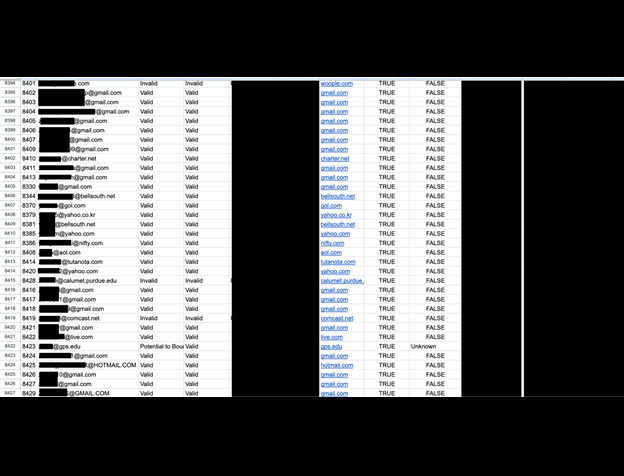
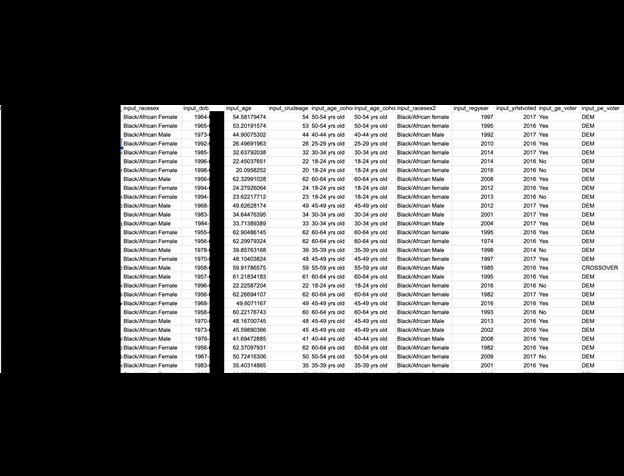
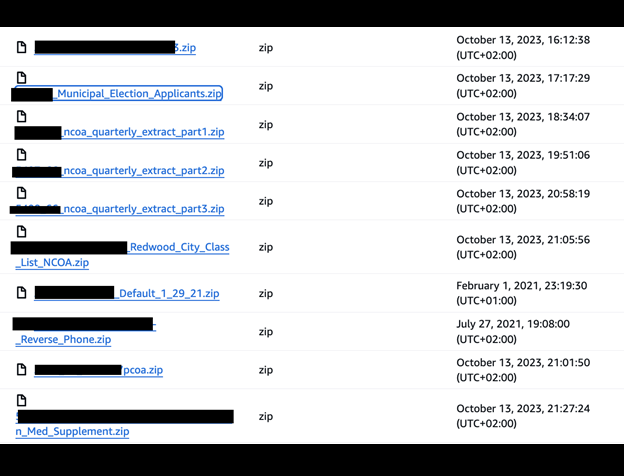
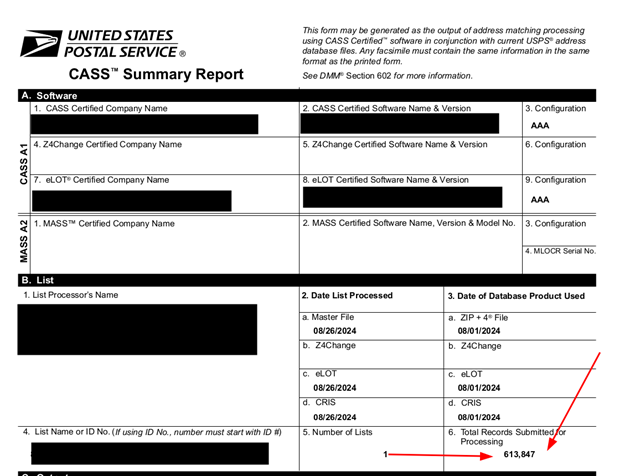
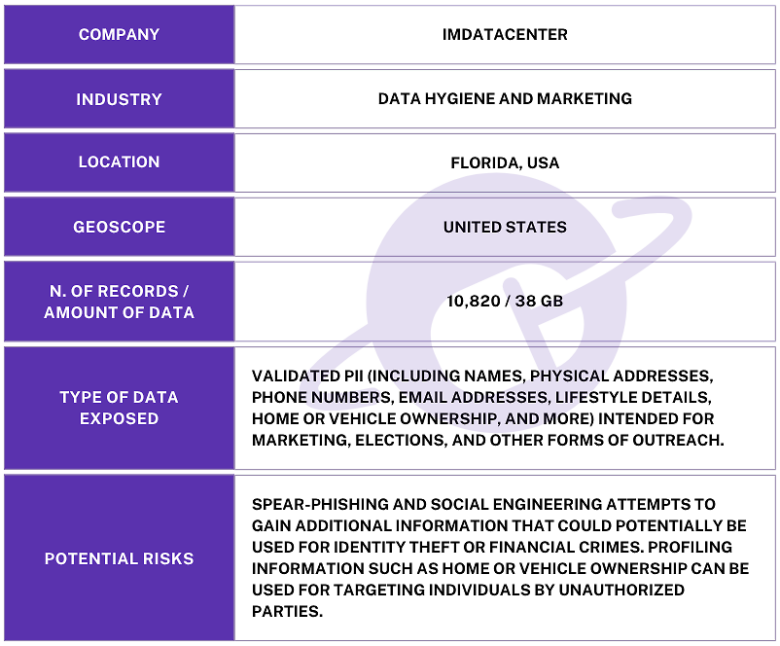
 The publicly exposed database was not password-protected or encrypted. It contained 10,820 records, with a total size of 38 GB. The majority of the files were .csv spreadsheets containing many thousands or hundreds of thousands of rows of PII. In a limited sampling of the exposed files, I saw documents that included PII such as names, physical addresses, email addresses, phone numbers, and lifestyle or ownership information. The records appeared to be a storage repository for client orders labeled “reports” and “results”. Files names indicated these lists were used for multiple purposes, including sales and marketing leads for industries such as insurance, solar, elections, car warranties, hospitals, healthcare providers, and more.
The name of the database as well as the information inside it indicated the records belonged to a Florida-based company called IMDataCenter. The firm provides data append and enhancement solutions designed to improve marketing strategies through lead scoring and identity management. I immediately sent a responsible disclosure notice to IMDataCenter, and the database was restricted from public access soon after and no longer accessible. I received a reply stating “Data security is really important to us too and really appreciate you sharing this information with us. We are working to secure the information ASAP”. Although the records appeared to belong to IMDataCenter, it is not known if the database was owned and managed directly by them, by a third-party contractor, or by an affiliated or related company, including a parent or holding company. It is also not known how long the database was exposed before I discovered it or if anyone else may have gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity.
According to their website, IMDataCenter has a data library built from hundreds of verified public and proprietary online and offline sources; it includes detailed information on over 260 million individuals and 130 million households. It contains 600 million email addresses, 550 million phone numbers (including 230 million mobile numbers), 153 million property records, 208 million deeds, and data on 75 million homeowners.
Based on the file names, the database appeared to hold documents related to campaigns or individual customer orders rather than IMData’s entire data library. In a limited sample, I saw files that contained the contact information of numerous individuals. This information appeared to be intended for a range of marketing or outreach services, such as: the healthcare sector, investor prospects, medicare eligibility, patients, medical supplements, automotive and home ownership, insurance, elections, restaurants, food services, and many more. With each CSV document containing the data of thousands of individuals, it is difficult to calculate the total number of those who may have potentially had their data exposed.
These types of marketing campaigns can be very expensive, so it is important that addresses, emails, and phone numbers are valid. IMData provides a range of data hygiene and validation services to ensure physical mailing addresses are accurate, including USPS change-of-address checks and other types of confirmed contact details.
