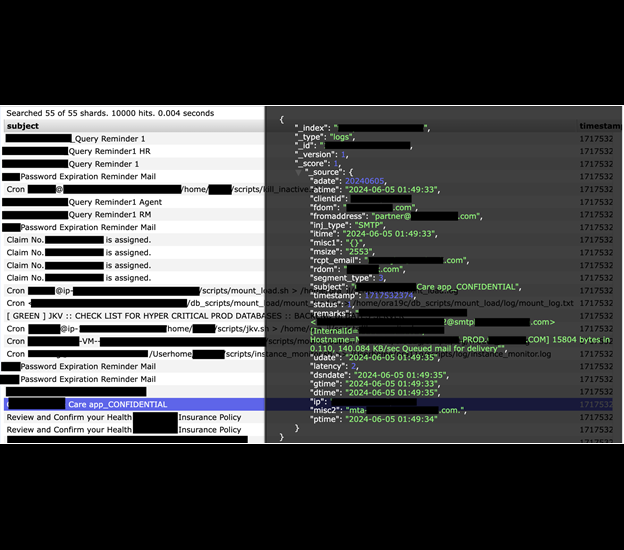
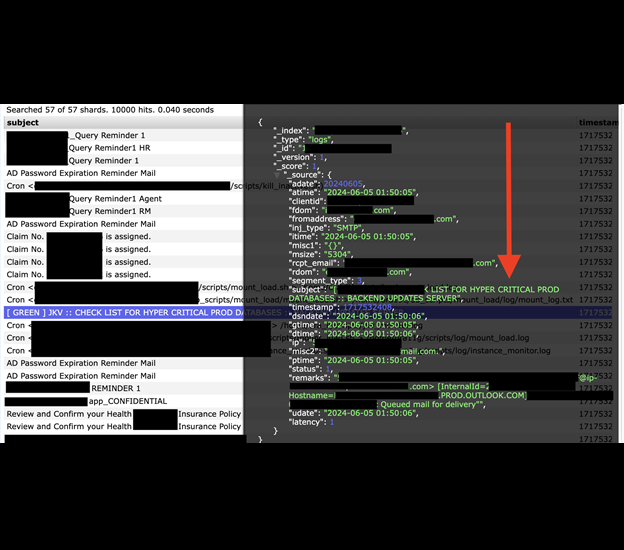
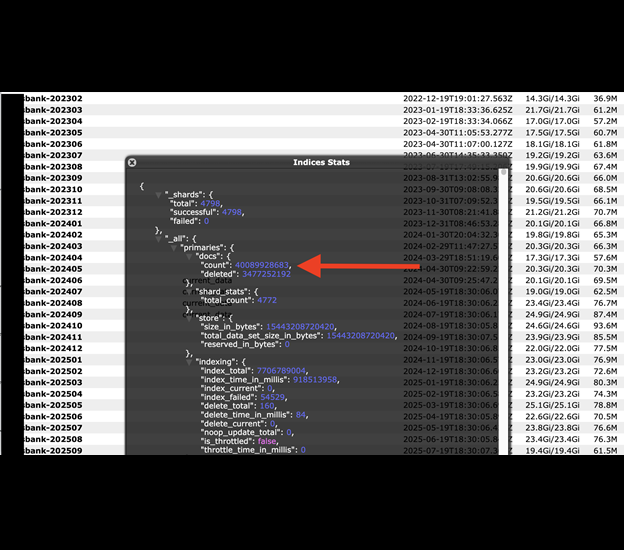
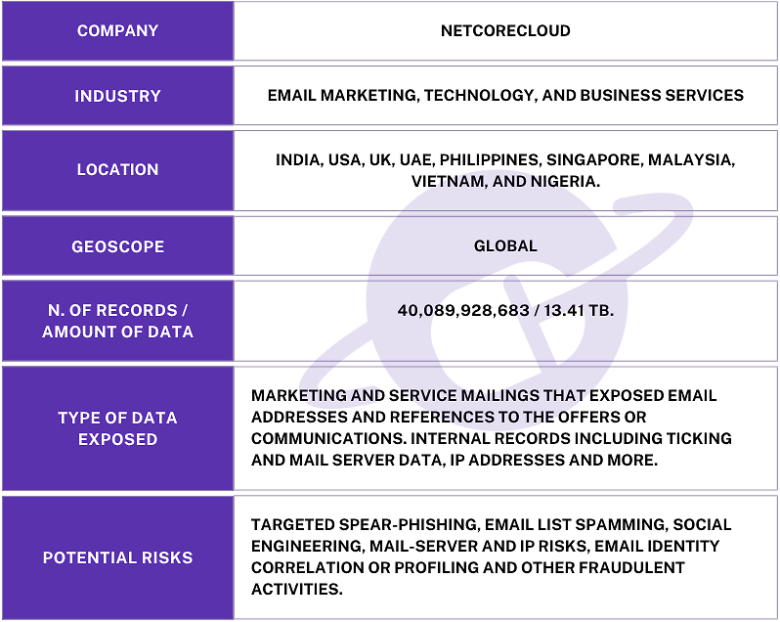
 The publicly exposed database was not password-protected or encrypted. It contained 40,089,928,683 records totaling 13.41 TB. In a limited sampling of the exposed files, I saw what appeared to be mail log records that contained a copious amount of email addresses, message subjects, and more. Among different files, I saw healthcare notifications and banking activity notices. Some of these notices included partial account numbers and specific information (such as IP addresses and SMTP details) that could be potentially sensitive and, therefore, should not be publicly exposed. I saw numerous records marked as confidential.
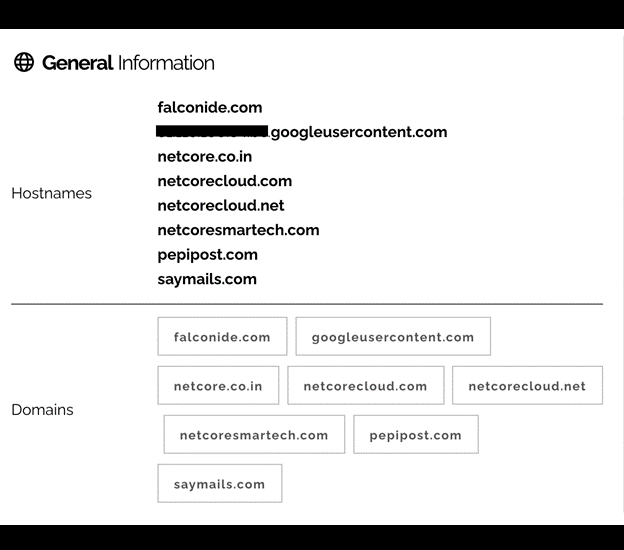
Information inside the database and the hostnames connected to the IP address indicated the records belonged to Netcore Cloud Pvt. Ltd (Netcore), a company based in Mumbai (India) that provides a wide range of outbound marketing services. I immediately sent a responsible disclosure notice to Netcore, and the database was restricted from public access the same day. It is no longer accessible. I received a reply thanking me for my notification and requesting more information. I provided the timeline and relevant facts of the discovery.
Although the records appeared to belong to Netcore Cloud Pvt. Ltd, it is not known if the database was owned and managed directly by them or by a third-party contractor. It is also not known how long the database was exposed before I discovered it or if anyone else may have gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity.
Netcore is an AI-powered marketing automation platform that allows clients to design and send various types of email campaigns, including promotional messages, automated transactional emails like order confirmations, and trigger-based emails that respond to specific customer actions. According to their LinkedIn account: “Netcore provides a customer engagement and experience suite for marketers. The platform enables marketers to connect customer data across channels and systems across digital channels like Web, Email, App Notifications, Whatsapp, SMS and RCS. Netcore is used by 6,500 brands in 40 countries across sectors such as Ecommerce, retail, banking & financial services, media & entertainment, and travel, to deliver AI-powered experiences.”
