What Is Invoice Fraud?
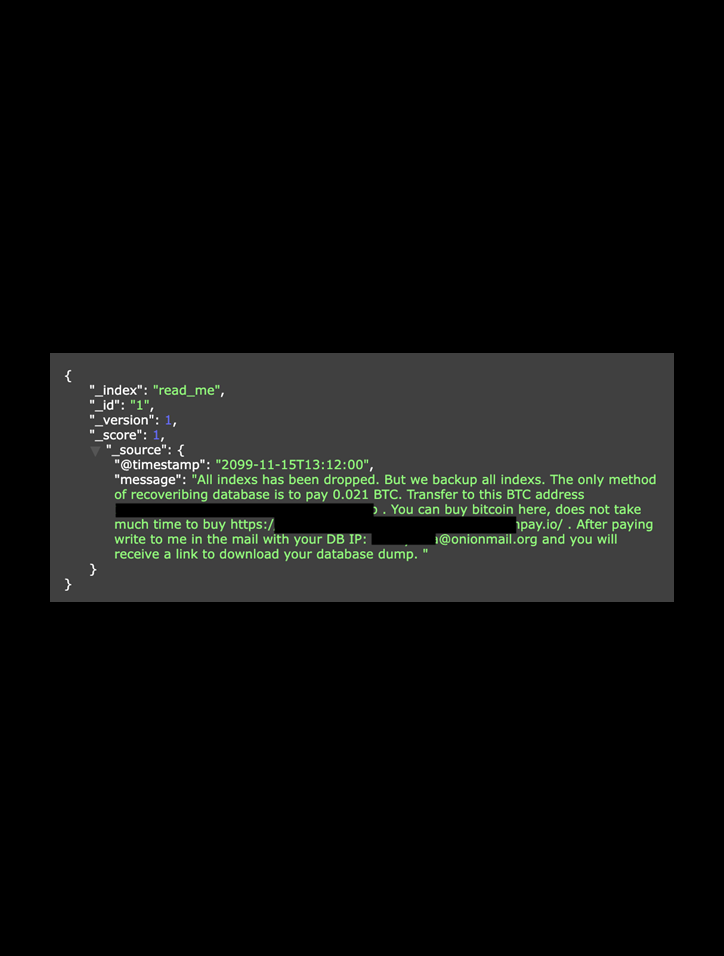
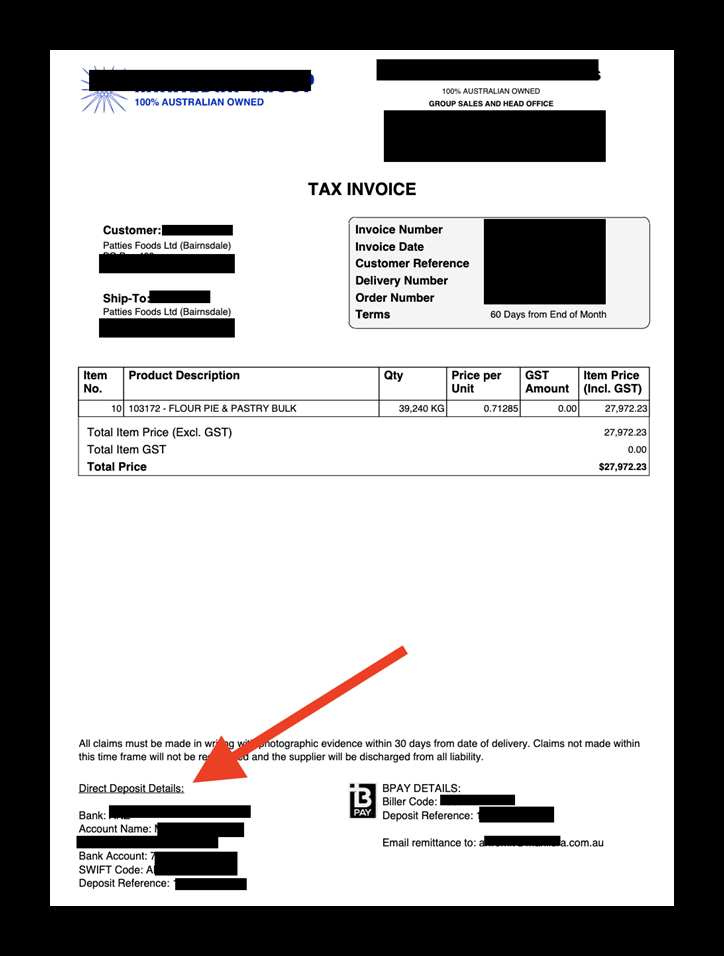
Invoice fraud involves the creation, alteration, or manipulation of invoices with the intent to deceive and defraud businesses. Criminals could potentially exploit invoices exposed in a data breach for financial gain by using non-public internal information such as billing details, payment terms, contact information, and other details to launch various fraudulent schemes. For example, using an exposed invoice as a template, the criminal could hypothetically alter legitimate invoices to redirect payments to accounts owned and operated by the criminals. Using real data from invoices, criminals could also impersonate legitimate vendors and issue false invoices for products or services that were never provided. By exploiting the position of trust a company has with their vendors, criminals could potentially deceive a business into making unwarranted payments. Using real data that only the company and vendors would know significantly increases the chances of a successful invoice fraud attack, as the targets would have little reason to doubt the legitimacy of the document. This type of fraud can lead to significant financial losses for organizations, regardless of size. In this case, the invoices were uploaded to the database and updated in real-time with a timestamp. Hypothetically, criminals could simply monitor the exposed database for new invoices. Once a new invoice appears, they could download it, modify the payment details to the criminal’s bank account, and then replace the legitimate invoice with the fraudulent version. With a company as large as Patties Foods and so many vendors, it would probably be a time-consuming task to validate or verify the number of monthly invoices being processed. This means a hypothetically higher chance of the fraudulent invoice going unnoticed until after it is paid. The Australian Cyber Security Centre (ACCC) issued an advisory on April 4th urging citizens to beware of invoice scams where criminals send victims altered payment requests. The advisory also indicates that, in 2023, Australians reported losing $16.2 million to payment redirection scams. Although the advisory was addressed to citizens, the same risks apply to companies, whose losses could be much greater. I am not saying that Patties Foods or any of its vendors are at risk of invoice fraud, I am only providing a real-world scenario to raise awareness of how the exposed documents could be used by criminals.Additional Potential Risks
