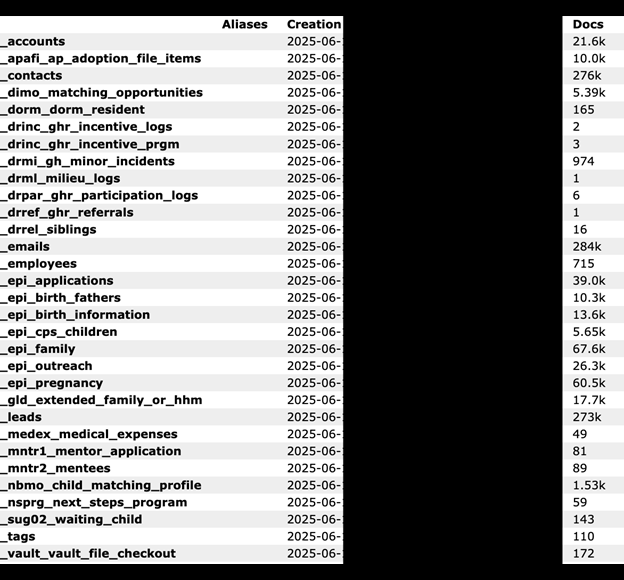
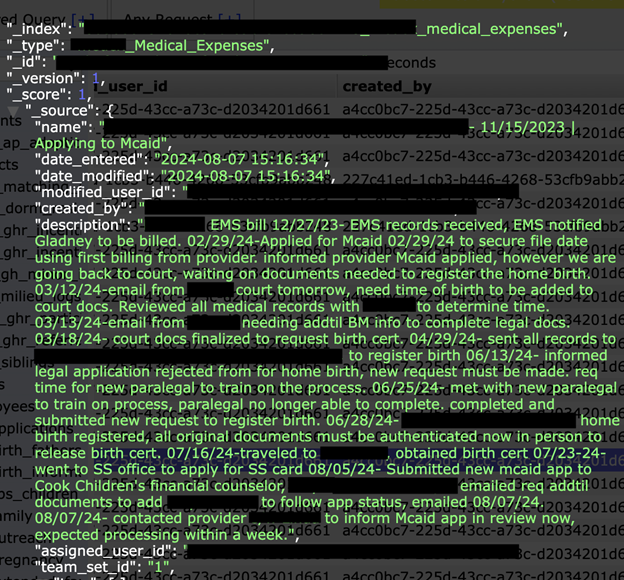
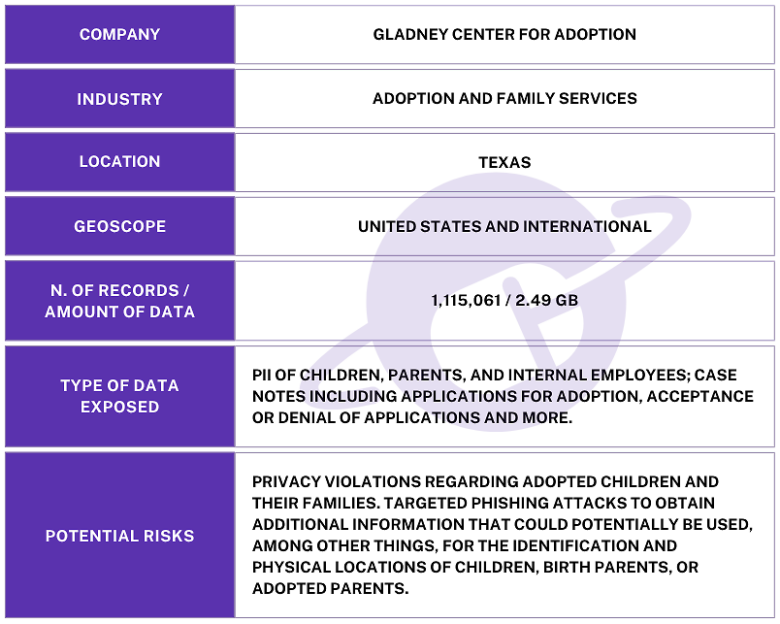
 The publicly exposed database was not password-protected or encrypted. It contained 1,115,061 records with a total size of 2.49 GB. In a limited sampling of the exposed records, I saw documents that included PII, such as names, physical addresses, email addresses, phone numbers, and more. The records appeared to be from a Customer Relationship Management (CRM) system that is used to coordinate and analyze internal and external actions. The records included a mixture of plain text data and Universally Unique Identifiers (UUID).
Information contained in the internal files indicated the records may be linked to a Texas-based organization called Gladney Centre for Adoption, which has reportedly provided adoption and advocacy services for over 130 years. I immediately sent a responsible disclosure notice to Gladney, and the database was restricted from public access the following day and no longer accessible. Although the records appeared to belong to Gladney, it is not known if the database was owned and managed directly by them or by a third-party contractor. I did not receive any reply to my responsible disclosure notice. It is also not known how long the database was exposed before I discovered it or if anyone else may have gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity.
In a folder named “contacts”, there were records that contained first and last names, phone numbers, emails, and physical addresses. These also included notes about their relationship with the organization or reasons they are listed as a contact. The “applications” folder contained just under 39k records that listed the names of individuals and internal notes on their specific case, such as the grounds for denial or approval to become adoptive parents. I saw several cases that indicated substance use or other reasons why the applicants were denied.
An “emails” folder contained 284k records detailing subject lines and who sent the email. Although the full email body was not exposed, some of the subject lines contained names or other identifiable details. In a folder named “Birth Fathers”, I saw many records that detailed first, last, and middle names, which could increase the risk of identifying individuals — many people may share a first and last name, but not a middle name. Some records also included details about the father, such as family circumstances or legal issues, that should not be publicly accessible.
