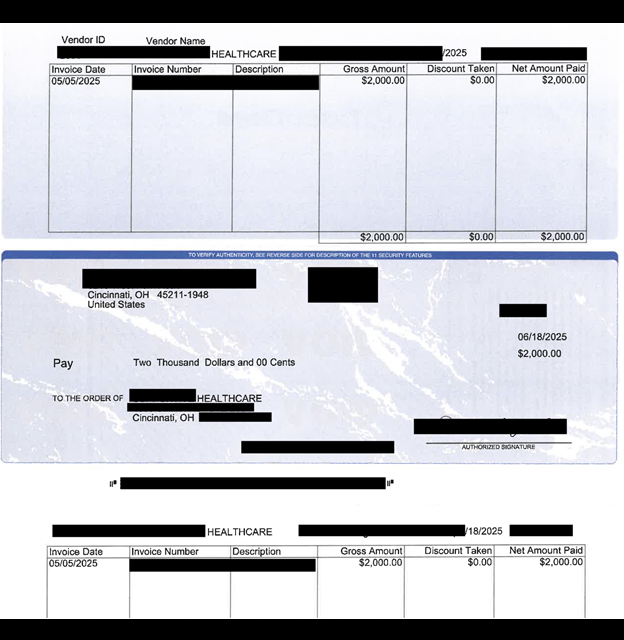
 The publicly exposed database was not password-protected or encrypted. It contained 178,519 files in xlsx, csv, pdf, and other image formats. In a limited sampling of the exposed files, I saw invoices containing PII (such as names, physical addresses, phone numbers, tax ID numbers, and more) of service providers, partners, employees, and customers around the world. Additionally, the database held a range of other documents that should not be publicly exposed, such as airline tickets, receipts for ride-sharing services, health insurance and medical payments, and more.
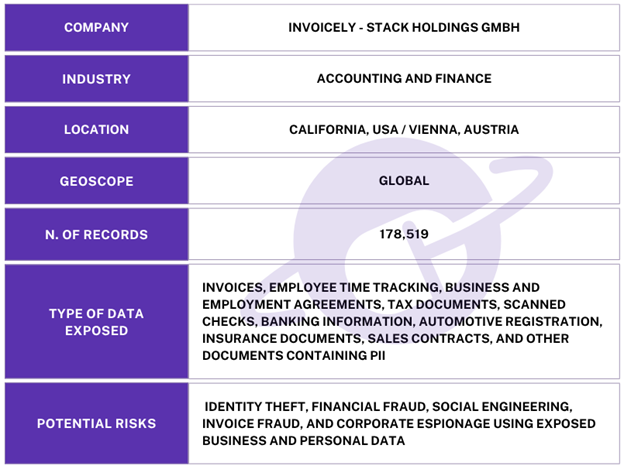
Information inside the database and the name of the database itself indicated the records belonged to Invoicely by Stack Holdings GmbH, a Vienna-based SaaS portfolio company. I immediately sent a responsible disclosure notice to Invoicely using their support ticketing system, and the database was restricted from public access and no longer accessible within hours. Although the records appeared to belong to Invoicely, it is not known if the database was owned and managed directly by them or by a third-party contractor. It is also not known how long the database was exposed before I discovered it or if anyone else may have gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity. I did not receive any reply to my responsible disclosure notice.
Invoicely is a cloud-based invoicing and billing platform that provides tools for creating estimates, automating recurring billing, sending payment reminders, and tracking time, expenses, and vehicle mileage. The platform has a free plan with limited invoices and clients, plus paid tiers with more features and flexibility. The application is available for both iOS and Android operating systems. According to their LinkedIn page, Invoicely is used by more than 250,000 businesses worldwide.
The exposure of invoices, purchase orders, work and time-tracking records, tax documents, and financial information poses serious potential risks. With so many different types of documents stored in one place it creates a broad range of potential attacks and methods that could hypothetically be used to target individuals and companies. The exposure of names, emails, physical addresses, phone numbers, tax ID numbers, and financial account details provide a wealth of information that criminals could potentially use to commit identity theft or financial fraud. Detailed personal information increases the possibility of successful spear-phishing and social engineering attacks. Knowing details about business transactions or employment agreements can potentially help criminals identify individuals that could be higher value targets.
Another potential risk that has risen in recent years is invoice fraud. According to the 2024 AFP Payments Fraud and Control Survey, 80% of organizations experienced some form of payment or invoice fraud attacks or attempts in 2023, which represents an increase of 15% compared to the previous year. Invoice fraud occurs when criminals use fake or manipulated invoices to trick companies or individuals into making fraudulent payments. When invoices are exposed in a data breach, criminals could potentially use internal information such as payee names, billing addresses, account numbers, and transaction histories to create convincing requests, redirect payments to their own accounts, or commit identity theft.
Exposed tax documents contain personal identifiers and SSN or tax ID numbers, dates of birth, employer details, and other potentially sensitive information. While not as prominent as invoice or payment fraud schemes, fraudulent tax filings are another potential concern. During the 2025 tax season in the United States, the IRS estimated that approximately 6,000 tax returns were filed using stolen identities. That year, the organization blocked an estimated $54 million USD in fraudulent refunds. Even if criminals are not successful in their attempts, it can create a difficult situation for the legitimate taxpayer who may need to endure a time-consuming dispute process with tax authorities. However, I am not claiming that Invoicely’s customers, users, or other organizations are or were ever at risk of these threats and only provide real world risk scenarios for educational purposes.
My advice to organizations that develop and provide invoice and accounting platforms, applications, or services is to limit the collection and retention of personal data when possible. Encrypt sensitive information so that it is not human readable; that way, if there is a data exposure, encryption adds an additional layer of security. While not impossible to decrypt, properly encrypted files remain extremely difficult to access without the correct credentials.