The exposure of such a large amount of PII, including names, addresses, emails, phone numbers, and other personalized lifestyle data could potentially pose significant privacy and cybersecurity risks. When data is verified and validated, that information can be used not only to identify individuals but also to potentially build detailed personal profiles. These profiles are valuable not only to marketers, but also to criminals who could potentially use that data for targeted phishing attacks, identity theft, or other forms of fraudulent activities.
Validated and active email addresses and phone numbers could be used as working lists for criminals to launch phishing, spam, and scam campaigns. Verified home addresses allow for realistic mail fraud, social engineering, or fake-check scams. The latter are also known as cash-back scams, where the victim receives a counterfeit check, and criminals ask them to return a portion of the money before the bank identifies the check as fake. The potential victim is then responsible for any amount of money they sent to the scammer.
Additionally, criminals often cross-reference previous data breaches looking for additional information or financial accounts, making this kind of dataset potentially valuable for resale on dark web markets. I am not saying that IMData’s clients or the individuals in IMData’s database were ever at risk of these types of fraudulent activities. I am only providing a real-world example of how this data could potentially be exploited if it were to fall into the wrong hands.
My advice to anyone who believes that their personal data may have been exposed in any data breach is to take steps to protect yourself. Be aware of common schemes used by criminals and always be suspicious if something feels off or not right. When it comes to emails, never click on links or provide personal information to unknown senders or unsolicited messages. The same applies to phone calls. Technology has provided scammers with a wide range of tools to deceive their targets. They can spoof phone numbers to appear as if they were calling from a trusted organization or even use deepfake audio to spoof voices.
Physical mail can also be a potential risk because people are more inclined to trust the postal service than the internet, and they tend to assume mail is sent from a trusted source. Always verify that anyone who contacts you with inside or privileged knowledge is who they say they are before sharing your private or financial information. By being suspicious and verifying individuals or businesses asking for personal data, potentially affected individuals can reduce the risk of further harm from most data breaches.
Companies that collect and store large amounts of personal data must invest in cybersecurity and data protection. When processing data is your core business, a breach can be compared to leaking a secret recipe or proprietary code. Remember that all data is valuable. Even if a portion of that data comes from public sources, it can be combined with information from previous breaches and become a critical puzzle piece for criminals to build profiles on individuals.
I recommend that companies routinely encrypt the data they collect to make it non-human readable. Implementing strict access controls and multi-factor authentication can help prevent unauthorized access. Conducting regular security audits, penetration testing, and vulnerability scanning can help identify critical issues and publicly exposed data. It is also a good idea for companies to have a dedicated communication channel for data security and privacy. This way, when customers, partners, or internal staff report suspicious activities or issues, the information will swiftly reach the right person or team.
We are living in a new era of the digital world where personal data is a highly valuable commodity that is bought, sold, and traded by companies. Our personal information and data are often used with very little transparency or accountability, and in some cases, without explicit consent. As we face the reality of our identities and online activities being a valuable product for data brokers and marketing agencies, we must also face the fact that information resellers and the data industry as a whole have far outpaced privacy protections. It is my personal opinion that there needs to be more regulation over digital rights so that individuals may have greater control over how their personal data is collected, used, and shared.
There has been a shift in both legal policies — e.g. California Consumer Privacy Act (CCPA), Virginia Consumer Data Protection Act (VCDPA), Colorado Privacy Act (CPA) — and public awareness when it comes to digital privacy. Unfortunately, it is hard to reverse years of industry practices and perhaps even harder to remove the vast amounts of personal data that is already out there. I am not saying that data brokers and marketing companies do not provide legitimate and valuable services. Companies like IMData ensure that contacts are valid and that those individuals receive important information from companies, civic groups, medical providers, local governments, and many more entities.
I imply no wrongdoing by IMDataCenter, Brooks Integrated Marketing, or their employees, agents, contractors, affiliates, and/or related entities. I do not claim that any internal, employee, customer, or user data was ever at imminent risk. The hypothetical data-risk scenarios I have presented in this report are strictly and exclusively for educational purposes and do not reflect, suggest, or imply any actual compromise of data integrity. It should not be construed as a reflection of or commentary on any organization’s specific practices, systems, or security measures.