Other folders included internal employee records with names, email addresses, dates modified, and unique identifiers. The database also contained outreach to organizations, social services, or medical professionals that help with child placement or other related services. Additionally, there were folders containing records that cataloged leads, pregnancies, CPS children (Child Protective Services), birth information, dorm residents, medical expenses, and other potentially sensitive information. Although the dates on the records go back many years, there were indications that the storage creation was recent and made only days before my discovery.
The exposed data could be highly valuable to criminals and scammers due to the emotionally sensitive nature of adoptions. The potential risks could include attempting to exploit contacts and personal details to obtain additional information that could hypothetically be used for identity theft, targeted phishing campaigns, or even blackmail. If criminals were to gain access to internal notes related to adoption cases, substance use, legal issues, or other privileged internal data, they might attempt to impersonate adoption agency employees, legal or social services professionals. The parents or clients would have little reason to doubt the requests are legitimate because the criminals could reference information that, theoretically, only the client and the organization would know.
The emotional factors of an adoption could potentially make these individuals more susceptible to fraud methods that prey on fear, urgency, or the need for privacy and confidentiality. I am not stating or implying that Gladney’s clients face these risks, I am only presenting a hypothetical scenario intended to illustrate real-world consequences if sensitive information were to be accessed by unauthorized individuals.
I recommend that any organization that handles potentially sensitive information implement additional security protocols to protect against unauthorized access or accidental data exposures. This includes encrypting all data or documents that may contain personal or health-related information — especially when children are involved. If the data is encrypted, it is not human-readable and basically worthless if it is accidentally leaked. As a security researcher, when I discover encrypted data, I notify the organization it belongs to and move on because I have no idea what it is and no way to decrypt that information.
Another good idea is to enforce strict access controls based on user roles, and ensure that not all internal employees have access to all data. This should also include a time-restricted access policy for potentially sensitive information. Conducting regular vulnerability assessments as well as monitoring user activity and system configurations can identify or help prevent serious data incidents. In cases where internal emails or other information has been exposed, it is important to train internal staff on the basics of data privacy, phishing, and secure handling of potentially sensitive information. Finally, storing only necessary data and archiving older data that is no longer in use can also help reduce the extent of an exposure in the event of a data breach.
It should be noted that the records did not contain full case files, and the publicly exposed records were a combination of plain text and unique identifiers. Each piece of data could be a potential puzzle piece to create a more complete profile of the internal systems, internal users, and Gladney’s clients. From a cybersecurity perspective, a UUID is designed for unique identification, not secrecy, and it can potentially be guessed, reverse-engineered, or enumerated. UUIDs are not recommended to be used to protect sensitive data. Most CRM systems use a UUID as a reference key to uniquely identify a record, such as a user, contact, or file. The CRM software uses it to look up and retrieve the readable data associated with the UUID. While UUIDs may seem like unintelligible characters, they are not secure and cannot replace hashing or encryption of potentially sensitive information.
The goal of my research and reporting is for educational and privacy purposes. I often encounter data that is sensitive and important, but rarely have I seen cases such as this where individuals in vulnerable circumstances are involved and the exposed data is so emotionally complex. I want to commend the good work that organizations like Gladney do to help children and families, while underscoring the importance of cybersecurity and data protection.
In situations that involve adoption and vulnerable children, it is essential to preserve their privacy and confidentiality. Protecting the personal information of those individuals that an organization serves is equally as valuable as the products or services it provides. Many organizations that work with real people offline now use technology to manage and store important data — and this can be a point of weakness from a security perspective. This discovery should serve as a reminder that cyber security should be a core priority of every business.
Gladney has a long and proven history of helping children, parents, and families. Those looking to adopt or give a child up for adoption should do their research and use a known, reputable, and experienced service like Gladney to avoid scams. According to the National Council for Adoption in the United States, adoptions are primarily regulated at the state level, with each state establishing their own rules and procedures. While international adoptions are subject to federal oversight (particularly in areas such as accreditation and compliance), there is no single, nationwide adoption code. The FBI has issued guidance on unethical adoption service providers and how to avoid adoption fraud.
Tactics of unethical adoption providers may include assigning the same child to multiple families, inventing non-existent birth mothers, charging excessive fees, sharing unverifiable credentials, having inconsistent communication, making upfront financial demands, or making misleading promises about the adoption timeline or outcome. Birth parents should be cautious of coercion, lack of choice in selecting adoptive families, and threats tied to financial reimbursements if they reconsider their decision.
I imply no wrongdoing by Gladney Center for Adoption, or its employees, agents, contractors, affiliates, and/or related entities. I do not claim that any internal, employee, customer, or user data was ever at imminent risk. The hypothetical data-risk scenarios I have presented in this report are strictly and exclusively for educational purposes and do not reflect, suggest, or imply any actual compromise of data integrity. It should not be construed as a reflection of or commentary on any organization’s specific practices, systems, or security measures.
As an ethical security researcher, I do not download, retain, or share any data I discover. I only take a limited number of screenshots when necessary and solely for verification and documentation purposes. I do not engage in any activities beyond identifying the security vulnerability and, where possible, notifying the relevant parties involved. I disclaim any and all liability for any and all actions that may be taken as a result of this disclosure. I publish my findings to raise awareness of issues of data security and privacy. My aim is to encourage organizations to proactively implement measures to safeguard sensitive information against unauthorized access.
The publicly exposed database was not password-protected or encrypted. It contained 1,115,061 records with a total size of 2.49 GB. In a limited sampling of the exposed records, I saw documents that included PII, such as names, physical addresses, email addresses, phone numbers, and more. The records appeared to be from a Customer Relationship Management (CRM) system that is used to coordinate and analyze internal and external actions. The records included a mixture of plain text data and Universally Unique Identifiers (UUID).
