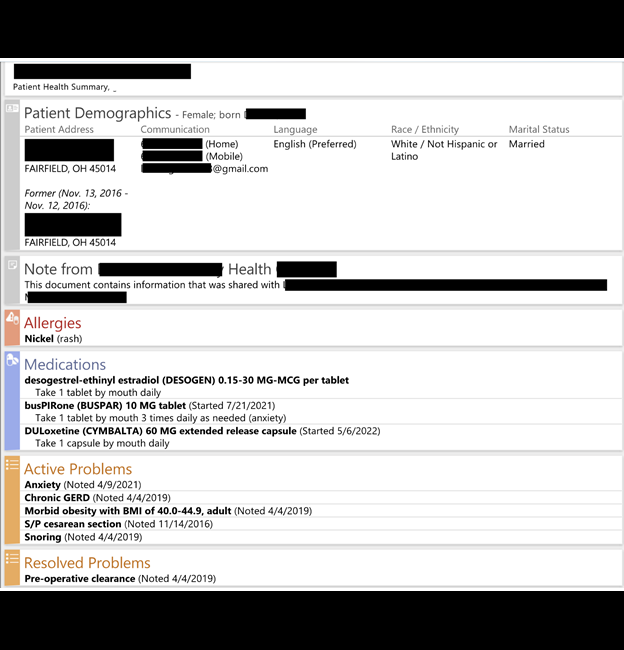
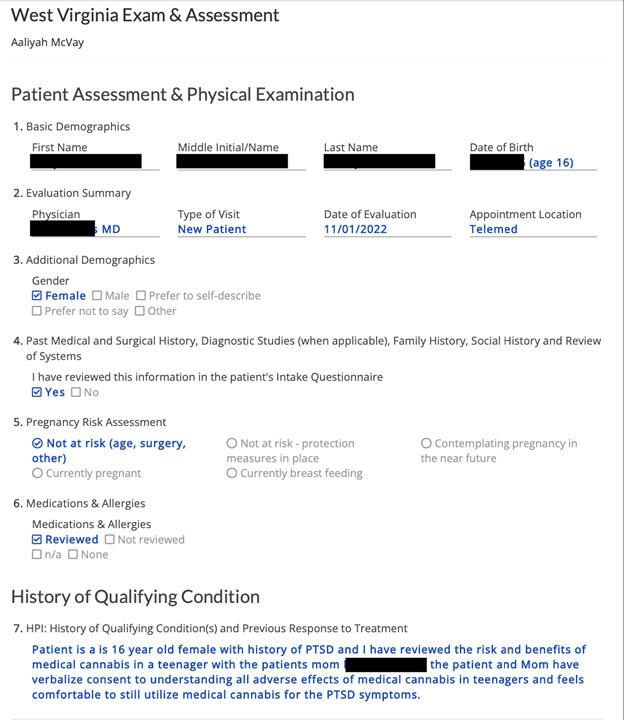
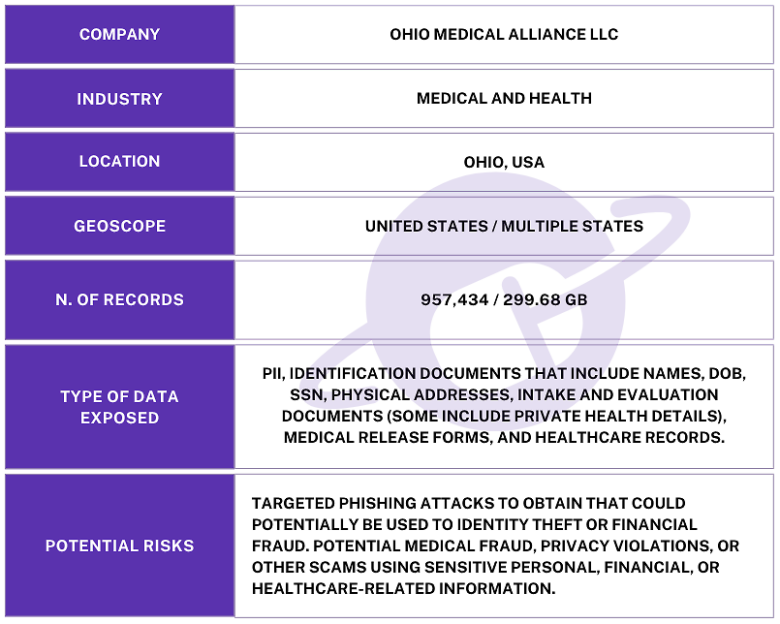
 The publicly exposed databases were not password-protected or encrypted and contained 957,434 records with a total size of 323 GB. In a limited sampling of the exposed records, I saw documents that included high-resolution images of driver’s licenses or identification documents that contained names, physical addresses, DOB, and license numbers. The folders were labeled with the first and last names of the patients and contained intake forms, medical records, release forms, physician certification forms with SSNs, mental health evaluations, and identification documents from multiple states. These medical documents indicated the patients’ diagnosis and the reason they were seeking to be prescribed medical marijuana.