As an ethical security researcher, I do not download, retain, or share any data I discover. I only take a limited number of screenshots strictly when necessary and solely for verification and documentation purposes. I do not engage in any activities beyond identifying the security vulnerability and, where possible, notifying the relevant parties involved. I expressly disclaim any and all liability from the use, interpretation or reliance on this disclosure. I publish my findings to raise awareness of issues of data security and privacy. My aim is to encourage organizations to proactively implement measures to safeguard sensitive information against unauthorized access.
The publicly exposed database was not password-protected or encrypted. It contained 10,820 records, with a total size of 38 GB. The majority of the files were .csv spreadsheets containing many thousands or hundreds of thousands of rows of PII. In a limited sampling of the exposed files, I saw documents that included PII such as names, physical addresses, email addresses, phone numbers, and lifestyle or ownership information. The records appeared to be a storage repository for client orders labeled “reports” and “results”. Files names indicated these lists were used for multiple purposes, including sales and marketing leads for industries such as insurance, solar, elections, car warranties, hospitals, healthcare providers, and more.
The name of the database as well as the information inside it indicated the records belonged to a Florida-based company called IMDataCenter. The firm provides data append and enhancement solutions designed to improve marketing strategies through lead scoring and identity management. I immediately sent a responsible disclosure notice to IMDataCenter, and the database was restricted from public access soon after and no longer accessible. I received a reply stating “Data security is really important to us too and really appreciate you sharing this information with us. We are working to secure the information ASAP”. Although the records appeared to belong to IMDataCenter, it is not known if the database was owned and managed directly by them, by a third-party contractor, or by an affiliated or related company, including a parent or holding company. It is also not known how long the database was exposed before I discovered it or if anyone else may have gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity.
According to their website, IMDataCenter has a data library built from hundreds of verified public and proprietary online and offline sources; it includes detailed information on over 260 million individuals and 130 million households. It contains 600 million email addresses, 550 million phone numbers (including 230 million mobile numbers), 153 million property records, 208 million deeds, and data on 75 million homeowners.
Based on the file names, the database appeared to hold documents related to campaigns or individual customer orders rather than IMData’s entire data library. In a limited sample, I saw files that contained the contact information of numerous individuals. This information appeared to be intended for a range of marketing or outreach services, such as: the healthcare sector, investor prospects, medicare eligibility, patients, medical supplements, automotive and home ownership, insurance, elections, restaurants, food services, and many more. With each CSV document containing the data of thousands of individuals, it is difficult to calculate the total number of those who may have potentially had their data exposed.
These types of marketing campaigns can be very expensive, so it is important that addresses, emails, and phone numbers are valid. IMData provides a range of data hygiene and validation services to ensure physical mailing addresses are accurate, including USPS change-of-address checks and other types of confirmed contact details.
The exposure of such a large amount of PII, including names, addresses, emails, phone numbers, and other personalized lifestyle data could potentially pose significant privacy and cybersecurity risks. When data is verified and validated, that information can be used not only to identify individuals but also to potentially build detailed personal profiles. These profiles are valuable not only to marketers, but also to criminals who could potentially use that data for targeted phishing attacks, identity theft, or other forms of fraudulent activities.
Validated and active email addresses and phone numbers could be used as working lists for criminals to launch phishing, spam, and scam campaigns. Verified home addresses allow for realistic mail fraud, social engineering, or fake-check scams. The latter are also known as cash-back scams, where the victim receives a counterfeit check, and criminals ask them to return a portion of the money before the bank identifies the check as fake. The potential victim is then responsible for any amount of money they sent to the scammer.
Additionally, criminals often cross-reference previous data breaches looking for additional information or financial accounts, making this kind of dataset potentially valuable for resale on dark web markets. I am not saying that IMData’s clients or the individuals in IMData’s database were ever at risk of these types of fraudulent activities. I am only providing a real-world example of how this data could potentially be exploited if it were to fall into the wrong hands.