The exposure of billions of digital messaging records has numerous potential risks that go far deeper than unwanted spam messages. The exposure of email addresses (both personal and professional) and mail delivery records could provide criminals with a better understanding of the business, customer, or banking relationships that an individual has. Hypothetically, these records could reveal sensitive personal and financial data that could be used by criminals for targeted phishing attempts.
Another potential risk could be clone-phishing (or spoofing) legitimate marking or account notification messages. Criminals could theoretically pose as a company or service provider to known customers by using real header or meta data, subject lines, or sender addresses as a template. The goal of this type of attack would be obtaining additional personal information, getting financial data, or distributing malware while the recipient believes it is a legitimate message from a business they trust.
Many email addresses are formatted to contain full or partial names and could provide insight on the real identities of individuals based on the exposure of email addresses alone. These addresses could also be cross-referenced against previous data breaches or info-stealer malware logs for credential harvesting or other targeted activities. Knowing an individual’s email address and that it is connected to specific accounts could also increase the potential risks of social-engineering, account or password recovery, or even account takeover attempts. I am not claiming that these email accounts or individuals were ever at risk and I am only providing hypothetical examples of how the publicly exposed data could be used for educational purposes.
The publicly exposed database was not password-protected or encrypted. It contained 40,089,928,683 records totaling 13.41 TB. In a limited sampling of the exposed files, I saw what appeared to be mail log records that contained a copious amount of email addresses, message subjects, and more. Among different files, I saw healthcare notifications and banking activity notices. Some of these notices included partial account numbers and specific information (such as IP addresses and SMTP details) that could be potentially sensitive and, therefore, should not be publicly exposed. I saw numerous records marked as confidential.
Information inside the database and the hostnames connected to the IP address indicated the records belonged to Netcore Cloud Pvt. Ltd (Netcore), a company based in Mumbai (India) that provides a wide range of outbound marketing services. I immediately sent a responsible disclosure notice to Netcore, and the database was restricted from public access the same day. It is no longer accessible. I received a reply thanking me for my notification and requesting more information. I provided the timeline and relevant facts of the discovery.
Although the records appeared to belong to Netcore Cloud Pvt. Ltd, it is not known if the database was owned and managed directly by them or by a third-party contractor. It is also not known how long the database was exposed before I discovered it or if anyone else may have gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity.
Netcore is an AI-powered marketing automation platform that allows clients to design and send various types of email campaigns, including promotional messages, automated transactional emails like order confirmations, and trigger-based emails that respond to specific customer actions. According to their LinkedIn account: “Netcore provides a customer engagement and experience suite for marketers. The platform enables marketers to connect customer data across channels and systems across digital channels like Web, Email, App Notifications, Whatsapp, SMS and RCS. Netcore is used by 6,500 brands in 40 countries across sectors such as Ecommerce, retail, banking & financial services, media & entertainment, and travel, to deliver AI-powered experiences.”
The exposure of billions of digital messaging records has numerous potential risks that go far deeper than unwanted spam messages. The exposure of email addresses (both personal and professional) and mail delivery records could provide criminals with a better understanding of the business, customer, or banking relationships that an individual has. Hypothetically, these records could reveal sensitive personal and financial data that could be used by criminals for targeted phishing attempts.
Another potential risk could be clone-phishing (or spoofing) legitimate marking or account notification messages. Criminals could theoretically pose as a company or service provider to known customers by using real header or meta data, subject lines, or sender addresses as a template. The goal of this type of attack would be obtaining additional personal information, getting financial data, or distributing malware while the recipient believes it is a legitimate message from a business they trust.
Many email addresses are formatted to contain full or partial names and could provide insight on the real identities of individuals based on the exposure of email addresses alone. These addresses could also be cross-referenced against previous data breaches or info-stealer malware logs for credential harvesting or other targeted activities. Knowing an individual’s email address and that it is connected to specific accounts could also increase the potential risks of social-engineering, account or password recovery, or even account takeover attempts. I am not claiming that these email accounts or individuals were ever at risk and I am only providing hypothetical examples of how the publicly exposed data could be used for educational purposes.