Information contained in the internal files indicated the records may be linked to a Texas-based organization called Gladney Centre for Adoption, which has reportedly provided adoption and advocacy services for over 130 years. I immediately sent a responsible disclosure notice to Gladney, and the database was restricted from public access the following day and no longer accessible. Although the records appeared to belong to Gladney, it is not known if the database was owned and managed directly by them or by a third-party contractor. I did not receive any reply to my responsible disclosure notice. It is also not known how long the database was exposed before I discovered it or if anyone else may have gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity.
In a folder named “contacts”, there were records that contained first and last names, phone numbers, emails, and physical addresses. These also included notes about their relationship with the organization or reasons they are listed as a contact. The “applications” folder contained just under 39k records that listed the names of individuals and internal notes on their specific case, such as the grounds for denial or approval to become adoptive parents. I saw several cases that indicated substance use or other reasons why the applicants were denied.
An “emails” folder contained 284k records detailing subject lines and who sent the email. Although the full email body was not exposed, some of the subject lines contained names or other identifiable details. In a folder named “Birth Fathers”, I saw many records that detailed first, last, and middle names, which could increase the risk of identifying individuals — many people may share a first and last name, but not a middle name. Some records also included details about the father, such as family circumstances or legal issues, that should not be publicly accessible.
Other folders included internal employee records with names, email addresses, dates modified, and unique identifiers. The database also contained outreach to organizations, social services, or medical professionals that help with child placement or other related services. Additionally, there were folders containing records that cataloged leads, pregnancies, CPS children (Child Protective Services), birth information, dorm residents, medical expenses, and other potentially sensitive information. Although the dates on the records go back many years, there were indications that the storage creation was recent and made only days before my discovery.
The exposed data could be highly valuable to criminals and scammers due to the emotionally sensitive nature of adoptions. The potential risks could include attempting to exploit contacts and personal details to obtain additional information that could hypothetically be used for identity theft, targeted phishing campaigns, or even blackmail. If criminals were to gain access to internal notes related to adoption cases, substance use, legal issues, or other privileged internal data, they might attempt to impersonate adoption agency employees, legal or social services professionals. The parents or clients would have little reason to doubt the requests are legitimate because the criminals could reference information that, theoretically, only the client and the organization would know.
The emotional factors of an adoption could potentially make these individuals more susceptible to fraud methods that prey on fear, urgency, or the need for privacy and confidentiality. I am not stating or implying that Gladney’s clients face these risks, I am only presenting a hypothetical scenario intended to illustrate real-world consequences if sensitive information were to be accessed by unauthorized individuals.
I recommend that any organization that handles potentially sensitive information implement additional security protocols to protect against unauthorized access or accidental data exposures. This includes encrypting all data or documents that may contain personal or health-related information — especially when children are involved. If the data is encrypted, it is not human-readable and basically worthless if it is accidentally leaked. As a security researcher, when I discover encrypted data, I notify the organization it belongs to and move on because I have no idea what it is and no way to decrypt that information.
Another good idea is to enforce strict access controls based on user roles, and ensure that not all internal employees have access to all data. This should also include a time-restricted access policy for potentially sensitive information. Conducting regular vulnerability assessments as well as monitoring user activity and system configurations can identify or help prevent serious data incidents. In cases where internal emails or other information has been exposed, it is important to train internal staff on the basics of data privacy, phishing, and secure handling of potentially sensitive information. Finally, storing only necessary data and archiving older data that is no longer in use can also help reduce the extent of an exposure in the event of a data breach.
It should be noted that the records did not contain full case files, and the publicly exposed records were a combination of plain text and unique identifiers. Each piece of data could be a potential puzzle piece to create a more complete profile of the internal systems, internal users, and Gladney’s clients. From a cybersecurity perspective, a UUID is designed for unique identification, not secrecy, and it can potentially be guessed, reverse-engineered, or enumerated. UUIDs are not recommended to be used to protect sensitive data. Most CRM systems use a UUID as a reference key to uniquely identify a record, such as a user, contact, or file. The CRM software uses it to look up and retrieve the readable data associated with the UUID. While UUIDs may seem like unintelligible characters, they are not secure and cannot replace hashing or encryption of potentially sensitive information.
The goal of my research and reporting is for educational and privacy purposes. I often encounter data that is sensitive and important, but rarely have I seen cases such as this where individuals in vulnerable circumstances are involved and the exposed data is so emotionally complex. I want to commend the good work that organizations like Gladney do to help children and families, while underscoring the importance of cybersecurity and data protection.
In situations that involve adoption and vulnerable children, it is essential to preserve their privacy and confidentiality. Protecting the personal information of those individuals that an organization serves is equally as valuable as the products or services it provides. Many organizations that work with real people offline now use technology to manage and store important data — and this can be a point of weakness from a security perspective. This discovery should serve as a reminder that cyber security should be a core priority of every business.
Gladney has a long and proven history of helping children, parents, and families. Those looking to adopt or give a child up for adoption should do their research and use a known, reputable, and experienced service like Gladney to avoid scams. According to the National Council for Adoption in the United States, adoptions are primarily regulated at the state level, with each state establishing their own rules and procedures. While international adoptions are subject to federal oversight (particularly in areas such as accreditation and compliance), there is no single, nationwide adoption code. The FBI has issued guidance on unethical adoption service providers and how to avoid adoption fraud.
Tactics of unethical adoption providers may include assigning the same child to multiple families, inventing non-existent birth mothers, charging excessive fees, sharing unverifiable credentials, having inconsistent communication, making upfront financial demands, or making misleading promises about the adoption timeline or outcome. Birth parents should be cautious of coercion, lack of choice in selecting adoptive families, and threats tied to financial reimbursements if they reconsider their decision.
I imply no wrongdoing by Gladney Center for Adoption, or its employees, agents, contractors, affiliates, and/or related entities. I do not claim that any internal, employee, customer, or user data was ever at imminent risk. The hypothetical data-risk scenarios I have presented in this report are strictly and exclusively for educational purposes and do not reflect, suggest, or imply any actual compromise of data integrity. It should not be construed as a reflection of or commentary on any organization’s specific practices, systems, or security measures.
