- Access Logs: Record information about requests made to the server, including details like IP addresses, requested resources, HTTP methods, and status codes.
- Error Logs: Capture information about errors and issues encountered by the server, helping administrators identify and resolve problems.
- Security Logs: Contain information related to security events, such as failed login attempts, authentication failures, and other security-related incidents.
- System Logs: Cover a broad range of system-level events, including startup and shutdown sequences, hardware and software errors, and other system-related activities.
Exposed Customer Data
Any data exposure of customer information poses a potential threat to the confidentiality and privacy of clients. Information such as names and emails of authorized individuals, billing administrators, or account representatives could be potentially useful for targeted phishing attacks or other forms of fraudulent activities. For instance, some of the records in the exposed database indicated the name of what appeared to be the dedicated salesperson within Zenlayer assigned to each specific account. Hypothetically, in a social engineering or phishing attack, a cyber criminal could contact the customer posing as the Zenlayer salesperson and ask for payment or banking information. Customers of any organization should only use official channels when providing sensitive financial information and always verify any suspicious requests. Among the customer records I saw a company which has been described as a leading provider of international capacity for telecom carriers in Russia. Registration and filing documents indicate the company is partially owned by a sanctioned Russian state controlled company. Certain telecom providers linked to the Russian government have been allegedly involved in internet traffic hijacking, also known as BGP (Border Gateway Protocol) hijacking. The BGP is the protocol that Internet Service Providers (ISPs) and other network operators use to inform each other about the optimal paths for routing traffic between different IP addresses. A BGP hijacking involves an attacker announcing false BGP route information to the internet, causing traffic to be rerouted through the attacker’s network. This can have serious consequences, as it allows the attacker to intercept, inspect, or modify the traffic passing through their network. The motivations behind BGP hijacking can vary. Some attackers may engage in BGP hijacking for espionage, intercepting sensitive information flowing through the rerouted traffic. Others may do it for financial gain, such as redirecting cryptocurrency transactions or launching man-in-the-middle attacks. I am not claiming this company or any other Zenlayer customers are engaged in BGP hijacking. I am only identifying a real-world hypothetical scenario of how state actors or cybercriminals could capture and analyze internet traffic using the exposed traffic information or legitimate services.Access and Secret Keys
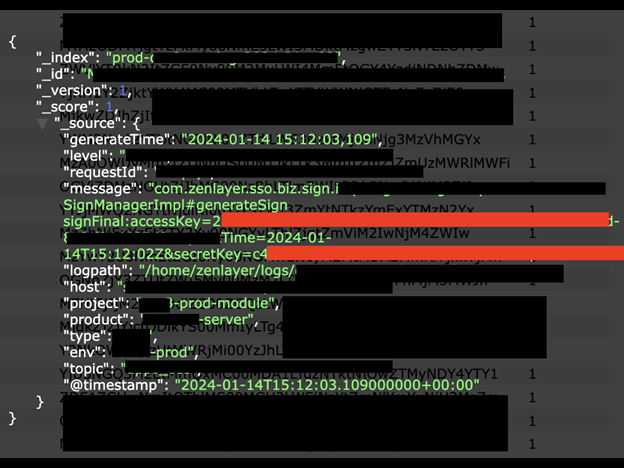
Similar to how keys open doors in the real world, digital keys can open folders, files, and documents. Any exposure of access and secret keys can pose significant risks to the affected individuals, organizations, and their assets. Access and secret keys are often used for authentication and authorization in various systems, services, and applications. When these keys are compromised, it can lead to a range of potential risks. Compromised access and secret keys may enable attackers to retrieve, download, or manipulate sensitive data stored in databases, file storage systems, or other repositories.Zenlayer Internal Emails
