Security Researcher Jeremiah Fowler in cooperation with the WebsitePlanet research team discovered a non-password protected database that contained 92 million records. Upon further investigation it appeared to belong to the Cronin digital marketing agency. The exposed server was named “Cronin-Main” and many of the records contained references to Cronin. These records included internal data such as employee and client information. Also included in the dataset was a “Master Mailing List” with direct physical names, addresses, Salesforce IDs, phone numbers, and references to where the leads came from.
The Connecticut based agency has some very well known clients listed on their website. According to Cronin’s website they are “digitally driven, results-focused marketing agency that’s propelled by technology. Client focus: financial, healthcare & consumer products/services”. In a press release dated March 16, 2020, Horizon Group of North America has acquired Cronin, Connecticut’s largest independent full-service marketing agency. Their clients list includes companies such as Dunkin, Lego, Henkel, Loctite to mention a few
Here is what was discovered:
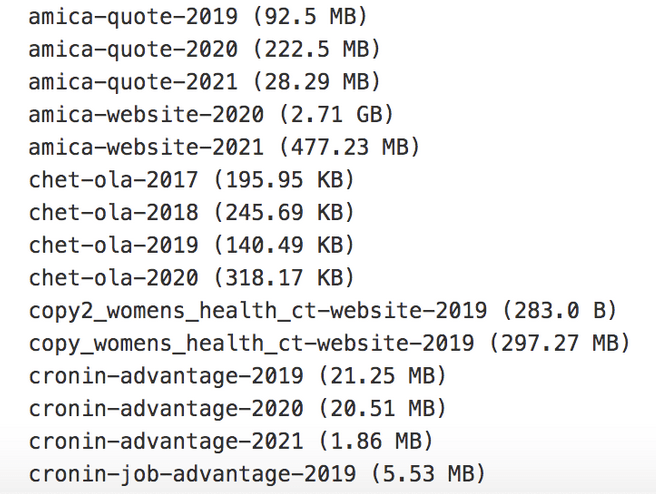
- Total Size: 26.43 GB / Total Docs: 92,711,060
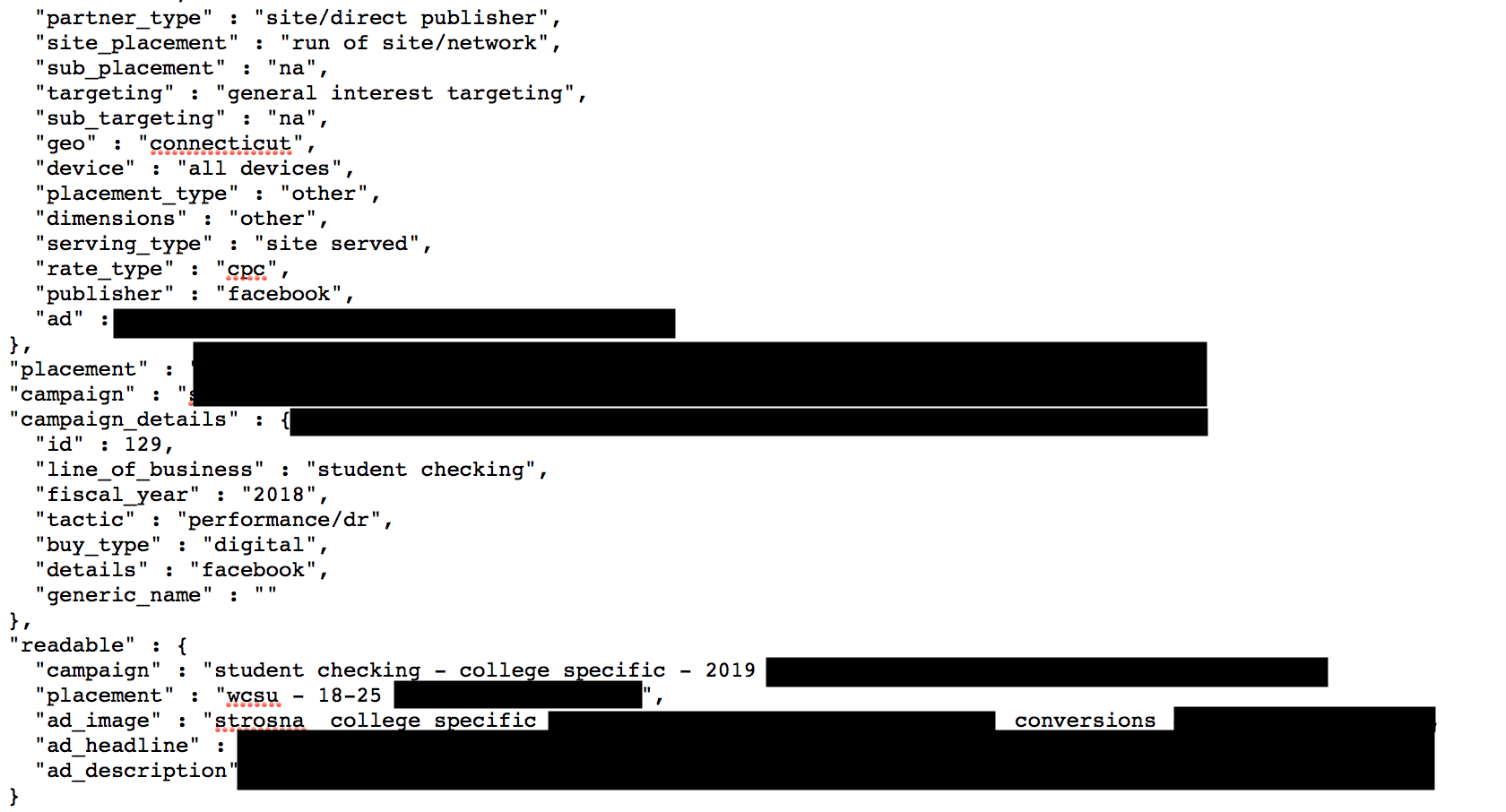
- Exposed records that contained internal logging of client advertisement campaigns, keywords, Google analytics data, detailed information such as session ID, Client ID, device data and other identifying information.
- Login tokens and other security information.
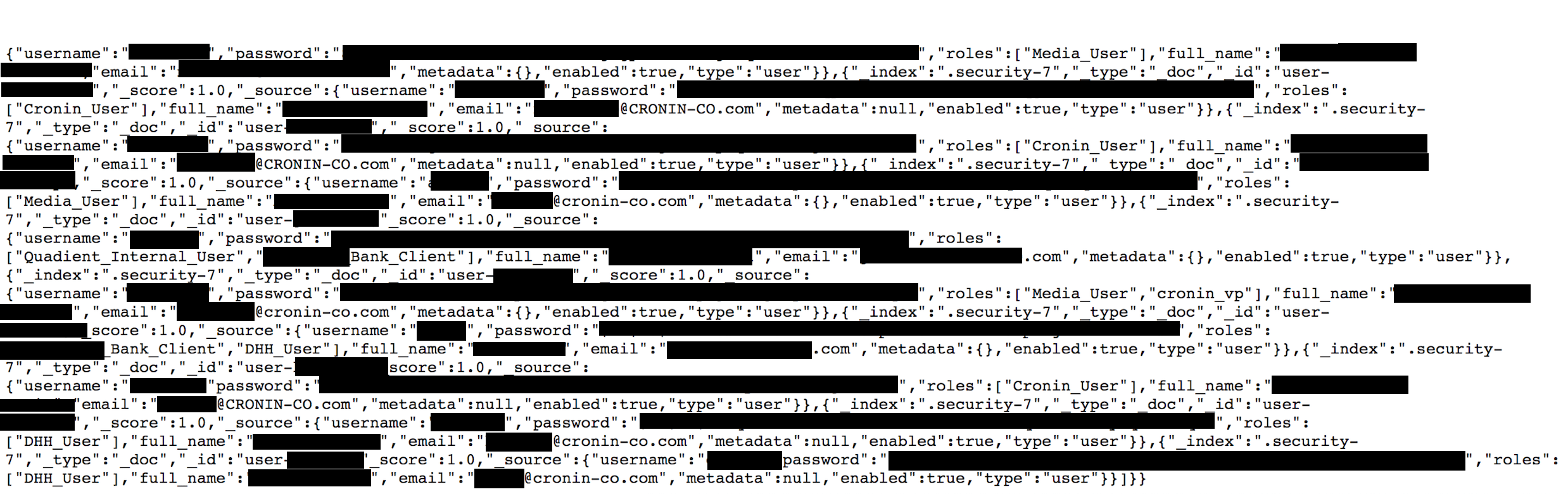
- Internal Cronin employee usernames, emails, and hashed passwords that could be potentially targeted in a phishing attack or used to access restricted areas of the network or password protected records.
