicious activity. In the event of new unrecognized accounts or attempts to apply for loans or credit, it is a good idea to immediately report any unauthorized accounts charges or claims. Placing a fraud alert or credit freeze with major credit bureaus can help protect against identity theft if caught early. There are also many third-party companies that offer credit monitoring or identity protection services that could provide an additional layer of defense.
If the organization affected by the data breach has a portal, app, or member login area that requires a password, it is important to change those passwords and enable multi-factor authentication (2FA) if it is supported. Finally, make sure to review any medical billing statements or unexpected insurance claims for signs of potential medical fraud.
I imply no wrongdoing by Archer Health, Inc. or its employees, agents, contractors, affiliates, and/or related entities. I do not claim that any internal, employee, patient, or user data was ever at imminent risk. I only wish to raise public awareness of my findings to help organizations strengthen their data protection and cybersecurity practices. The hypothetical data-risk scenarios I have presented in this report are strictly and exclusively for educational purposes and do not reflect, suggest, or imply any actual compromise of data integrity. It should not be construed as a reflection of or commentary on any organization’s specific practices, systems, or security measures.
As an ethical security researcher, I do not download, retain, or share any data I discover. I only take a limited number of screenshots strictly when necessary and solely for verification and documentation purposes. I do not engage in any activities beyond identifying the security vulnerability and, where possible, notifying the relevant parties involved. I disclaim any and all liability arising from the use, interpretation, or reliance on this disclosure. I publish my findings to raise awareness of issues of data security and privacy. My aim is to encourage organizations to proactively implement measures to safeguard sensitive information against unauthorized access.
Website Planet’s Recent Publications
At Website Planet we work with an experienced team of ethical security research experts who uncover and disclose serious data leaks. Recently, cybersecurity expert Jeremiah Fowler discovered and disclosed a non-password protected database that contained 1.6 million audio files apparently belonging to Hello Gym.He also found another unsecured database that 5.1 million files totaling 10 TB apparently belonging to ClaimPix.