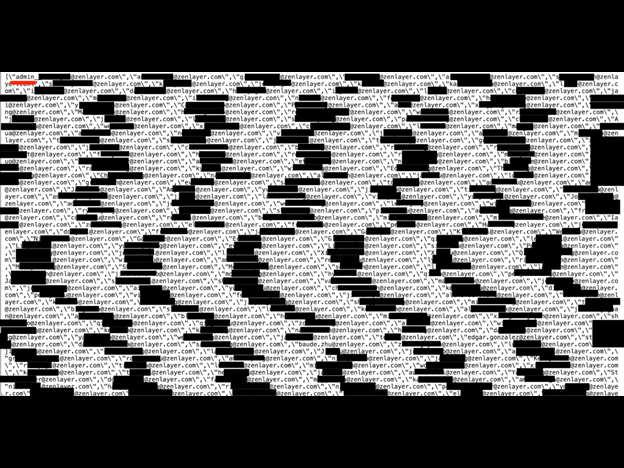
Any data breach that exposes internal company email addresses and user roles could pose a significant potential risk. I was able to search and identify the email accounts of senior leadership and their associated internal ID numbers using only an internet browser. The disclosure of hundreds or thousands of internal email addresses could potentially assist cybercriminals in launching targeted phishing attacks or social engineering attempts with the goal of obtaining unauthorized access to sensitive information or systems. In particular, exposure of user roles such as an administrator would allow malicious actors to exploit privileged access, manipulate critical settings, and potentially compromise the entire infrastructure. In an email phishing campaign against a company employee, the attacker typically sends a deceptive email appearing to be from a trusted source, such as the employer or a colleague. The email from the criminal could aim to trick the employee into clicking a certain link, downloading a malware-ridden attachment, or visiting a malicious website. By doing so, the employee could inadvertently reveal sensitive information, unwittingly install malware, potentially enable the attacker to gain unauthorized access, or compromise their own credentials. I am not implying that Zenlayer’s employees or leadership are at risk of this type of cyber threat. I am only identifying the real world risk of how exposed internal email accounts could potentially be used by cybercriminals if the data fell in the wrong hands. This analysis is meant to highlight general cybersecurity concerns and is not indicative of any specific vulnerabilities within Zenlayer or any specific organization.VPN Records
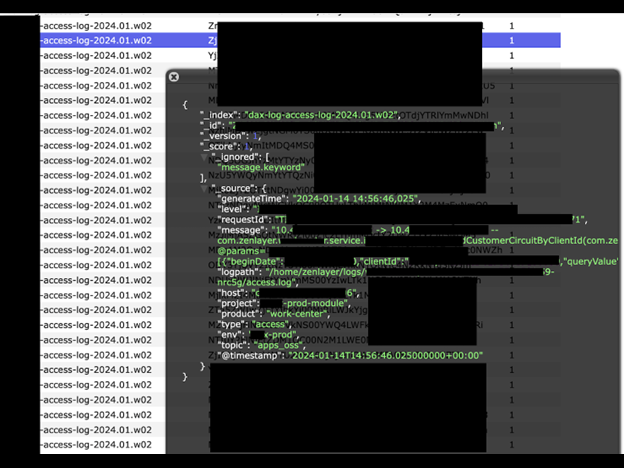
I also saw logs indicating VPN (Virtual Private Network) records and numerous IP addresses. The VPN logs were labeled as controller host IP, controller IP, IP LAN, jumper IP, PXE IPMI, among others. Here is what these terms probably refer to, given the context:- Controller: In networking, it can refer to a device or software component that manages and coordinates the activities of other network elements. In the context of a VPN, this could potentially be a central device responsible for orchestrating VPN connections, managing encryption keys, or overseeing the overall operation of the VPN infrastructure.
- Jump host: It typically refers to an intermediary server that is used as a gateway to access other servers or devices within a network.
- PXE IPMI: In the context of a VPN, the term typically refers to the combination of PXE (Preboot eXecution Environment) and IPMI (Intelligent Platform Management Interface) technologies within a network.

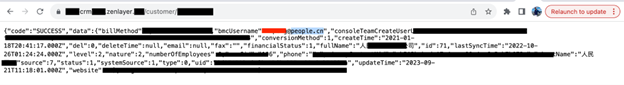
Customer Accounts Exposed on Subdomain
Two days after notifying Zenlayer about the exposed database, I noticed a second potential vulnerability involving a subdomain on Zenlayer’s website. It identified customers, disclosing their information in a URL format that could be viewed in any browser. The customer numbers run in chronological order and could be seen by simply changing the number such as customer/001, customer/002, customer/003, etc. This was not a database but a web base listing of Zenlayer’s users in a plain text html format. Each of these records indicated the customer’s email, phone number, ID number, billing method, name of the business, and number of employees. I sent Zenlayer another responsible disclosure notice as soon as I saw the subdomain, but it also went unanswered.