The majority of files I saw in the two databases were in PDF, JPG, PNG formats. One CSV document named “staff comments” contained a large amount of internal communications, notes about clients, appointments, status, or personal situations. That document also contained an estimated 210,620 email addresses of clients and internal employees or business partners.
Information from the internal files suggests the records belong to an Ohio-based company called Ohio Medical Alliance LLC (OMA), operating under the brand “Ohio Marijuana Card”. This company is a telemedicine and in‑person provider that helps clients obtain physician‑certified medical marijuana cards. OMA facilitates evaluations for a wide range of qualifying health conditions through state‑licensed doctors.
I immediately sent a responsible disclosure notice to OMA, and the database was restricted from public access the following day and no longer accessible. I did not receive any reply to my responsible disclosure notice. Although the records appeared to belong to OMA, it is not known if the database was owned and managed directly by them or by a third-party contractor. It is also not known how long the database was exposed before I discovered it or if anyone else may have gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity.
According to their website, OMA has helped over 330,000 patients nationwide access medical marijuana. The company operates clinics in Ohio, Arkansas, Kentucky, Louisiana, Virginia,
The publicly exposed databases were not password-protected or encrypted and contained 957,434 records with a total size of 323 GB. In a limited sampling of the exposed records, I saw documents that included high-resolution images of driver’s licenses or identification documents that contained names, physical addresses, DOB, and license numbers. The folders were labeled with the first and last names of the patients and contained intake forms, medical records, release forms, physician certification forms with SSNs, mental health evaluations, and identification documents from multiple states. These medical documents indicated the patients’ diagnosis and the reason they were seeking to be prescribed medical marijuana.
The majority of files I saw in the two databases were in PDF, JPG, PNG formats. One CSV document named “staff comments” contained a large amount of internal communications, notes about clients, appointments, status, or personal situations. That document also contained an estimated 210,620 email addresses of clients and internal employees or business partners.
Information from the internal files suggests the records belong to an Ohio-based company called Ohio Medical Alliance LLC (OMA), operating under the brand “Ohio Marijuana Card”. This company is a telemedicine and in‑person provider that helps clients obtain physician‑certified medical marijuana cards. OMA facilitates evaluations for a wide range of qualifying health conditions through state‑licensed doctors.
I immediately sent a responsible disclosure notice to OMA, and the database was restricted from public access the following day and no longer accessible. I did not receive any reply to my responsible disclosure notice. Although the records appeared to belong to OMA, it is not known if the database was owned and managed directly by them or by a third-party contractor. It is also not known how long the database was exposed before I discovered it or if anyone else may have gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity.