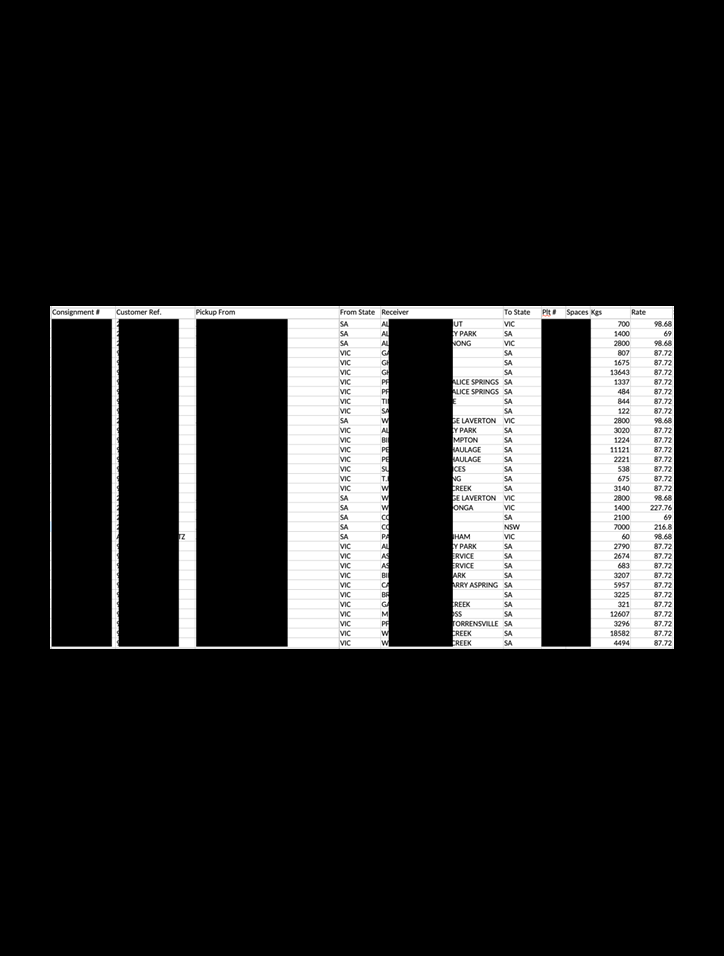
In addition to the exposed invoices, the database also contained Jira tickets identifying support requests, technical issues, and communications between Patties Foods and Provenio. These communications identified problems with invoices and solutions, service issues or other information that could potentially be misused for fraud or for malicious actors to exploit identified system vulnerabilities. Jira is a project management software used by companies to track and manage their activities. It provides teams with tools for task tracking, issue management, collaboration, and workflow automation. It is also a useful tool for service support. In this case, the records were stored and managed by the end user, and the exposure is no fault of the Jira software. In the database, there were also spreadsheets and invoices containing fleet and transportation information, such as details of the vehicle, pallet numbers, billing and invoice totals. In addition to contact information for food vendors and suppliers, the fleet or delivery service documents could potentially provide criminals with additional inside information that could be exploited for fraudulent activities, such as impersonating an employee. Any exposure of supplier and vendor invoices in a data breach underscores the critical importance of safeguarding sensitive information required for normal business operations. I recommend that companies take proactive measures to protect themselves from invoice fraud and be vigilant to the common tactics of cyber criminals. Here are a few basic tips that could help prevent invoice fraud:- Implement verification procedures to ensure the authenticity of invoices and the legitimacy of vendors. Adding extra layers of security is time-consuming, but even when companies use automation to save time and resources, it is important to apply human logic to identify suspicious activity. Verify vendor contact information using official communication channels, and cross-reference invoice and payment details with purchase orders and contracts to ensure they have not been altered or changed.