Potential Risks of Open Ports and Infrastructure Exposure
An open port is a network endpoint on a host that could potentially accept connections for a range of services. According to an IoT search engine review of the IP address, in this case, there were a total of 89 open ports. While not all open ports are dangerous, any internet-facing host with this many open ports could potentially create a large attack surface for cybercriminals to target. Common ports that are usually associated with remote admin, directory/DB, VPN, messaging, and security tooling should not be publicly accessible. Open ports could hypothetically allow criminals to test the network to try and identify known-vulnerability exploits and misconfigurations; they could also attempt brute-force or credential-stuffing, service fingerprinting, and even DDoS attacks on internal non-public infrastructure. Some of the records I saw appeared to indicate internal services and access data that was marked as “production”. They referenced databases and backend update servers. The potential risk of any organization exposing critical infrastructure details is that they could be used as a roadmap or a blueprint for how the service operates. The exposure of server names, IP addresses, and even potential usernames could provide sensitive details about the organization’s internal systems. Even without credentials or passwords, the exposure of operational details could increase the potential for unauthorized access to production databases and any information they contain. Exposing detailed internal and infrastructure data could hypothetically make it easier for criminals to attempt to compromise the system. Ransomware is a serious concern for any organization and, unfortunately, most modern ransomware variants can easily locate, encrypt, or delete backups with the goal of forcing the victim to pay a ransom. My advice to anyone who believes that their email may have been leaked in a data breach is to know the most common threats. As a general rule, don’t click links or open attachments in unexpected messages from unknown senders. Always verify senders and only communicate through official channels if the communications contain sensitive information. This can limit the chances of a targeted phishing or social engineering attempt using real information from a breach or hacked data. If you receive unexpected MFA requests or failed login attempts, it is a good idea to change the password on the affected account to a strong unique password. Use an authenticator app or hardware key when possible and make sure you know what apps or accounts are connected to your email. It is also a good idea to review account recovery information (such as phone numbers or backup emails) and make sure they are up to date. Some email providers offer features that send alerts and notifications of account changes or failed login attempts. Keeping account data accurate and configuring alert settings can help prevent account takeover attempts or help recover the account if it is compromised.Disclosure
As an ethical security researcher, I do not download or extract data. I often manually review and query a limited amount of data to understand what was there, who it affects, its geoscope, and potential risks. According to Netcore Cloud’s website, their client base includes many companies and brands that are well-known and have extensive numbers of customers. It is not known how many of the approximately 6,500 businesses that use Netcore may have been affected (or whether any were affected at all) by the reported exposure. While this database is one of the largest I have discovered in many years, the 40 billion records it holds are most likely not all unique. Account notifications, mailing lists, and general outreach would likely generate recurring messages to the same email address, so the number of total records is larger than the total number of potentially affected individuals. Nevertheless, the reality of this exposure is that this information could potentially provide cybercriminals with key trends and insights into account activities and the contact information of many millions of individuals. I imply no wrongdoing by Netcore Cloud, or its employees, agents, contractors, affiliates, and/or related entities. I do not claim that any internal, employee, customer, or user data was ever at imminent risk. The hypothetical data-risk scenarios I have presented in this report are strictly and exclusively for educational purposes and do not reflect, suggest, or imply any actual compromise of data integrity. It should not be construed as a reflection of or commentary on any particular organization’s specific practices, systems, or security measures. I do not engage in any activities beyond identifying the security vulnerability and, where possible, notifying the relevant parties involved. I disclaim any and all liability from the use, interpretation, or reliance on this disclosure. I publish my findings to raise awareness of issues of data security and privacy. My aim is to encourage organizations to proactively implement measures to safeguard sensitive information against unauthorized access.Website Planet’s Recent Publications
At Website Planet we work with an experienced team of ethical security research experts who uncover and disclose serious data leaks. Recently, cybersecurity expert Jeremiah Fowler discovered and disclosed a non-password protected database containing 85,361 files totaling 158 GB of data apparently belonging to Rainwalk.He also found another unsecured database containing 178,519 files apparently belonging to Invoicely.