My advice to anyone who believes that their personal data may have been exposed in any data breach is to take steps to protect yourself. Be aware of common schemes used by criminals and always be suspicious if something feels off or not right. When it comes to emails, never click on links or provide personal information to unknown senders or unsolicited messages. The same applies to phone calls. Technology has provided scammers with a wide range of tools to deceive their targets. They can spoof phone numbers to appear as if they were calling from a trusted organization or even use deepfake audio to spoof voices.
Physical mail can also be a potential risk because people are more inclined to trust the postal service than the internet, and they tend to assume mail is sent from a trusted source. Always verify that anyone who contacts you with inside or privileged knowledge is who they say they are before sharing your private or financial information. By being suspicious and verifying individuals or businesses asking for personal data, potentially affected individuals can reduce the risk of further harm from most data breaches.
Companies that collect and store large amounts of personal data must invest in cybersecurity and data protection. When processing data is your core business, a breach can be compared to leaking a secret recipe or proprietary code. Remember that all data is valuable. Even if a portion of that data comes from public sources, it can be combined with information from previous breaches and become a critical puzzle piece for criminals to build profiles on individuals.
I recommend that companies routinely encrypt the data they collect to make it non-human readable. Implementing strict access controls and multi-factor authentication can help prevent unauthorized access. Conducting regular security audits, penetration testing, and vulnerability scanning can help identify critical issues and publicly exposed data. It is also a good idea for companies to have a dedicated communication channel for data security and privacy. This way, when customers, partners, or internal staff report suspicious activities or issues, the information will swiftly reach the right person or team.
We are living in a new era of the digital world where personal data is a highly valuable commodity that is bought, sold, and traded by companies. Our personal information and data are often used with very little transparency or accountability, and in some cases, without explicit consent. As we face the reality of our identities and online activities being a valuable product for data brokers and marketing agencies, we must also face the fact that information resellers and the data industry as a whole have far outpaced privacy protections. It is my personal opinion that there needs to be more regulation over digital rights so that individuals may have greater control over how their personal data is collected, used, and shared.
There has been a shift in both legal policies — e.g. California Consumer Privacy Act (CCPA), Virginia Consumer Data Protection Act (VCDPA), Colorado Privacy Act (CPA) — and public awareness when it comes to digital privacy. Unfortunately, it is hard to reverse years of industry practices and perhaps even harder to remove the vast amounts of personal data that is already out there. I am not saying that data brokers and marketing companies do not provide legitimate and valuable services. Companies like IMData ensure that contacts are valid and that those individuals receive important information from companies, civic groups, medical providers, local governments, and many more entities.
I imply no wrongdoing by IMDataCenter, Brooks Integrated Marketing, or their employees, agents, contractors, affiliates, and/or related entities. I do not claim that any internal, employee, customer, or user data was ever at imminent risk. The hypothetical data-risk scenarios I have presented in this report are strictly and exclusively for educational purposes and do not reflect, suggest, or imply any actual compromise of data integrity. It should not be construed as a reflection of or commentary on any organization’s specific practices, systems, or security measures.
As an ethical security researcher, I do not download, retain, or share any data I discover. I only take a limited number of screenshots strictly when necessary and solely for verification and documentation purposes. I do not engage in any activities beyond identifying the security vulnerability and, where possible, notifying the relevant parties involved. I expressly disclaim any and all liability from the use, interpretation or reliance on this disclosure. I publish my findings to raise awareness of issues of data security and privacy. My aim is to encourage organizations to proactively implement measures to safeguard sensitive information against unauthorized access.
What Is Website Planet?
Website Planet stands as the premier resource for web designers, digital marketers, developers, and businesses operating online. We offer a wide array of helpful tools and resources catering to individuals at all skill levels, from beginners to experts. Furthermore, we provide updates on the most recent advancements in cybersecurity.We work with an experienced team of ethical security research experts who uncover and disclose serious data leaks. Recently, cybersecurity expert Jeremiah Fowler discovered and disclosed a non-password protected database which exposed 170k records, presumably belonging to Income Property Investments, a real estate management and investment company. He also found another unsecured database that contained Over 1 million records belonging to Gladney Adoption Center, holding the names of children, birth parents, adopted parents, employees, leads and other internal potentially sensitive information.