Potential risks of the exposure
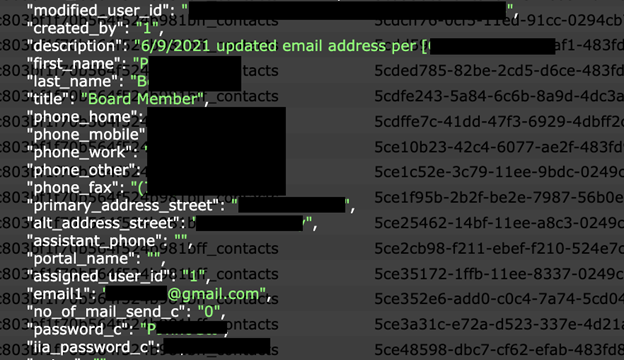
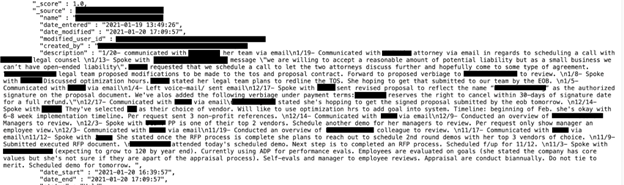
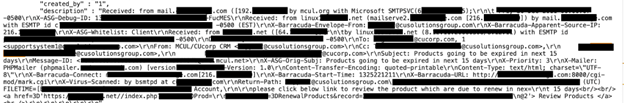
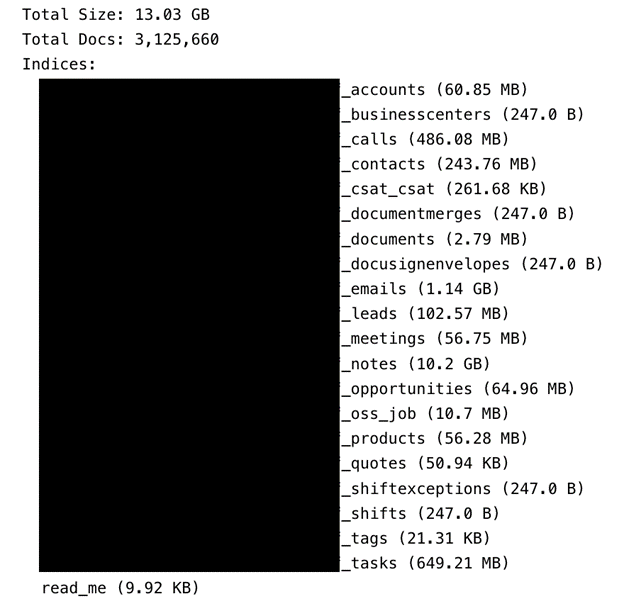
In 2022, the average cost of a data breach in the financial industry was nearly six million USD, second only to the healthcare sector, which was nearly 11 million USD. With financial gain being the goal of most cybercrimes, it is clear to see why financial institutions and their customers could be a serious potential target. Overall, in the United States, consumers reported losing a cumulative $8.8 billion to fraudulent scams in 2022 — a 30% increase from the previous year, according to the Federal Trade Commission (FTC). Any data breach involving a technology service provider for credit unions could potentially pose significant risks to both the financial institutions and their members. Although I didn’t see individual customer records of credit union members in the exposed database, I did see contacts, communications, and other related data of board members and the leadership of a large number of credit unions. It is unknown if anyone else accessed these exposed records. In the dubious world of cyber crime, exposed internal data could be a stepping stone to try and identify a vulnerability or backdoor into the network of a financial institution. Exposed passwords could hypothetically allow unauthorized access to the accounts and any documents or information stored there. The potential risks of a massive number of email addresses being publicly exposed include a low-tech phishing campaign, distribution of malware, or simple spam emails. Exposed email server communications, pathways, and IP addresses can hypothetically pose even more serious risks and various cybersecurity threats or vulnerabilities. If the email server communication channels are unencrypted or inadequately protected, technical attackers could potentially intercept data and other sensitive information. Exposed email server configurations or outdated software may become vulnerable and increase the likelihood of potential data interception by unauthorized cybercriminals. When IP addresses associated with email servers are publicly exposed, they could potentially enable cybercriminals to spoof or impersonate legitimate servers, allowing them to send fraudulent emails that appear to come from trusted sources. This tactic (known as “IP spoofing”) can be used in a wide range of malicious activities. I am not saying or implying that CUSG or their clients are at imminent risk of this type of attack. I am only providing a hypothetical real-world scenario of the potential risks of a public exposure of internal email server data. Any data breach or unauthorized access of a CRM system can have serious potential security risks for the organization or their clients. Organizations and financial institutions that collect and store potentially sensitive data in a CRM system should implement multiple layers of security measures to safeguard their data. I highly recommend:- Updating the CRM software to the latest version as it becomes available. The latest software version can include things such as security patches and fixed known vulnerabilities.
- Having strong access controls and role-based permissions. It is important to ensure that only authorized personnel can access sensitive data within the CRM and any other database where records are stored.
- Encrypting data is also a good way to get an additional layer of protection. If encrypted data is exposed, it is far less likely to be decrypted and used for nefarious purposes.
- Doing regular security audits and penetration testing. This can help an organization identify exposed data or potential vulnerabilities (including human errors).