- Employee and financial records in the following format: bill_rate”,”department”:”digi”,”department_code”:”technology & innovation”, and other internal recording or logging formats.
- The exposure shows where data is stored and serves as a blueprint of how the service operates from the backend.
- Middleware or build information that could allow for a secondary path for malware. IP addresses, Ports, Pathways, and storage info that cyber criminals could exploit to access deeper into the network that should not be public.
- This is a database set to open and be visible in any browser (publicly accessible) and anyone could edit, download, or even delete data without administrative credentials.
The downside of technology is that with digital records and cloud storage also comes the increased risk of a data incident or exposure. For companies who work in the digital sphere the cyber security threat landscape evolves daily. Any organization that relies on technology and data as the core of their business must take extra steps to secure the digital records they collect and store online. In this case anyone with an internet connection could have gained access to a massive amount of records.
I immediately sent a responsible disclosure notice on March, 6th 2021 to multiple contacts including those found inside the records. On March, 11th I followed up again after noticing that the database was still publicly exposed. This time I spoke with someone by phone who informed me that they were aware of the incident and that it was being taken care of. The following day the database was secured. It is unclear how long the database was exposed or who else may have gained access to Cronin’s records. We are not implying that any of Cronin’s employees or clients were ever at risk and we are only highlighting the facts of our discovery to raise awareness of any potential cyber security vulnerabilities.
The Risk Of This Kind of Exposure
Cyber criminals are always looking to exploit the data they find. Having inside knowledge of a business relationship could potentially put employees and clients at risk of a social engineering attack or targeted spear phishing attempt. Hypothetically there could have been enough information to engage in a Man-in-the-middle attack or (MITM) where an unauthorized third party intercepts or gains access to transactions between two parties. For example if an invoice is due they would see the date, amount, and if the invoice was paid or owed. Next the criminal would request payments to their own account instead of the company’s account. They could simply call or email and say “we have updated our banking information, please pay your outstanding balance to the following account number”. They could provide invoice numbers, or other internal account information that only the service provider would have. The client would have no reason to suspect anything and the money would be gone. This happens far more than people think and it often goes unreported unless the amount is too large to ignore.
The size of the digital marketing agency market in 2021 is estimated to be a $17.2 billion business in the US alone. Many competitors would love to see how a rival business operates from the backend. Analytic data is a secret ingredient to any company’s sales success. What tools or applications are they using? What are the views, click rates, sales, and more? This exposure painted a very clear picture of where ads were being delivered, costs, where lead data comes from, and other important details.
Businesses have engaged in corporate espionage for as long as they have existed, and companies take extensive measures to safeguard the specifics of their service provision. In this case, the front door remained locked, while the back door was left wide open, granting unrestricted access to a vast trove of data and analytical information.
As security researchers we never download or extract the data we find and our goal is to protect and secure exposed records before they can be exploited. This is yet another wakeup call that the digital marketing and advertising industry must do more to protect the data they collect and store. Having a dedicated team to manage data security is an important step. We understand that not all companies can afford a big security budget, but they can easily create a communication channel for reporting data incidents or educate customer support on how to manage outside data security notices. Far too often we see data exposures where it is difficult to report the incident because key leadership is hidden behind a firewall. This creates a delay in securing the data and adds additional risks that the information will be compromised or destroyed by ransomware.
We are not implying any wrongdoing by Cronin Group Holdings, LLC, their partners or affiliates. We are also not implying that clients or customers were at risk. We are only highlighting our discovery to raise awareness of cyber security best practices and data protection.