As an ethical security researcher, I do not download, retain, or share any data I discover. I only take a limited number of screenshots when necessary and solely for verification and documentation purposes. I do not engage in any activities beyond identifying the security vulnerability and, where possible, notifying the relevant parties involved. I disclaim any and all liability for any and all actions that may be taken as a result of this disclosure. I publish my findings to raise awareness of issues of data security and privacy. My aim is to encourage organizations to proactively implement measures to safeguard sensitive information against unauthorized access.

Over One Million Records Exposed in Data Breach Involving Adoption Agency
Cybersecurity Researcher, Jeremiah Fowler, discovered and reported to Website Planet about an unencrypted and non-password-protected database that contained 1,115,061 records. The database was associated with a well-known adoption agency, holding the names of children, birth parents, adopted parents, employees, leads, and other internal potentially sensitive information.
 The publicly exposed database was not password-protected or encrypted. It contained 1,115,061 records with a total size of 2.49 GB. In a limited sampling of the exposed records, I saw documents that included PII, such as names, physical addresses, email addresses, phone numbers, and more. The records appeared to be from a Customer Relationship Management (CRM) system that is used to coordinate and analyze internal and external actions. The records included a mixture of plain text data and Universally Unique Identifiers (UUID).
Information contained in the internal files indicated the records may be linked to a Texas-based organization called Gladney Centre for Adoption, which has reportedly provided adoption and advocacy services for over 130 years. I immediately sent a responsible disclosure notice to Gladney, and the database was restricted from public access the following day and no longer accessible. Although the records appeared to belong to Gladney, it is not known if the database was owned and managed directly by them or by a third-party contractor. I did not receive any reply to my responsible disclosure notice. It is also not known how long the database was exposed before I discovered it or if anyone else may have gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity.
In a folder named “contacts”, there were records that contained first and last names, phone numbers, emails, and physical addresses. These also included notes about their relationship with the organization or reasons they are listed as a contact. The “applications” folder contained just under 39k records that listed the names of individuals and internal notes on their specific case, such as the grounds for denial or approval to become adoptive parents. I saw several cases that indicated substance use or other reasons why the applicants were denied.
An “emails” folder contained 284k records detailing subject lines and who sent the email. Although the full email body was not exposed, some of the subject lines contained names or other identifiable details. In a folder named “Birth Fathers”, I saw many records that detailed first, last, and middle names, which could increase the risk of identifying individuals — many people may share a first and last name, but not a middle name. Some records also included details about the father, such as family circumstances or legal issues, that should not be publicly accessible.
Other folders included internal employee records with names, email addresses, dates modified, and unique identifiers. The database also contained outreach to organizations, social services, or medical professionals that help with child placement or other related services. Additionally, there were folders containing records that cataloged leads, pregnancies, CPS children (Child Protective Services), birth information, dorm residents, medical expenses, and other potentially sensitive information. Although the dates on the records go back many years, there were indications that the storage creation was recent and made only days before my discovery.
The exposed data could be highly valuable to criminals and scammers due to the emotionally sensitive nature of adoptions. The potential risks could include attempting to exploit contacts and personal details to obtain additional information that could hypothetically be used for identity theft, targeted phishing campaigns, or even blackmail. If criminals were to gain access to internal notes related to adoption cases, substance use, legal issues, or other privileged internal data, they might attempt to impersonate adoption agency employees, legal or social services professionals. The parents or clients would have little reason to doubt the requests are legitimate because the criminals could reference information that, theoretically, only the client and the organization would know.
The emotional factors of an adoption could potentially make these individuals more susceptible to fraud methods that prey on fear, urgency, or the need for privacy and confidentiality. I am not stating or implying that Gladney’s clients face these risks, I am only presenting a hypothetical scenario intended to illustrate real-world consequences if sensitive information were to be accessed by unauthorized individuals.
I recommend that any organization that handles potentially sensitive information implement additional security protocols to protect against unauthorized access or accidental data exposures. This includes encrypting all data or documents that may contain personal or health-related information — especially when children are involved. If the data is encrypted, it is not human-readable and basically worthless if it is accidentally leaked. As a security researcher, when I discover encrypted data, I notify the organization it belongs to and move on because I have no idea what it is and no way to decrypt that information.
Another good idea is to enforce strict access controls based on user roles, and ensure that not all internal employees have access to all data. This should also include a time-restricted access policy for potentially sensitive information. Conducting regular vulnerability assessments as well as monitoring user activity and system configurations can identify or help prevent serious data incidents. In cases where internal emails or other information has been exposed, it is important to train internal staff on the basics of data privacy, phishing, and secure handling of potentially sensitive information. Finally, storing only necessary data and archiving older data that is no longer in use can also help reduce the extent of an exposure in the event of a data breach.
It should be noted that the records did not contain full case files, and the publicly exposed records were a combination of plain text and unique identifiers. Each piece of data could be a potential puzzle piece to create a more complete profile of the internal systems, internal users, and Gladney’s clients. From a cybersecurity perspective, a UUID is designed for unique identification, not secrecy, and it can potentially be guessed, reverse-engineered, or enumerated. UUIDs are not recommended to be used to protect sensitive data. Most CRM systems use a UUID as a reference key to uniquely identify a record, such as a user, contact, or file. The CRM software uses it to look up and retrieve the readable data associated with the UUID. While UUIDs may seem like unintelligible characters, they are not secure and cannot replace hashing or encryption of potentially sensitive information.
The goal of my research and reporting is for educational and privacy purposes. I often encounter data that is sensitive and important, but rarely have I seen cases such as this where individuals in vulnerable circumstances are involved and the exposed data is so emotionally complex. I want to commend the good work that organizations like Gladney do to help children and families, while underscoring the importance of cybersecurity and data protection.