Furthermore, continuous monitoring and logging can help identify suspicious activity and flag unauthorized access. I also recommend regular vulnerability scanning and penetration testing to help identify issues including publicly accessible storage accounts or internal network vulnerabilities. This also goes for third-party vendors and contractors to ensure that they also follow strict data protection and security measures.
For individuals and companies who suspect their personal or internal business data may have been exposed in any type of breach, I would recommend taking proactive steps such as:
The publicly exposed database was not password-protected or encrypted. It contained 178,519 files in xlsx, csv, pdf, and other image formats. In a limited sampling of the exposed files, I saw invoices containing PII (such as names, physical addresses, phone numbers, tax ID numbers, and more) of service providers, partners, employees, and customers around the world. Additionally, the database held a range of other documents that should not be publicly exposed, such as airline tickets, receipts for ride-sharing services, health insurance and medical payments, and more.
Information inside the database and the name of the database itself indicated the records belonged to Invoicely by Stack Holdings GmbH, a Vienna-based SaaS portfolio company. I immediately sent a responsible disclosure notice to Invoicely using their support ticketing system, and the database was restricted from public access and no longer accessible within hours. Although the records appeared to belong to Invoicely, it is not known if the database was owned and managed directly by them or by a third-party contractor. It is also not known how long the database was exposed before I discovered it or if anyone else may have gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity. I did not receive any reply to my responsible disclosure notice.
Invoicely is a cloud-based invoicing and billing platform that provides tools for creating estimates, automating recurring billing, sending payment reminders, and tracking time, expenses, and vehicle mileage. The platform has a free plan with limited invoices and clients, plus paid tiers with more features and flexibility. The application is available for both iOS and Android operating systems. According to their LinkedIn page, Invoicely is used by more than 250,000 businesses worldwide.
The exposure of invoices, purchase orders, work and time-tracking records, tax documents, and financial information poses serious potential risks. With so many different types of documents stored in one place it creates a broad range of potential attacks and methods that could hypothetically be used to target individuals and companies. The exposure of names, emails, physical addresses, phone numbers, tax ID numbers, and financial account details provide a wealth of information that criminals could potentially use to commit identity theft or financial fraud. Detailed personal information increases the possibility of successful spear-phishing and social engineering attacks. Knowing details about business transactions or employment agreements can potentially help criminals identify individuals that could be higher value targets.
Another potential risk that has risen in recent years is invoice fraud. According to the 2024 AFP Payments Fraud and Control Survey, 80% of organizations experienced some form of payment or invoice fraud attacks or attempts in 2023, which represents an increase of 15% compared to the previous year. Invoice fraud occurs when criminals use fake or manipulated invoices to trick companies or individuals into making fraudulent payments. When invoices are exposed in a data breach, criminals could potentially use internal information such as payee names, billing addresses, account numbers, and transaction histories to create convincing requests, redirect payments to their own accounts, or commit identity theft.
Exposed tax documents contain personal identifiers and SSN or tax ID numbers, dates of birth, employer details, and other potentially sensitive information. While not as prominent as invoice or payment fraud schemes, fraudulent tax filings are another potential concern. During the 2025 tax season in the United States, the IRS estimated that approximately 6,000 tax returns were filed using stolen identities. That year, the organization blocked an estimated $54 million USD in fraudulent refunds. Even if criminals are not successful in their attempts, it can create a difficult situation for the legitimate taxpayer who may need to endure a time-consuming dispute process with tax authorities. However, I am not claiming that Invoicely’s customers, users, or other organizations are or were ever at risk of these threats and only provide real world risk scenarios for educational purposes.
My advice to organizations that develop and provide invoice and accounting platforms, applications, or services is to limit the collection and retention of personal data when possible. Encrypt sensitive information so that it is not human readable; that way, if there is a data exposure, encryption adds an additional layer of security. While not impossible to decrypt, properly encrypted files remain extremely difficult to access without the correct credentials.
Furthermore, continuous monitoring and logging can help identify suspicious activity and flag unauthorized access. I also recommend regular vulnerability scanning and penetration testing to help identify issues including publicly accessible storage accounts or internal network vulnerabilities. This also goes for third-party vendors and contractors to ensure that they also follow strict data protection and security measures.
For individuals and companies who suspect their personal or internal business data may have been exposed in any type of breach, I would recommend taking proactive steps such as:- Changing passwords on affected accounts, applications, or services. This can also include primary email accounts, as they are often used as a password-recovery method for various logins. As a general rule, use multi-factor authentication (MFA) when possible and never reuse passwords.
- Obtaining a credit report to check for new accounts or suspicious activity, as this can be a sign of identity theft. The sooner these attempts are identified the easier it can be to mitigate the situation and recover. There are also many companies that offer credit-monitoring services and can send real-time notifications.
- If you are a business owner or accounting professional, beware of unsolicited payment requests or duplicate invoices with changes to payment or financial accounts. Only communicate through official communication channels and verify the person is who they say they are. Keep in mind that many phishing and social-engineering attempts begin with criminals leveraging exposed information, and that this can occur weeks, months, or even years after a data breach.
- Keeping accurate records, reviewing account statements, and implementing a verification process can add additional steps to help identify fraud and criminal activity.
Website Planet’s Recent Publications
At Website Planet we work with an experienced team of ethical security research experts who uncover and disclose serious data leaks. Recently, cybersecurity expert Jeremiah Fowler discovered and disclosed a non-password protected database containing 145,000 files contained within 23 GB of data apparently belonging to Archer Health, Inc.He also found another unsecured database containing 85,361 files totaling 158 GB of data apparently belonging to Rainwalk.