- Enforce dual authorization within your accounts payable or finance department to ensure that no single individual has sole control over the entire invoicing and payment process. Requiring two separate individuals to review and sign off on financial transactions can reduce the chances of criminals successfully carrying out a fraudulent scheme. This way, if one account is compromised or a modified invoice goes unnoticed at first, the transaction will hopefully be identified by the second person needed for the approval.
- Raise awareness and train employees to recognize common red flags of invoice fraud, such as discrepancies in billing details, unusual payment requests, or changes in vendor contact information. It is also important to provide dedicated communication channels for employees to report suspicious activity or concerns before a suspicious payment is approved.
- Regularly review financial records to identify any discrepancies or anomalies that may indicate potential fraud. Although it may be difficult to reverse a fraudulent transaction once it has been identified, it can prevent additional payments from going through. Reviewing vendor accounts and payments regularly decreases the chances of unauthorized transactions or other irregularities taking place.
- Including strong encryption protocols to protect sensitive data that may be used by an application, user dashboard, or storage repository. Encrypting all data ensures that even if records are intercepted or accidentally exposed, those files will be unreadable and virtually worthless to criminals.
- Using strong access controls and authentication mechanisms, such as multi-factor authentication. These steps can help prevent unauthorized users from gaining access to critical systems or data.
- Running regular security audits and penetration testing can identify vulnerabilities proactively, including open ports, misconfigured firewalls, and publicly exposed cloud storage databases.
- Providing cybersecurity training for all employees can help identify potential threats and mitigate human errors — even if security is not in their job titles. Cyber threats change often, so companies need to take basic steps to secure their data and stay a step ahead of criminals who are actively looking to exploit all types of vulnerabilities for financial gain.