In situations that involve adoption and vulnerable children, it is essential to preserve their privacy and confidentiality. Protecting the personal information of those individuals that an organization serves is equally as valuable as the products or services it provides. Many organizations that work with real people offline now use technology to manage and store important data — and this can be a point of weakness from a security perspective. This discovery should serve as a reminder that cyber security should be a core priority of every business.
Gladney has a long and proven history of helping children, parents, and families. Those looking to adopt or give a child up for adoption should do their research and use a known, reputable, and experienced service like Gladney to avoid scams. According to the National Council for Adoption in the United States, adoptions are primarily regulated at the state level, with each state establishing their own rules and procedures. While international adoptions are subject to federal oversight (particularly in areas such as accreditation and compliance), there is no single, nationwide adoption code. The FBI has issued guidance on unethical adoption service providers and how to avoid adoption fraud.
Tactics of unethical adoption providers may include assigning the same child to multiple families, inventing non-existent birth mothers, charging excessive fees, sharing unverifiable credentials, having inconsistent communication, making upfront financial demands, or making misleading promises about the adoption timeline or outcome. Birth parents should be cautious of coercion, lack of choice in selecting adoptive families, and threats tied to financial reimbursements if they reconsider their decision.
I imply no wrongdoing by Gladney Center for Adoption, or its employees, agents, contractors, affiliates, and/or related entities. I do not claim that any internal, employee, customer, or user data was ever at imminent risk. The hypothetical data-risk scenarios I have presented in this report are strictly and exclusively for educational purposes and do not reflect, suggest, or imply any actual compromise of data integrity. It should not be construed as a reflection of or commentary on any organization’s specific practices, systems, or security measures.
As an ethical security researcher, I do not download, retain, or share any data I discover. I only take a limited number of screenshots when necessary and solely for verification and documentation purposes. I do not engage in any activities beyond identifying the security vulnerability and, where possible, notifying the relevant parties involved. I disclaim any and all liability for any and all actions that may be taken as a result of this disclosure. I publish my findings to raise awareness of issues of data security and privacy. My aim is to encourage organizations to proactively implement measures to safeguard sensitive information against unauthorized access.
The publicly exposed database was not password-protected or encrypted. It contained 1,115,061 records with a total size of 2.49 GB. In a limited sampling of the exposed records, I saw documents that included PII, such as names, physical addresses, email addresses, phone numbers, and more. The records appeared to be from a Customer Relationship Management (CRM) system that is used to coordinate and analyze internal and external actions. The records included a mixture of plain text data and Universally Unique Identifiers (UUID).
Information contained in the internal files indicated the records may be linked to a Texas-based organization called Gladney Centre for Adoption, which has reportedly provided adoption and advocacy services for over 130 years. I immediately sent a responsible disclosure notice to Gladney, and the database was restricted from public access the following day and no longer accessible. Although the records appeared to belong to Gladney, it is not known if the database was owned and managed directly by them or by a third-party contractor. I did not receive any reply to my responsible disclosure notice. It is also not known how long the database was exposed before I discovered it or if anyone else may have gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity.
In a folder named “contacts”, there were records that contained first and last names, phone numbers, emails, and physical addresses. These also included notes about their relationship with the organization or reasons they are listed as a contact. The “applications” folder contained just under 39k records that listed the names of individuals and internal notes on their specific case, such as the grounds for denial or approval to become adoptive parents. I saw several cases that indicated substance use or other reasons why the applicants were denied.
An “emails” folder contained 284k records detailing subject lines and who sent the email. Although the full email body was not exposed, some of the subject lines contained names or other identifiable details. In a folder named “Birth Fathers”, I saw many records that detailed first, last, and middle names, which could increase the risk of identifying individuals — many people may share a first and last name, but not a middle name. Some records also included details about the father, such as family circumstances or legal issues, that should not be publicly accessible.
Other folders included internal employee records with names, email addresses, dates modified, and unique identifiers. The database also contained outreach to organizations, social services, or medical professionals that help with child placement or other related services. Additionally, there were folders containing records that cataloged leads, pregnancies, CPS children (Child Protective Services), birth information, dorm residents, medical expenses, and other potentially sensitive information. Although the dates on the records go back many years, there were indications that the storage creation was recent and made only days before my discovery.
The exposed data could be highly valuable to criminals and scammers due to the emotionally sensitive nature of adoptions. The potential risks could include attempting to exploit contacts and personal details to obtain additional information that could hypothetically be used for identity theft, targeted phishing campaigns, or even blackmail. If criminals were to gain access to internal notes related to adoption cases, substance use, legal issues, or other privileged internal data, they might attempt to impersonate adoption agency employees, legal or social services professionals. The parents or clients would have little reason to doubt the requests are legitimate because the criminals could reference information that, theoretically, only the client and the organization would know.
The emotional factors of an adoption could potentially make these individuals more susceptible to fraud methods that prey on fear, urgency, or the need for privacy and confidentiality. I am not stating or implying that Gladney’s clients face these risks, I am only presenting a hypothetical scenario intended to illustrate real-world consequences if sensitive information were to be accessed by unauthorized individuals.
I recommend that any organization that handles potentially sensitive information implement additional security protocols to protect against unauthorized access or accidental data exposures. This includes encrypting all data or documents that may contain personal or health-related information — especially when children are involved. If the data is encrypted, it is not human-readable and basically worthless if it is accidentally leaked. As a security researcher, when I discover encrypted data, I notify the organization it belongs to and move on because I have no idea what it is and no way to decrypt that information.
Another good idea is to enforce strict access controls based on user roles, and ensure that not all internal employees have access to all data. This should also include a time-restricted access policy for potentially sensitive information. Conducting regular vulnerability assessments as well as monitoring user activity and system configurations can identify or help prevent serious data incidents. In cases where internal emails or other information has been exposed, it is important to train internal staff on the basics of data privacy, phishing, and secure handling of potentially sensitive information. Finally, storing only necessary data and archiving older data that is no longer in use can also help reduce the extent of an exposure in the event of a data breach.