According to their website, OMA has helped over 330,000 patients nationwide access medical marijuana. The company operates clinics in Ohio, Arkansas, Kentucky, Louisiana, Virginia,West Virginia. OMA operates multiple websites and performs evaluations for $198 each. According to the site’s privacy statement, OMA claims that all patient information is kept confidential in their HIPAA-compliant file storage system. The publicly exposed records could potentially create serious privacy and security risks in the wrong hands. Patient intake forms and medical history records often contain detailed personal and health information that could be used to impersonate patients. Information regarding sensitive medical conditions could potentially be exploited for harassment or possible extortion attempts. Moreover, medical records release authorizations could potentially be used to gain unauthorized access to additional healthcare data, increasing the risk of eroding personal medical privacy. Physician certification forms and any document that contains Social Security numbers or tax IDs in plain text, when combined with identification documents, could increase the possible risks for identity theft or financial fraud. The exposure of driver’s licenses and other forms of ID could be used for identity fraud or for creating fake accounts that require identification. As of 2025, in the United States, marijuana is legal in 40 of 50 states for medical use and in 24 states for recreational use, but remains illegal under federal law. Given the potential stigma, medical marijuana use is something that many people would want to remain private. Another concern is the exposure of mental health data that clients share with providers assuming it would remain confidential. Among the exposed documents, I saw a large number of evaluations that summarized PTSD, anxiety, and other mental health conditions. Mental health is a deeply private issue that could be stigmatized by employers, friends, or family if that information were to ever be publicly exposed. Generally, mental health evaluations and medical records are protected under the Health Insurance Portability and Accountability Act (HIPAA). The law requires strict privacy and security standards for the handling, storage, and sharing of protected health information by healthcare providers, clinics, and, in some cases, medical marijuana businesses when they qualify as HIPAA-covered entities. There are mixed messages regarding HIPAA coverage and the medical cannabis industry, but when individual employees of HIPAA-covered entities access PHI, they are subject to HIPAA’s privacy and security rules. My advice to anyone who believes their personal or health information may have been exposed in any data breach: it is important to take necessary steps to protect your data and identity. Monitoring credit reports can help identify any new accounts or suspicious activity. There are a range of companies that offer credit-monitoring services and can send notifications and alerts each time a new account is opened. Identifying and detecting fraud early can help limit the potential damage of identity theft — consider placing a fraud alert on your credit reports or even freezing a credit profile to prevent new accounts from being opened. It is also a good idea to change any passwords for accounts that may be linked to a data incident. For data breaches that expose SSNs, the Federal Trade Commission recommends reporting it to IdentityTheft.gov. I am not saying or claiming that OMA’s clients are at risk of any type of fraud or identity theft, I am only providing hypothetical scenarios to illustrate how criminals could potentially exploit this type of information. Companies and organizations that collect and store potentially sensitive documents (like patient information and health data) should take additional security measures to prevent unauthorized access and accidental data exposures. Images and PDF files can be password-protected to add a minimal additional layer of security. The best method to protect sensitive documents is to use encryption to make them non-human readable; this way, if data is ever exposed, it would be extremely difficult to decrypt. I would also recommend that companies do not store all data in one place and isolate records that are not in active use. Role-based permissions and time-restricted access to sensitive files can limit external exposures and lower the risks of an insider attack or insider data breach. Conducting routine security audits and penetration testing can also help identify misconfigured firewalls or detect if a database is publicly accessible. Finally, make sure the individuals working with sensitive data have proper training on important topics like data privacy, data protection, and phishing awareness. I imply no wrongdoing by Ohio Medical Alliance LLC (OMA), operating under the brand Ohio Marijuana Card, or its employees, agents, contractors, affiliates, and/or related entities. I do not claim that any internal, employee, customer, or user data was ever at imminent risk. The hypothetical data-risk scenarios I have presented in this report are strictly and exclusively for educational purposes and do not reflect, suggest, or imply any actual compromise of data integrity. It should not be construed as a reflection of or commentary on any organization’s specific practices, systems, or security measures. As an ethical security researcher, I do not download, retain, or share any data I discover. I only take a limited number of screenshots when necessary and solely for verification and documentation purposes. I do not engage in any activities beyond identifying the security vulnerability and, where possible, notifying the relevant parties involved. I expressly disclaim any and all liability for any and all actions that may be taken as a result of this disclosure. I publish my findings to raise awareness of issues of data security and privacy. My aim is to encourage organizations to proactively implement measures to safeguard sensitive information against unauthorized access.
What Is Website Planet?
Website Planet stands as the premier resource for web designers, digital marketers, developers, and businesses operating online. We offer a wide array of helpful tools and resources catering to individuals at all skill levels, from beginners to experts. Furthermore, we provide updates on the most recent advancements in cybersecurity.We work with an experienced team of ethical security research experts who uncover and disclose serious data leaks. Recently, cybersecurity expert Jeremiah Fowler discovered and disclosed a non-password protected database which exposed 1 million records belonging to Gladney Adoption Center, holding the names of children, birth parents, adopted parents, employees, leads and other internal potentially sensitive information. He also found another unsecured database that contained 38 GB of CSV and PDF files displaying hundreds of thousands of names, physical addresses, phone numbers, email addresses, and other potentially sensitive information belonging to IMDataCenter.