On March 3rd, 2021 security researcher Jeremiah Fowler and the Website Planet research team discovered a non-password protected Elasticsearch database that contained just under a million records. The exposed records were labeled as “Production” and contained customer names, phone, physical addresses and more. The monitoring and file logs exposed many internal records that should not have been publicly accessible.
There were multiple references to Office Depot in a large sampling of the records. We immediately sent a responsible disclosure to Office Depot and the database was secured within hours. On March 5th we received a reply from a team member with the Security Operations team at Office Depot Europe thanking us for the notification and raising awareness to the data exposure.
This leak could have provided enough information for cyber criminals to target customers with a social engineering attack or try to gain access to the accounts.
What the Database Contained:
- Total Records: 974,050
- The types of indices exposed included: monitoring-kibana,
Apm-metric, filebeat, heartbeat logs. - There were many references to “Officedepot” in the dataset such as host name, IP addresses, and pathways indicating the server was theirs.
- Among the data exposed were *SSH Login information , dashboard and user group logs of internal employees, as well as European customer records with most referencing Germany.
*(SSH enables a secure connection to a server or remote machine) - The records were labeled “Production” and contained customer PIIs such as names, phone numbers, physical addresses (home and/or office), @members.ebay addresses, and hashed passwords. The leak also exposed Marketplace logs and order history, exposing the customers’ past purchases and costs.
- The database was at risk of ransomware or other malicious attacks.
- Middleware or build information that could allow for a secondary path for vulnerabilities. (Middleware connects third party software applications, and outdated or unpatched middleware can be a backdoor into the network). More technical records included IP addresses, Ports, Pathways, and storage info that cyber criminals could exploit to access deeper into the network.
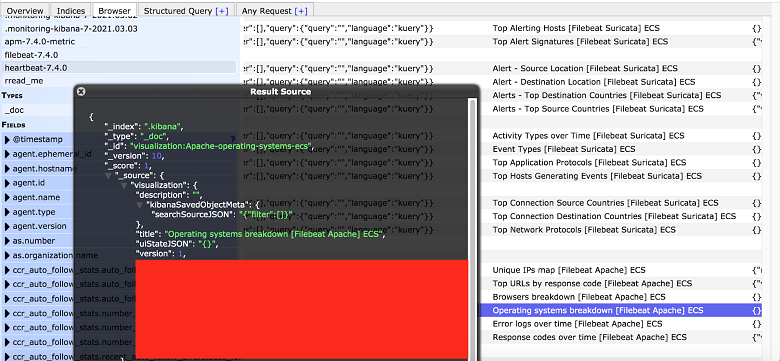
The records exposed detailed information about the inner workings of the network. This screenshot shows an “Operating System Breakdown” and would give a potential attacker a clear understanding of how to exploit known vulnerabilities or other intrusive methods.

Privacy Implications
Any unwanted data leak poses a potential risk to customers and the exposed internal network. There is always a real possibility of bad actors stealing information and using it for fraudulent purposes. These records were accessible to anyone with an internet connection.
Note: We never download or extract the data that we find and only take several screenshots for verification purposes. We redact any potentially sensitive information to protect the privacy of users or customers.
All records that contained PII were based in the European Union and many referenced Germany. In the EU there are very clear data protection rules and financial penalties. On May 25th, 2018 the EU passed the General Data Protection Regulation (GDPR). This change allowed data protection regulators the ability to impose high fines and strict reporting guidelines. The highest fine amount is a maximum of €20 million or 4% of the global annual turnover of a business, whichever is the higher. Data exposures in the EU must be reported in 72 hours to the proper authorities.
Best Practices and Risks
Apart from recommending to properly configure any server you own in order to limit access to it, we recommend that all data should be encrypted. Companies and organizations continue to collect and store sensitive data in plain text or use outdated encryption algorithms. One of the biggest mistakes is to encrypt the records but include the encryption keys in the same database. This would allow anyone to simply unlock the data and have full access to these records.
Managing vulnerabilities requires active patch management and updates. Keeping applications and middleware up to date is crucial in the ever-changing security landscape and represents one of the most effective means of mitigating these risks. Neglecting older builds and outdated software can result in the emergence of critical vulnerabilities.
Never underestimate the value of monitoring and error logs. The real risk for log files is that they can expose small pieces of data that collectively serve as puzzle pieces to create a larger picture of the network. This can include details about middleware that can be targeted as a secondary pathway for malware, operating systems, or even pathways to cloud storage accounts. Once cyber criminals or nation state hackers understand how the network or infrastructure is built and operates it is easy to launch a plan of attack. We are not implying that Office Depot Europe or their customers were targeted in this form of attack but only highlighting the potential risks of how this kind of exposure could be exploited.
In this case there were many internal records that should have not been publicly exposed. When personally identifiable information (PII) is exposed it simplifies the ability to target those individuals. Once a cyber criminal has this information they can directly target customers or employees and reference account specific information. As an example, let’s hypothetically say a criminal calls the customer and they validate the recent order. Next the criminal says something is wrong with your billing information can you please provide me with the credit card number used for your purchase? The customer would have no reason to doubt this because the caller can validate real details that only the retailer would know. This is how a social engineering attack works and it is one of the most common forms of fraud used today.
Physical Stores to Ecommerce
Office Depot Europe is the European business of the U.S. company Office Depot Inc. In Jan 2017 AURELIUS Group acquired the European operations of Office Depot. Headquartered in Venlo, Netherlands, Office Depot Europe operates in 13 countries through its two main brands, Office Depot and Viking, with retail stores in France and Sweden. Office Depot Europe sells its products directly to small and medium-sized businesses and private individuals online, and under the Viking brand name.
It appears that many of these records were connected to Office Depot’s eBay store. There were customer names, phone numbers, physical addresses, @members.ebay.com accounts and hashed passwords. This included customer types such as B2C (business to customer) or B2B (business to business), online customer numbers and backend customer numbers.
Office Depot Europe acted fast and professionally to secure the data and restrict public access. It is unclear how long the data was exposed or who else may have had access to the records. According to the Binary Edge IoT search engine the exposed port was first detected: 2/22/21 at 10:31 AM. This would indicate the possibility that the database was misconfigured to allow public access for as long as 10 days. It is nothing short of a miracle that the data was not destroyed by automated ransomware or other malicious scripts that target non-password protected databases.