It should be noted that the records did not contain full case files, and the publicly exposed records were a combination of plain text and unique identifiers. Each piece of data could be a potential puzzle piece to create a more complete profile of the internal systems, internal users, and Gladney’s clients. From a cybersecurity perspective, a UUID is designed for unique identification, not secrecy, and it can potentially be guessed, reverse-engineered, or enumerated. UUIDs are not recommended to be used to protect sensitive data. Most CRM systems use a UUID as a reference key to uniquely identify a record, such as a user, contact, or file. The CRM software uses it to look up and retrieve the readable data associated with the UUID. While UUIDs may seem like unintelligible characters, they are not secure and cannot replace hashing or encryption of potentially sensitive information.
The goal of my research and reporting is for educational and privacy purposes. I often encounter data that is sensitive and important, but rarely have I seen cases such as this where individuals in vulnerable circumstances are involved and the exposed data is so emotionally complex. I want to commend the good work that organizations like Gladney do to help children and families, while underscoring the importance of cybersecurity and data protection.
In situations that involve adoption and vulnerable children, it is essential to preserve their privacy and confidentiality. Protecting the personal information of those individuals that an organization serves is equally as valuable as the products or services it provides. Many organizations that work with real people offline now use technology to manage and store important data — and this can be a point of weakness from a security perspective. This discovery should serve as a reminder that cyber security should be a core priority of every business.
Gladney has a long and proven history of helping children, parents, and families. Those looking to adopt or give a child up for adoption should do their research and use a known, reputable, and experienced service like Gladney to avoid scams. According to the National Council for Adoption in the United States, adoptions are primarily regulated at the state level, with each state establishing their own rules and procedures. While international adoptions are subject to federal oversight (particularly in areas such as accreditation and compliance), there is no single, nationwide adoption code. The FBI has issued guidance on unethical adoption service providers and how to avoid adoption fraud.
Tactics of unethical adoption providers may include assigning the same child to multiple families, inventing non-existent birth mothers, charging excessive fees, sharing unverifiable credentials, having inconsistent communication, making upfront financial demands, or making misleading promises about the adoption timeline or outcome. Birth parents should be cautious of coercion, lack of choice in selecting adoptive families, and threats tied to financial reimbursements if they reconsider their decision.
I imply no wrongdoing by Gladney Center for Adoption, or its employees, agents, contractors, affiliates, and/or related entities. I do not claim that any internal, employee, customer, or user data was ever at imminent risk. The hypothetical data-risk scenarios I have presented in this report are strictly and exclusively for educational purposes and do not reflect, suggest, or imply any actual compromise of data integrity. It should not be construed as a reflection of or commentary on any organization’s specific practices, systems, or security measures.
As an ethical security researcher, I do not download, retain, or share any data I discover. I only take a limited number of screenshots when necessary and solely for verification and documentation purposes. I do not engage in any activities beyond identifying the security vulnerability and, where possible, notifying the relevant parties involved. I disclaim any and all liability for any and all actions that may be taken as a result of this disclosure. I publish my findings to raise awareness of issues of data security and privacy. My aim is to encourage organizations to proactively implement measures to safeguard sensitive information against unauthorized access.
 The publicly exposed database was not password-protected or encrypted. It contained 1,115,061 records with a total size of 2.49 GB. In a limited sampling of the exposed records, I saw documents that included PII, such as names, physical addresses, email addresses, phone numbers, and more. The records appeared to be from a Customer Relationship Management (CRM) system that is used to coordinate and analyze internal and external actions. The records included a mixture of plain text data and Universally Unique Identifiers (UUID).
Information contained in the internal files indicated the records may be linked to a Texas-based organization called Gladney Centre for Adoption, which has reportedly provided adoption and advocacy services for over 130 years. I immediately sent a responsible disclosure notice to Gladney, and the database was restricted from public access the following day and no longer accessible. Although the records appeared to belong to Gladney, it is not known if the database was owned and managed directly by them or by a third-party contractor. I did not receive any reply to my responsible disclosure notice. It is also not known how long the database was exposed before I discovered it or if anyone else may have gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity.
In a folder named “contacts”, there were records that contained first and last names, phone numbers, emails, and physical addresses. These also included notes about their relationship with the organization or reasons they are listed as a contact. The “applications” folder contained just under 39k records that listed the names of individuals and internal notes on their specific case, such as the grounds for denial or approval to become adoptive parents. I saw several cases that indicated substance use or other reasons why the applicants were denied.
An “emails” folder contained 284k records detailing subject lines and who sent the email. Although the full email body was not exposed, some of the subject lines contained names or other identifiable details. In a folder named “Birth Fathers”, I saw many records that detailed first, last, and middle names, which could increase the risk of identifying individuals — many people may share a first and last name, but not a middle name. Some records also included details about the father, such as family circumstances or legal issues, that should not be publicly accessible.
Other folders included internal employee records with names, email addresses, dates modified, and unique identifiers. The database also contained outreach to organizations, social services, or medical professionals that help with child placement or other related services. Additionally, there were folders containing records that cataloged leads, pregnancies, CPS children (Child Protective Services), birth information, dorm residents, medical expenses, and other potentially sensitive information. Although the dates on the records go back many years, there were indications that the storage creation was recent and made only days before my discovery.
The exposed data could be highly valuable to criminals and scammers due to the emotionally sensitive nature of adoptions. The potential risks could include attempting to exploit contacts and personal details to obtain additional information that could hypothetically be used for identity theft, targeted phishing campaigns, or even blackmail. If criminals were to gain access to internal notes related to adoption cases, substance use, legal issues, or other privileged internal data, they might attempt to impersonate adoption agency employees, legal or social services professionals. The parents or clients would have little reason to doubt the requests are legitimate because the criminals could reference information that, theoretically, only the client and the organization would know.
The emotional factors of an adoption could potentially make these individuals more susceptible to fraud methods that prey on fear, urgency, or the need for privacy and confidentiality. I am not stating or implying that Gladney’s clients face these risks, I am only presenting a hypothetical scenario intended to illustrate real-world consequences if sensitive information were to be accessed by unauthorized individuals.
I recommend that any organization that handles potentially sensitive information implement additional security protocols to protect against unauthorized access or accidental data exposures. This includes encrypting all data or documents that may contain personal or health-related information — especially when children are involved. If the data is encrypted, it is not human-readable and basically worthless if it is accidentally leaked. As a security researcher, when I discover encrypted data, I notify the organization it belongs to and move on because I have no idea what it is and no way to decrypt that information.
Another good idea is to enforce strict access controls based on user roles, and ensure that not all internal employees have access to all data. This should also include a time-restricted access policy for potentially sensitive information. Conducting regular vulnerability assessments as well as monitoring user activity and system configurations can identify or help prevent serious data incidents. In cases where internal emails or other information has been exposed, it is important to train internal staff on the basics of data privacy, phishing, and secure handling of potentially sensitive information. Finally, storing only necessary data and archiving older data that is no longer in use can also help reduce the extent of an exposure in the event of a data breach.
It should be noted that the records did not contain full case files, and the publicly exposed records were a combination of plain text and unique identifiers. Each piece of data could be a potential puzzle piece to create a more complete profile of the internal systems, internal users, and Gladney’s clients. From a cybersecurity perspective, a UUID is designed for unique identification, not secrecy, and it can potentially be guessed, reverse-engineered, or enumerated. UUIDs are not recommended to be used to protect sensitive data. Most CRM systems use a UUID as a reference key to uniquely identify a record, such as a user, contact, or file. The CRM software uses it to look up and retrieve the readable data associated with the UUID. While UUIDs may seem like unintelligible characters, they are not secure and cannot replace hashing or encryption of potentially sensitive information.
The goal of my research and reporting is for educational and privacy purposes. I often encounter data that is sensitive and important, but rarely have I seen cases such as this where individuals in vulnerable circumstances are involved and the exposed data is so emotionally complex. I want to commend the good work that organizations like Gladney do to help children and families, while underscoring the importance of cybersecurity and data protection.
In situations that involve adoption and vulnerable children, it is essential to preserve their privacy and confidentiality. Protecting the personal information of those individuals that an organization serves is equally as valuable as the products or services it provides. Many organizations that work with real people offline now use technology to manage and store important data — and this can be a point of weakness from a security perspective. This discovery should serve as a reminder that cyber security should be a core priority of every business.
Gladney has a long and proven history of helping children, parents, and families. Those looking to adopt or give a child up for adoption should do their research and use a known, reputable, and experienced service like Gladney to avoid scams. According to the National Council for Adoption in the United States, adoptions are primarily regulated at the state level, with each state establishing their own rules and procedures. While international adoptions are subject to federal oversight (particularly in areas such as accreditation and compliance), there is no single, nationwide adoption code. The FBI has issued guidance on unethical adoption service providers and how to avoid adoption fraud.
Tactics of unethical adoption providers may include assigning the same child to multiple families, inventing non-existent birth mothers, charging excessive fees, sharing unverifiable credentials, having inconsistent communication, making upfront financial demands, or making misleading promises about the adoption timeline or outcome. Birth parents should be cautious of coercion, lack of choice in selecting adoptive families, and threats tied to financial reimbursements if they reconsider their decision.
I imply no wrongdoing by Gladney Center for Adoption, or its employees, agents, contractors, affiliates, and/or related entities. I do not claim that any internal, employee, customer, or user data was ever at imminent risk. The hypothetical data-risk scenarios I have presented in this report are strictly and exclusively for educational purposes and do not reflect, suggest, or imply any actual compromise of data integrity. It should not be construed as a reflection of or commentary on any organization’s specific practices, systems, or security measures.
As an ethical security researcher, I do not download, retain, or share any data I discover. I only take a limited number of screenshots when necessary and solely for verification and documentation purposes. I do not engage in any activities beyond identifying the security vulnerability and, where possible, notifying the relevant parties involved. I disclaim any and all liability for any and all actions that may be taken as a result of this disclosure. I publish my findings to raise awareness of issues of data security and privacy. My aim is to encourage organizations to proactively implement measures to safeguard sensitive information against unauthorized access.
The publicly exposed database was not password-protected or encrypted. It contained 1,115,061 records with a total size of 2.49 GB. In a limited sampling of the exposed records, I saw documents that included PII, such as names, physical addresses, email addresses, phone numbers, and more. The records appeared to be from a Customer Relationship Management (CRM) system that is used to coordinate and analyze internal and external actions. The records included a mixture of plain text data and Universally Unique Identifiers (UUID).
Information contained in the internal files indicated the records may be linked to a Texas-based organization called Gladney Centre for Adoption, which has reportedly provided adoption and advocacy services for over 130 years. I immediately sent a responsible disclosure notice to Gladney, and the database was restricted from public access the following day and no longer accessible. Although the records appeared to belong to Gladney, it is not known if the database was owned and managed directly by them or by a third-party contractor. I did not receive any reply to my responsible disclosure notice. It is also not known how long the database was exposed before I discovered it or if anyone else may have gained access to it. Only an internal forensic audit could identify additional access or potentially suspicious activity.
In a folder named “contacts”, there were records that contained first and last names, phone numbers, emails, and physical addresses. These also included notes about their relationship with the organization or reasons they are listed as a contact. The “applications” folder contained just under 39k records that listed the names of individuals and internal notes on their specific case, such as the grounds for denial or approval to become adoptive parents. I saw several cases that indicated substance use or other reasons why the applicants were denied.
An “emails” folder contained 284k records detailing subject lines and who sent the email. Although the full email body was not exposed, some of the subject lines contained names or other identifiable details. In a folder named “Birth Fathers”, I saw many records that detailed first, last, and middle names, which could increase the risk of identifying individuals — many people may share a first and last name, but not a middle name. Some records also included details about the father, such as family circumstances or legal issues, that should not be publicly accessible.
Other folders included internal employee records with names, email addresses, dates modified, and unique identifiers. The database also contained outreach to organizations, social services, or medical professionals that help with child placement or other related services. Additionally, there were folders containing records that cataloged leads, pregnancies, CPS children (Child Protective Services), birth information, dorm residents, medical expenses, and other potentially sensitive information. Although the dates on the records go back many years, there were indications that the storage creation was recent and made only days before my discovery.
The exposed data could be highly valuable to criminals and scammers due to the emotionally sensitive nature of adoptions. The potential risks could include attempting to exploit contacts and personal details to obtain additional information that could hypothetically be used for identity theft, targeted phishing campaigns, or even blackmail. If criminals were to gain access to internal notes related to adoption cases, substance use, legal issues, or other privileged internal data, they might attempt to impersonate adoption agency employees, legal or social services professionals. The parents or clients would have little reason to doubt the requests are legitimate because the criminals could reference information that, theoretically, only the client and the organization would know.
The emotional factors of an adoption could potentially make these individuals more susceptible to fraud methods that prey on fear, urgency, or the need for privacy and confidentiality. I am not stating or implying that Gladney’s clients face these risks, I am only presenting a hypothetical scenario intended to illustrate real-world consequences if sensitive information were to be accessed by unauthorized individuals.
I recommend that any organization that handles potentially sensitive information implement additional security protocols to protect against unauthorized access or accidental data exposures. This includes encrypting all data or documents that may contain personal or health-related information — especially when children are involved. If the data is encrypted, it is not human-readable and basically worthless if it is accidentally leaked. As a security researcher, when I discover encrypted data, I notify the organization it belongs to and move on because I have no idea what it is and no way to decrypt that information.
Another good idea is to enforce strict access controls based on user roles, and ensure that not all internal employees have access to all data. This should also include a time-restricted access policy for potentially sensitive information. Conducting regular vulnerability assessments as well as monitoring user activity and system configurations can identify or help prevent serious data incidents. In cases where internal emails or other information has been exposed, it is important to train internal staff on the basics of data privacy, phishing, and secure handling of potentially sensitive information. Finally, storing only necessary data and archiving older data that is no longer in use can also help reduce the extent of an exposure in the event of a data breach.
It should be noted that the records did not contain full case files, and the publicly exposed records were a combination of plain text and unique identifiers. Each piece of data could be a potential puzzle piece to create a more complete profile of the internal systems, internal users, and Gladney’s clients. From a cybersecurity perspective, a UUID is designed for unique identification, not secrecy, and it can potentially be guessed, reverse-engineered, or enumerated. UUIDs are not recommended to be used to protect sensitive data. Most CRM systems use a UUID as a reference key to uniquely identify a record, such as a user, contact, or file. The CRM software uses it to look up and retrieve the readable data associated with the UUID. While UUIDs may seem like unintelligible characters, they are not secure and cannot replace hashing or encryption of potentially sensitive information.
The goal of my research and reporting is for educational and privacy purposes. I often encounter data that is sensitive and important, but rarely have I seen cases such as this where individuals in vulnerable circumstances are involved and the exposed data is so emotionally complex. I want to commend the good work that organizations like Gladney do to help children and families, while underscoring the importance of cybersecurity and data protection.
In situations that involve adoption and vulnerable children, it is essential to preserve their privacy and confidentiality. Protecting the personal information of those individuals that an organization serves is equally as valuable as the products or services it provides. Many organizations that work with real people offline now use technology to manage and store important data — and this can be a point of weakness from a security perspective. This discovery should serve as a reminder that cyber security should be a core priority of every business.
Gladney has a long and proven history of helping children, parents, and families. Those looking to adopt or give a child up for adoption should do their research and use a known, reputable, and experienced service like Gladney to avoid scams. According to the National Council for Adoption in the United States, adoptions are primarily regulated at the state level, with each state establishing their own rules and procedures. While international adoptions are subject to federal oversight (particularly in areas such as accreditation and compliance), there is no single, nationwide adoption code. The FBI has issued guidance on unethical adoption service providers and how to avoid adoption fraud.
Tactics of unethical adoption providers may include assigning the same child to multiple families, inventing non-existent birth mothers, charging excessive fees, sharing unverifiable credentials, having inconsistent communication, making upfront financial demands, or making misleading promises about the adoption timeline or outcome. Birth parents should be cautious of coercion, lack of choice in selecting adoptive families, and threats tied to financial reimbursements if they reconsider their decision.
I imply no wrongdoing by Gladney Center for Adoption, or its employees, agents, contractors, affiliates, and/or related entities. I do not claim that any internal, employee, customer, or user data was ever at imminent risk. The hypothetical data-risk scenarios I have presented in this report are strictly and exclusively for educational purposes and do not reflect, suggest, or imply any actual compromise of data integrity. It should not be construed as a reflection of or commentary on any organization’s specific practices, systems, or security measures.
As an ethical security researcher, I do not download, retain, or share any data I discover. I only take a limited number of screenshots when necessary and solely for verification and documentation purposes. I do not engage in any activities beyond identifying the security vulnerability and, where possible, notifying the relevant parties involved. I disclaim any and all liability for any and all actions that may be taken as a result of this disclosure. I publish my findings to raise awareness of issues of data security and privacy. My aim is to encourage organizations to proactively implement measures to safeguard sensitive information against unauthorized access.